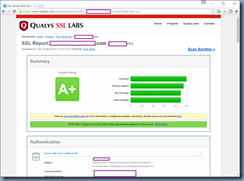
I’ve received quite a few requests from clients over the past few months requesting to secure their NetScaler published services to score an A+ on Qualys SSL Labs:
https://www.ssllabs.com/ssltest/
I’m a bit late to writing this blog post as there are plenty of other excellent posts that demonstrate the process so in an effort to add a bit more value to the community, this post will demonstrate the process on a NetScaler VPX NS11.0 63.16.nc via the command line.
Without any additional configuration, NetScaler published services such as Citrix XenApp/XenDesktop typically scores a C:

Note that the following vulnerabilities exist as shown in the screenshot above:
- SSL 3 enabled
- No support for TLS 1.2
- Server accepts RC4 cipher, but only with older protocol versions
- Server does not support Forward Secrecy with the reference browsers
Step #1 – Turn off SSLv3 and enable TLSv11 + TLSv12
The first step is to turn off SSLv3 and enable TLSv11 and TLSv12 on your Load Balancing Virtual Server(s) and NetScaler Gateway Virtual Servers.
The following screenshots shows where the settings are in the GUI for the Load Balancing Virtual Server named StoreFront-lbvip:


The command to execute are as follows:
set ssl vserver StoreFront-lbvip -ssl3 disabled
set ssl vserver StoreFront-lbvip -tls11 enabled
set ssl vserver StoreFront-lbvip -tls12 enabled

With the commands above executed, the protocols should now be displayed as such:

Repeat the same process for the NetScaler Gateway Virtual Servers.
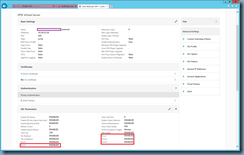
The following screenshots shows where the settings are in the GUI for the NetScaler Gateway Virtual Servers named www.contoso.com_external and www.contoso.com_internal :

The command to execute are as follows:
set ssl vserver www.contoso.com_external -ssl3 disabled
set ssl vserver www.contoso.com_external -tls11 enabled
set ssl vserver www.contoso.com_external -tls12 enabled

With the commands above executed, the protocols should now be displayed as such:
Step #2 – Create new custom Ciphers
The set of SSL Ciphers will allow us to score an A+ SSL scan on a NetScaler VPX appliance:
- TLS1-ECDHE-RSA-AES256-SHA
- TLS1-ECDHE-RSA-AES128-SHA
- TLS1-DHE-RSA-AES-256-CBC-SHA
- TLS1-DHE-RSA-AES-128-CBC-SHA
- TLS1-AES-256-CBC-SHA
- TLS1-AES-128-CBC-SHA
- SSL3-DES-CBC3-SHA
Execute the following to create a group named Custom-VPX-Cipher with the ciphers listed above:
add ssl cipher Custom-VPX-Cipher
bind ssl cipher Custom-VPX-Cipher -cipherName TLS1-ECDHE-RSA-AES256-SHA
bind ssl cipher Custom-VPX-Cipher -cipherName TLS1-ECDHE-RSA-AES128-SHA
bind ssl cipher Custom-VPX-Cipher -cipherName TLS1-DHE-RSA-AES-256-CBC-SHA
bind ssl cipher Custom-VPX-Cipher -cipherName TLS1-DHE-RSA-AES-128-CBC-SHA
bind ssl cipher Custom-VPX-Cipher -cipherName TLS1-AES-256-CBC-SHA
bind ssl cipher Custom-VPX-Cipher -cipherName TLS1-AES-128-CBC-SHA
bind ssl cipher Custom-VPX-Cipher -cipherName SSL3-DES-CBC3-SHA

With the above commands successfully executed, we should now see the following Cipher Group created:

Step #3 – Bind new custom Ciphers to Load Balancing Servers
With the new cipher group created, proceed with binding them to the Load Balancing Virtual Server(s) and NetScaler Gateway Virtual Server(s):
bind ssl vserver StoreFront-lbvip -cipherName Custom-VPX-Cipher
bind ssl vs StoreFront-lbvip -eccCurveName ALL
bind ssl vserver www.contoso.com_external -cipherName Custom-VPX-Cipher
bind ssl vs www.contoso.com_external -eccCurveName ALL
bind ssl vserver www.contoso.com_internal -cipherName Custom-VPX-Cipher
bind ssl vs www.contoso.com_internal -eccCurveName ALL
----------------------------------------------------------------------------------------------------------------------------------------------
Note that I’ve found the binding process a bit finicky at times and had to unbind the cipher groups so if this is necessary, use the following commands:
unbind ssl vserver StoreFront-lbvip -cipherName DEFAULT
unbind ssl vserver www.contoso.com_external -cipherName DEFAULT
unbind ssl vserver www.contoso.com_internal -cipherName DEFAULT
----------------------------------------------------------------------------------------------------------------------------------------------
With the new cipher group binded to the virtual servers, we can use the following commands to review the bindings:
show ssl vserver StoreFront-lbvip
show ssl vserver www.contoso.com_external
show ssl vserver www.contoso.com_internal



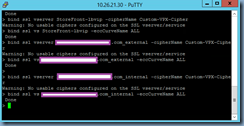
Note that navigating to the ciphers binding in the GUI may throw the following warning:
No usable ciphers configured on the SSL vserver/service

I’ve done a bit of research on this and it appears we can safely ignore it.
Step #4 – Create a Deffie-Hellman (DH) key for Forward Secrecy
The following screenshots shows where to create the Deffie-Hellman (DH) key in the GUI of the NetScaler:
NetScaler > Traffic Management > SSL


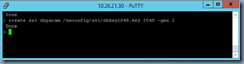
The command to execute to create the Deffie-Hellman (DH) key is as follows:
create ssl dhparam /nsconfig/ssl/dhkey2048.key 2048 -gen 2

Note that the process could take a few minutes before completing so wait until the green cursor display changes to a >:
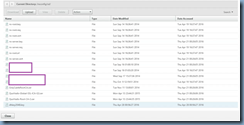
Reviewing the /nsconfig/ssl directory on the NetScaler should now show the dhkey2048.key key that was created:
Step #5 – Assign Deffie-Hellman (DH) key for Forward Secrecy to Virtual Server
With the Deffie-Hellman (DH) key successfully created, proceed with assigning it to the virtual servers.
The following screenshots shows where the settings are in the GUI:

Execute the following command to assign the key:
set ssl vserver StoreFront-lbvip -dh ENABLED -dhFile "/nsconfig/ssl/dhkey2048.key" -dhcount 1000

Repeat the process for the NetScaler Gateway Virtual Servers:
set ssl vserver www.contoso.com_external -dh ENABLED -dhFile "/nsconfig/ssl/dhkey2048.key" -dhcount 1000
set ssl vserver www.contoso.com_internal -dh ENABLED -dhFile "/nsconfig/ssl/dhkey2048.key" -dhcount 1000

Step #6 – Create a Rewrite Action and Policy for Strict Transport Security
Execute the following to create a Rewrite Action for Strict-Transport-Security:
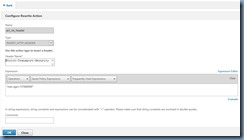
add rewrite action act_sts_header insert_http_header Strict-Transport-Security q/"max-age=157680000"/

With the command above successfully executed, you should now see the following action created:

Execute the following to assign the Rewrite Action for to a policy:
add rewrite policy pol_sts_header TRUE act_sts_header
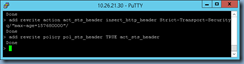
With the command above successfully executed, you should now see the following policy created with the action assigned:

Step #7 – Bind the Strict Transport Security policy to the Virtual Servers
With the Strict Transport Security policy created, proceed with binding them to the virtual servers with the following commands:
bind vpn vserver www.contoso.com_external -policy pol_sts_header -priority 100 -gotoPriorityExpression END -type RESPONSE
bind vpn vserver www.contoso.com_internal -policy pol_sts_header -priority 100 -gotoPriorityExpression END -type RESPONSE
bind lb vserver StoreFront-lbvip -policy pol_sts_header -priority 100 -gotoPriorityExpression END -type RESPONSE

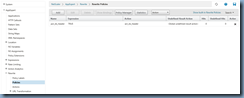
With the command above successfully executed, we should now see the policy binded to the virtual servers:

-----------------------------------------------------------------------------------------------------------------------------------------------------------------
Having completed all the steps outlined above should now allow the NetScaler site to score an A+: