Problem
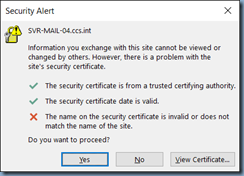
I’ve had a several clients call me in regards to a common issue when upgrading VMware Horizon View to veresion 7.0.x where their vCenter Servers status is labeled with the red colour and the Status is listed as Untrusted Certificate but clicking on the Verify button does nothing:
Status: Untrusted Certificate Verify
For self-signed certificate, click ‘Verify’. If the vCenter Server certificate can be validated, make sure that the trusted store on the Connection Server system has the correct Certification Authorities.
SSL Certificate: Invalid
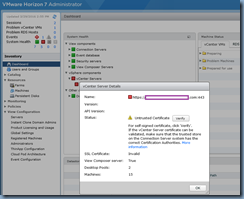

I find that this issue throws a lot of administrators off because previous versions simply allow you to click on the Verify button, accept the self-signed certificate, and you’re on your way but version 7 appears to render the button clickable but does nothing when you click on it other than give you a click symbol as if it was doing something:

Solution
The reason why this would happen is if the vCenter in the environment is running an earlier release of vCenter Server 5.0, 5.1, and 5.5 where only TLSv1.0 is supported. VMware Horizon 7 and later components have TLSv1.0 disabled and thus causes this strange behavior to occur. More information can be found in the deployment guide here:
View Installation
VMware Horizon 7 Version 7.0
VMware Horizon 7 Version 7.0.1
VMware Horizon 7 Version 7.0.2
http://pubs.vmware.com/horizon-7-view/topic/com.vmware.ICbase/PDF/view-70-installation.pdf

To resolve this issue, either upgrade vCenter Server to 6.0 Update 1B or workaround the issue by re-enabling TLSv1.0 on the VMware View Composer as outlined in the following KB:
Unable to verify vCenter certificate in VMware View Administrator (2144967)
https://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=2144967
Re-enable TLSv1.0 on enable VMware View Composer
To re-enable TLSv1.0 on enable VMware View Composer:
1. Click Start > Run, type regedit, and click OK. The Registry Editor window opens.
2. Navigate to HKLM\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS1.0\Client
Note: If this key does not already exist, create the key.
3. Delete the value Enabled if it exists.
4. Edit the DWORD value DisabledByDefault and set it to 0.
![clip_image002[5] clip_image002[5]](https://lh3.googleusercontent.com/-NTCDWkRout8/WCOE2xLXdmI/AAAAAAAB9r4/ktKb-J1ZBPQ/clip_image002%25255B5%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
5. Restart the VMware View Composer service. TLSv1.0 connections from View Composer to vCenter are now enabled.
6. Navigate to HKLM\SOFTWARE\VMware,Inc.\VMware View Composer.
7. Create or edit the String value EnableTLS1.0 and set it to 1.
8. If the View Composer host is a 64-bit machine, navigate to HKLM\SOFTWARE\WOW6432Node\VMware,Inc\VMware View Composer.
9. Create or edit the String value EnableTLS1.0 and set it to 1.
![clip_image002[7] clip_image002[7]](https://lh3.googleusercontent.com/-0utihaU-sB0/WCOE5kL8yLI/AAAAAAAB9sA/B-nwmvLszOE/clip_image002%25255B7%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
10. Restart the VMware Horizon View Composer service.TLSv1.0 connections from View Composer to ESXi hosts are now enabled.
Re-enable TLSv1.0 on enable VMware Connection Server
To re-enable TLSv1.0 on enable VMware Connection Server:
1. Start the ADSI Edit utility on your View Connection Server host.
2. In the console tree, select Connect to.
3. In the Select or type a Distinguished Name, type the distinguished name DC=vdi,DC=vmware, DC=int.
4. In the Computer pane, select or type localhost:389 or the fully qualified domain name (FQDN) of the View Connection Server host followed by port 389.
![clip_image002[9] clip_image002[9]](https://lh3.googleusercontent.com/-ds3lUkzml_c/WCOE7-vJZFI/AAAAAAAB9sI/OuUqHk1XfFs/clip_image002%25255B9%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
5. Expand the ADSI Edit tree, expand OU=Properties, select OU=Global, and double-click CN=Common.
6. In the Properties dialog box, edit the pae-ClientSSLSecureProtocols attribute to add this entry:
\LIST:TLSv1.2,TLSv1.1,TLSv1

![clip_image002[11] clip_image002[11]](https://lh3.googleusercontent.com/-SH__stZvexM/WCOFBstSmGI/AAAAAAAB9sY/M_qIwlbaLRg/clip_image002%25255B11%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
7. Click OK.
8. Restart the VMware Horizon View Connection Server service on each connection server instance.
![clip_image002[13] clip_image002[13]](https://lh3.googleusercontent.com/-J2OBMyi03IA/WCOFEpKn-eI/AAAAAAAB9sg/XCIsXImMGgs/clip_image002%25255B13%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
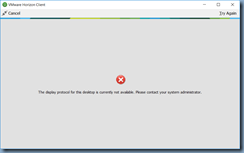















![clip_image002[5] clip_image002[5]](https://lh3.googleusercontent.com/-NTCDWkRout8/WCOE2xLXdmI/AAAAAAAB9r4/ktKb-J1ZBPQ/clip_image002%25255B5%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
![clip_image002[7] clip_image002[7]](https://lh3.googleusercontent.com/-0utihaU-sB0/WCOE5kL8yLI/AAAAAAAB9sA/B-nwmvLszOE/clip_image002%25255B7%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
![clip_image002[9] clip_image002[9]](https://lh3.googleusercontent.com/-ds3lUkzml_c/WCOE7-vJZFI/AAAAAAAB9sI/OuUqHk1XfFs/clip_image002%25255B9%25255D_thumb%25255B1%25255D.jpg?imgmax=800)

![clip_image002[11] clip_image002[11]](https://lh3.googleusercontent.com/-SH__stZvexM/WCOFBstSmGI/AAAAAAAB9sY/M_qIwlbaLRg/clip_image002%25255B11%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
![clip_image002[13] clip_image002[13]](https://lh3.googleusercontent.com/-J2OBMyi03IA/WCOFEpKn-eI/AAAAAAAB9sg/XCIsXImMGgs/clip_image002%25255B13%25255D_thumb%25255B1%25255D.jpg?imgmax=800)

![clip_image002[4] clip_image002[4]](https://lh3.googleusercontent.com/-I3PaqRmW_v4/WBsrB5sj8sI/AAAAAAAB9ps/o4gTZjXlebg/clip_image0024_thumb.jpg?imgmax=800)
![clip_image002[6] clip_image002[6]](https://lh3.googleusercontent.com/-hJYdAS7k0jA/WBsrEAxdwBI/AAAAAAAB9p0/7be-XRNDVmo/clip_image0026_thumb1.jpg?imgmax=800)
![clip_image002[8] clip_image002[8]](https://lh3.googleusercontent.com/-ThlhqwEZ00k/WBsrGrgcKJI/AAAAAAAB9p8/vkzEBKEugVg/clip_image0028_thumb1.jpg?imgmax=800)
![clip_image002[10] clip_image002[10]](https://lh3.googleusercontent.com/-IEUoeYGNg_Q/WBsrJAWiH5I/AAAAAAAB9qE/ql5u9Wi5m1Y/clip_image00210_thumb1.jpg?imgmax=800)
![clip_image002[12] clip_image002[12]](https://lh3.googleusercontent.com/-ruuFaY1VeBQ/WBsrLi13RWI/AAAAAAAB9qM/Y5nBu8xxj5Y/clip_image00212_thumb.jpg?imgmax=800)