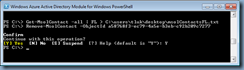
Problem
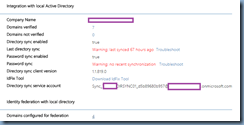
You’ve noticed that your Azure AD synchronization has stopped synchronizing for a period of time:
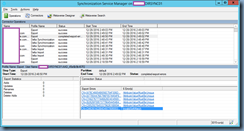
Launching the Synchronization Service Manager indicates the export job is failing with stopped-extension-dll-exception:
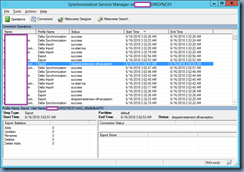
Reviewing the event logs show the following three events consistently logged:
- Event ID: 6900
- Event ID: 659
- Event ID: 906
Log Name: Application
Source: ADSync
Event ID: 6900
Level: Error
The server encountered an unexpected error while processing a password change notification:
"user_realm_discovery_failed: User realm discovery failed
at InitializeAndGetTargetExtension(Object lockObject, TargetTaskScheduler taskScheduler, Dictionary`2 targetExtensions, ECMAInformation* ecmaInformation)
at TargetExtensionManager.ExportPasswords(TargetExtensionManager* , ECMAInformation* ecmaInformation, DynamicArray<ActiveDirectoryPasswordChange \*>* targetPasswordChanges, Char* forestInfo)
InnerException=>
The remote server returned an error: (407) Proxy Authentication Required.
at System.Net.HttpWebRequest.GetResponse()
at Microsoft.IdentityModel.Clients.ActiveDirectory.HttpWebRequestWrapper.<GetResponseSyncOrAsync>d__2.MoveNext()
--- End of stack trace from previous location where exception was thrown ---
at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw()
at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
at Microsoft.IdentityModel.Clients.ActiveDirectory.UserRealmDiscoveryResponse.<CreateByDiscoveryAsync>d__0.MoveNext()
InnerException=>
none
"
Log Name: Application
Source: Directory Synchronization
Event ID: 659
Level: Error
Error while retrieving password policy sync configuration. Microsoft.IdentityModel.Clients.ActiveDirectory.AdalServiceException: user_realm_discovery_failed: User realm discovery failed ---> System.Net.WebException: The remote server returned an error: (407) Proxy Authentication Required.
at System.Net.HttpWebRequest.GetResponse()
at Microsoft.IdentityModel.Clients.ActiveDirectory.HttpWebRequestWrapper.<GetResponseSyncOrAsync>d__2.MoveNext()
--- End of stack trace from previous location where exception was thrown ---
at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw()
at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
at Microsoft.IdentityModel.Clients.ActiveDirectory.UserRealmDiscoveryResponse.<CreateByDiscoveryAsync>d__0.MoveNext()
--- End of inner exception stack trace ---
at Microsoft.IdentityModel.Clients.ActiveDirectory.AuthenticationContext.RunAsyncTask[T](Task`1 task)
at Microsoft.Online.Coexistence.ProvisionHelper.GetADALToken(String userName, String userPassword, MSOInstance adalServiceResource)
at Microsoft.Online.Coexistence.ProvisionHelper.GetSecurityToken(String userName, String userPassword, MSOInstance adalServiceResource)
at Microsoft.Azure.ActiveDirectory.Connector.ProvisioningServiceAdapter.InitializeProvisionHelper()
at Microsoft.Azure.ActiveDirectory.Connector.ProvisioningServiceAdapter.Initialize()
at Microsoft.Azure.ActiveDirectory.Connector.ProvisioningServiceAdapter.GetCompanyConfiguration()
at Microsoft.Azure.ActiveDirectory.Connector.PasswordPolicy.RefreshPasswordPolicySyncSettings()
ErrorCode: user_realm_discovery_failed
StatusCode: 0
Log Name: Application
Source: Directory Synchronization
Event ID: 906
Level: Error
GetADALToken [user_realm_discovery_failed]: unexpected authentication failure. STS endpoint (https://login.windows.net), userName (Sync_DIRSYNC01_d5b89680b957@contoso.onmicrosoft.com), tenantName (contoso.onmicrosoft.com), adalAuthority(https://login.windows.net/contoso.onmicrosoft.com) user_realm_discovery_failed: User realm discovery failed | The remote server returned an error: (407) Proxy Authentication Required..
Solution
One of the possible causes to this error is if the DirSync service is attempting reach Azure via a proxy server and is unable to authenticate. In the case of this example, the DirSync server was able to synchronize directly via the internet but had inadvertently inherited proxy settings due to a network misconfiguration. Changing the proxy settings did not correct the problem as DirSync continued to connect to the proxy. To correct this problem, you’ll need to edit a configuration file for the synchronization service manager to stop it from using a proxy. Navigate to the following directly:
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\config
.. and locate the machine.config file:
Duplicate the file to create a backup:
Open the file and navigate to the end of the configuration:
Add the following under the </system.web> tag:
<system.net>
<defaultProxy enabled="false"></defaultProxy>
</system.net>
Save the file, restart the Azure synchronization services and rerun the synchronization.