Although VMware provides a KB article on how to request and install a new SSL certificate for VMware View 5.0’s Security Server, sometimes I wished it there was a GUI available to do it because I find that I always forget the steps after a few months. After having to read the KB article again after a few deployments, I’ve decided to write this blog post so I have something to reference to in the future. First off, the following is the link to VMware’s KB article:
Guidelines for generating and importing an SSL certificate for the View Connection Server
http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=1008705
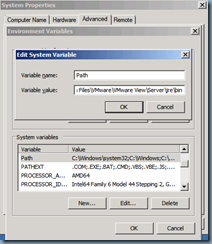
Begin by logging onto your Security Server’s Windows Server 2008 R2 operating system and open up the System Properties window, navigate to the Advanced tab and then click on Environment Variables:
Highlight the Path line item under System variables and click on the Edit button:
The path we need to add is as follows:
<install_directory>\VMware\VMware View\Server\jre\bin
Note that you should not mistaken this the path above for the path below:
C:\Program Files\VMware\VMware View\Server\bin <—WRONG
… for this:
C:\Program Files\VMware\VMware View\Server\jre\bin <—Right
Note the keytool.exe executable:
Append the path C:\Program Files\VMware\VMware View\Server\jre\bin to the Variable value: field:
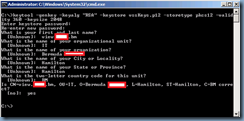
Once that path has been entered, open up the command prompt as an administrator and change the directory to the directory of your choice and then execute the following:
keytool -genkey -keyalg "RSA" -keystore vssKeys.p12 -storetype pkcs12 -validity 360 -keysize 2048
Note that you vssKeys.p12 is a user specified file so it’s up to you as to what you want to name the key. Proceed with filling out the fields and make sure you make a note of the password as you’ll be using it afterwards. For the purpose of this example, I’m going to use the password P@ssw0rd.
Once you’ve completed answer all of the questions, you’ll notice that a file named vssKeys.p12 is created in the working directory:
Note that this file is not a clear text file so if you open it, you’ll see the following content:
From here, switch back to the command prompt and type the following:
keytool -certreq -keyalg "RSA" -file viewbm.csr -keystore vssKeys.p12 -storetype pkcs12 -storepass P@ssw0rd
Note that the file viewbm.csr is a user specified filename so name as anything you prefer.
Once the command completes, you should now see a csr file in the working directory:
This csr file is the typical request file containing text that you submit to your CA:
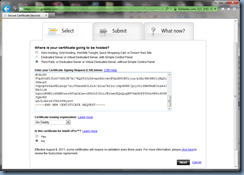
Switch to your GoDaddy certificate services console and select Third Party, or Dedicated Server or Virtual Dedicated Server, without Simple Control Panel then paste the CSR request into the window:
Proceed with submitting the request:
Once you have approved GoDaddy to issue the certificate, navigate back to their console and download the certificate:
As per VMware’s KB:
Importing external Godaddy.com certificates
http://kb.vmware.com/selfservice/microsites/search.do?cmd=displayKC&docType=kc&docTypeID=DT_KB_1_1&externalId=1004836
… proceed with downloading the certificate for a Tomcat server:
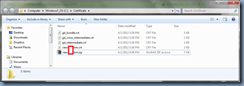
Once you get the certificate downloaded, proceed with unzipping them:
Proceed with opening the .crt file with Crypto Shell Extensions:
Once the certificate opens, click on the Details tab:
In the Details tab, click on the Copy to File button:
The Certificate Export Wizard will now open:
Change the radio button from DER encoded binary X.509 (.CER):
… to Cryptographic Message Syntax Standard – PKCS #7 Certificates (.P7B) and select Include all certificates in the certification path if possible checkbox:
Enter a name for the .p7b file:
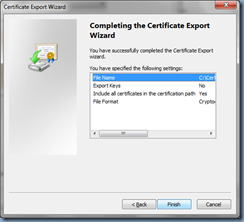
Proceed with exporting the file:
With the .p7b file in the same directory as the vssKeys.p12, open the command prompt as an administrator ane execute the following:
keytool -import -keystore C:\vssKeys.p12 -storetype pkcs12 –storepass P@ssw0rd -keyalg "RSA" -trustcacerts -file view.p7b
Once the command successfully executes, proceed with copying the vssKeys.p12 file to the following directory:
C:\Program Files\VMware\VMware View\Server\sslgateway\conf\
Create a file named locked.properties:
Edit the file and put in the following as shown in the screenshot:
keyfile=vssKeys.p12
keypass=P@ssw0rd
Restart the VMware View Security Server service:
Once the service restarts, navigate to the Security Server’s webpage and verify that the certificate has been installed.






























2 comments:
THANK YOU!!!!!!!!
Hi Guys! Please help. I was almost finish and i got the error below.
C:\>keytool -import -keystore C:\cer\viewxxx\vssKeys.p12 -storetype pkc
s12 -storepass xxxdomain! -keyalg "RSA" -trustcacerts -file viewdeltafundcom.p7
b
keytool error: java.lang.RuntimeException: Usage error, ûstorepass is not a lega
l command
Post a Comment