Problem
You’re attempting to install a new role, such as mediation services, on an existing front end server but the process fails with the following message:
> Bootstrap-CsComputerLogging status to: C:\Users\a-tluk\AppData\Local\Temp\2\BootstrapFull-[2018_06_23][13_45_16].htmlChecking prerequisites for bootstrapper...Checking prerequisite WMIEnabled...prerequisite satisfied.Checking prerequisite NoBootstrapperOnBranchOfficeAppliance...prerequisite satisfied.Checking prerequisite SupportedOS...prerequisite satisfied.Checking prerequisite NoOtherVersionInstalled...prerequisite satisfied.Host name: drlyncstd01.contoso.comDisabling unused roles...Executing PowerShell command: Disable-CSComputer -Confirm:$false -Verbose -Report "C:\Users\a-tluk\AppData\Local\Temp\2\Disable-CSComputer-[2018_06_23][13_45_24].html"Checking prerequisites for roles...Checking prerequisite SupportedOS...prerequisite satisfied.Checking prerequisite SupportedOSNoDC...prerequisite satisfied.Checking prerequisite DotNet35...prerequisite satisfied.Checking prerequisite SupportedSqlRtcLocal...prerequisite satisfied.Checking prerequisite WMIEnabled...prerequisite satisfied.Checking prerequisite NoOtherVersionInstalled...prerequisite satisfied.Checking prerequisite PowerShell...prerequisite satisfied.Checking prerequisite SupportedServerOS...prerequisite satisfied.Checking prerequisite KB2533623Installed...prerequisite satisfied.Checking prerequisite SupportedSqlLyncLocal...prerequisite satisfied.Checking prerequisite SupportedSqlRtc...prerequisite satisfied.Checking prerequisite IIS...prerequisite satisfied.Checking prerequisite IIS7Features...prerequisite satisfied.Checking prerequisite KB2982006Installed...missingChecking prerequisite ASPNet...prerequisite satisfied.Checking prerequisite KB2646886Installed...prerequisite satisfied.Checking prerequisite BranchCacheBlock...prerequisite satisfied.Checking prerequisite WCF...prerequisite satisfied.Checking prerequisite WindowsMediaFoundation...prerequisite satisfied.Prerequisite not satisfied: Before you install Skype for Business Server 2015, you must install an update for Windows Server 2012 R2. For details about the update, see Microsoft Knowledge Base article 2982006, "IIS crashes occasionally when a request is sent to a default document in Windows 8.1 or Windows Server 2012 R2" at http://go.microsoft.com/fwlink/?LinkId=519376
You navigate to the provided URL:
http://go.microsoft.com/fwlink/?LinkId=519376
… which redirects you to the following KB:
IIS crashes occasionally when a request is sent to a default document in Windows 8.1 or Windows Server 2012 R2
https://support.microsoft.com/en-us/help/2982006/iis-crashes-occasionally-when-a-request-is-sent-to-a-default-document
Last Updated Dec 9, 2014
… download the update but realize that it will not install:
The update is not applicable to your computer.
Solution
The supplied KB is outdated and have since been updated with the following correct one:
Prerequisite (KB2982006) not satisfied when you try to install Skype for Business Server 2015
https://support.microsoft.com/en-us/help/4056288/can-t-install-skype-for-business-server-2015-due-to-missing-kb2982006
Cause
This issue occurs because the WMI query result of the prerequisite of KB2982006 isn't reliable.
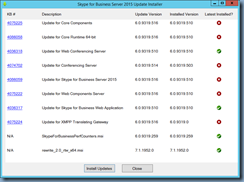
To correct the issue, navigate to the following URL and install the January 2018 cumulative update 6.0.9319.514 for Skype for Business Server 2015, core components or later CU:
https://support.microsoft.com/en-us/help/4074705
I went ahead and installed the March 2018 CU:
Business Server 2015 Cumulative Update KB3061064 Mar 2018
… and was able to proceed with the install: