As I had to deploy 2 new instances of vCenter over the weekend in Linked Mode, I took the opportunity to document all the steps so I could write a blog post demonstrating the steps for the deployment. The follow demonstrates a VMware vSphere 5.1 vCenter deployment with all the services installed onto the server and a full SQL 2008 R2 Standard Server installed directly onto the same vCenter server.
Prerequisites
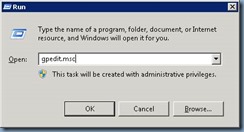
Begin by creating an Active Directory domain account that you’ll be using to run the vCenter service and grant it Act as part of the operating system permissions to the vCenter server. You can use a GPO to assign the permission or edit the local computer policy. For the purpose of this example, I will use the Local Computer Policy so open up the Run prompt and run:
gpedit.msc
Navigate to Local Computer Policy –> Computer Configuration –> Windows Settings –> Security Settings –> Local Policies –> User Rights Assignment
Edit the Act as part of the operating system policy and add the vCenter service account in:
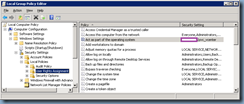
Next, add the vCenter service account into the local Administrators group on the vCenter server:
With the permissions for the service account set, proceed with adding the .NET Framework 3.5.1. feature onto the server by opening PowerShell ane executing the following cmdlet:
Import-Module ServerManager
Add-WindowsFeature as-net-framework
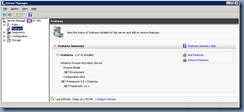
You can use the Server Manager to confirm that it is installed by navigating to the Features node:
Set up Single Sign On (SSO) Database
The scripts that we’ll be using to create the database used by the Single Sign On (SSO) service can be found in the following location (assuming you’ve extracted the package to your C drive):
C:\VMware-VIMSetup-all-5.1.0-880471\Single Sign On\DBScripts\SSOServer\schema\mssql
- rsaIMSLiteMSSQLCreateSchema.sql
- rsaIMSLiteMSSQLDropSchema.sql
- rsaIMSLiteMSSQLDropUsers.sql
- rsaIMSLiteMSSQLSetupTablespaces.sql
- rsaIMSLiteMSSQLSetupUsers.sql
The scripts we’ll be using are:
- rsaIMSLiteMSSQLSetupTablespaces.sql
- rsaIMSLiteMSSQLSetupUsers.sql
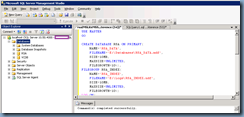
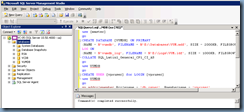
Begin by launching SQL Server Management Studio and opening the first script:
rsaIMSLiteMSSQLSetupTablespaces.sql
CREATE DATABASE RSA ON PRIMARY(
NAME='RSA_DATA',
FILENAME='C:\CHANGE ME\RSA_DATA.mdf',
SIZE=10MB,
MAXSIZE=UNLIMITED,
FILEGROWTH=10%),
FILEGROUP RSA_INDEX(
NAME='RSA_INDEX',
FILENAME='C:\CHANGE ME\RSA_INDEX.ndf',
SIZE=10MB,
MAXSIZE=UNLIMITED,
FILEGROWTH=10%)
LOG ON(
NAME='translog',
FILENAME='C:\CHANGE ME\translog.ldf',
SIZE=10MB,
MAXSIZE=UNLIMITED,
FILEGROWTH=10% )
GO
-- Set recommended perform settings on the database
EXEC SP_DBOPTION 'RSA', 'autoshrink', true
GO
EXEC SP_DBOPTION 'RSA', 'trunc. log on chkpt.', true
GO
CHECKPOINT
GO
------------------------------------------------------------------------------------------------------------------------------------------------------------------
It’s important to note that names RSA_DATA and RSA_INDEX are supposed to be hard coded in the Single Sign On service and while this may change in the future, it’s best to not attempt to change them. With that being said, you are free to change the database name RSA to a different name. Whether you change use a different name would be your choice but to keep the database recognizable to anyone upon first glance, I’m going to continue using RSA as the name. This means that the only content I’m going to change is the location of the mdf, ndf and ldf files highlighted in RED:
CREATE DATABASE RSA ON PRIMARY(
NAME='RSA_DATA',
FILENAME='E:\Databases\RSA_DATA.mdf',
SIZE=10MB,
MAXSIZE=UNLIMITED,
FILEGROWTH=10%),
FILEGROUP RSA_INDEX(
NAME='RSA_INDEX',
FILENAME='E:\Databases\RSA_INDEX.ndf',
SIZE=10MB,
MAXSIZE=UNLIMITED,
FILEGROWTH=10%)
LOG ON(
NAME='translog',
FILENAME='E:\Logs\translog.ldf',
SIZE=10MB,
MAXSIZE=UNLIMITED,
FILEGROWTH=10% )
GO
-- Set recommended perform settings on the database
EXEC SP_DBOPTION 'RSA', 'autoshrink', true
GO
EXEC SP_DBOPTION 'RSA', 'trunc. log on chkpt.', true
GO
CHECKPOINT
GO
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
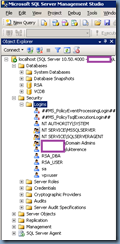
Executing the script above should create the RSA database shown in the Object Explorer on the left:
With the database created, the next step is to set up the 2 user objects required for accessing the RSA database. To so do, use the following script:
rsaIMSLiteMSSQLSetupUsers.sql
USE MASTER
GO
CREATE LOGIN RSA_DBA WITH PASSWORD = '<CHANGE DBA PASSWORD>', DEFAULT_DATABASE = RSA
GO
CREATE LOGIN RSA_USER WITH PASSWORD = '<CHANGE USER PASSWORD>', DEFAULT_DATABASE = RSA
GO
USE RSA
GO
ALTER AUTHORIZATION ON DATABASE::RSA TO [RSA_DBA]
GO
CREATE USER RSA_USER FOR LOGIN [RSA_USER]
GO
CHECKPOINT
GO
------------------------------------------------------------------------------------------------------------------------------------------------------------------
It’s important to note that the comments state the following:
-- The DBA account is used during installation and the USER account is used during
-- operation. The user names below can be customised, but it is forbidden to include
-- reserved keywords like table or any characters other than letters, numbers, and _ .
So proceed with using the default user account names RSA_USER and RSA_DBA or change them if you would like to use another name. For the purpose of this demonstration and to keep things consistent with the first script used to create the database, I will only change the passwords highlighted in RED:
USE MASTER
GO
CREATE LOGIN RSA_DBA WITH PASSWORD = '2wsx@WSX', DEFAULT_DATABASE = RSA
GO
CREATE LOGIN RSA_USER WITH PASSWORD = '2wsx@WSX', DEFAULT_DATABASE = RSA
GO
USE RSA
GO
ALTER AUTHORIZATION ON DATABASE::RSA TO [RSA_DBA]
GO
CREATE USER RSA_USER FOR LOGIN [RSA_USER]
GO
CHECKPOINT
GO
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
Executing the script above should create the user accounts and assign the appropriate permissions to the RSA database:
Note the 2 accounts located under Security –> Logins:
- RSA_DBA
- RSA_USER
**Note that there is no need to run the other scripts such as:
rsaIMSLiteMSSQLCreateSchema.sql
… or you may run into the error message:
Error 29120. Database schema already exists
… that I blogged about earlier here: http://terenceluk.blogspot.com/2013/02/installing-vsphere-51-vcenter-single.html
Set up vCenter Database and ODBC
The first step for setting up the vCenter database is to create the database with the following script found on page 205 in the installation guide (http://pubs.vmware.com/vsphere-51/topic/com.vmware.ICbase/PDF/vsphere-esxi-vcenter-server-51-installation-setup-guide.pdf):
use [master]
go
CREATE DATABASE [VCDB] ON PRIMARY
(NAME = N'vcdb', FILENAME = N'C:\VCDB.mdf', SIZE = 2000KB, FILEGROWTH = 10% )
LOG ON
(NAME = N'vcdb_log', FILENAME = N'C:\VCDB.ldf', SIZE = 1000KB, FILEGROWTH = 10%)
COLLATE SQL_Latin1_General_CP1_CI_AS
go
use VCDB
go
sp_addlogin @loginame=[vpxuser], @passwd=N'vpxuser!0', @defdb='VCDB',
@deflanguage='us_english'
go
ALTER LOGIN [vpxuser] WITH CHECK_POLICY = OFF
go
CREATE USER [vpxuser] for LOGIN [vpxuser]
go
use MSDB
go
CREATE USER [vpxuser] for LOGIN [vpxuser]
go
From this point, we need to make a decision on the following:
- Set Database Permissions By Manually Creating Database Roles and the VMW
Schema - Set Database Permissions by Using the dbo Schema and the db_owner Database
Role
Option #1 takes a bit more time because you need to manually create the database roles and assign them to the service account while the latter simply assigns the dbo Schema and db_owner database role to your service account. What’s interesting is that I believe option #1 was introduced in vCenter 5.0 because I don’t recall seeing this in the earlier deployment guides. I’ve always used the 2nd option but it’s obviously not as secure because VMware does recommend option #1. With that being said, I will only demonstrate option #2 as I for this particular deployment, I went with that route.
Since we won’t be using Windows Authentication (like my vCenter 4.1 post here: http://terenceluk.blogspot.com/2010/10/creating-vcenter-41-sql-database-and.html) and that we’ll be using SQL Authentication, we can pretty much just use the default script with the modifications highlighted in red:
use [master]
go
CREATE DATABASE [VCDB] ON PRIMARY
(NAME = N'vcdb', FILENAME = N'K:\Databases\VCDB.mdf', SIZE = 2000KB, FILEGROWTH = 10% )
LOG ON
(NAME = N'vcdb_log', FILENAME = N'L:\Logs\VCDB.ldf', SIZE = 1000KB, FILEGROWTH = 10%)
COLLATE SQL_Latin1_General_CP1_CI_AS
go
use VCDB
go
sp_addlogin @loginame=[vpxuser], @passwd=N'P@ssw0rd', @defdb='VCDB',
@deflanguage='us_english'
go
ALTER LOGIN [vpxuser] WITH CHECK_POLICY = OFF
go
CREATE USER [vpxuser] for LOGIN [vpxuser]
go
use MSDB
go
CREATE USER [vpxuser] for LOGIN [vpxuser]
Continue by clicking on the Execute button and ensure that the Messages windows outputs the message: Command(s) completed successfully.
Since we went with option #2 for this example, we will also need to execute the following:
use VCDB
go
sp_addrolemember @rolename = 'db_owner', @membername = 'vpxuser'
go
use MSDB
go
sp_addrolemember @rolename = 'db_owner', @membername = 'vpxuser'
go
Alternatively, if you want to combine both of the transact-sql statements together, you can execute the following in one shot:
use [master]
go
CREATE DATABASE [VCDB] ON PRIMARY
(NAME = N'vcdb', FILENAME = N'K:\Databases\VCDB.mdf', SIZE = 2000KB, FILEGROWTH = 10% ) LOG ON
(NAME = N'vcdb_log', FILENAME = N'L:\Logs\VCDB.ldf', SIZE = 1000KB, FILEGROWTH = 10%) COLLATE SQL_Latin1_General_CP1_CI_AS
go
use VCDB
go
sp_addlogin @loginame=[vpxuser], @passwd=N'P@ssw0rd', @defdb='VCDB',
@deflanguage='us_english'
go
ALTER LOGIN [vpxuser] WITH CHECK_POLICY = OFF
go
CREATE USER [vpxuser] for LOGIN [vpxuser]
go
sp_addrolemember @rolename = 'db_owner', @membername = 'vpxuser'
go
use MSDB
go
CREATE USER [vpxuser] for LOGIN [vpxuser]
go
sp_addrolemember @rolename = 'db_owner', @membername = 'vpxuser'
With the database created, the next step is to create the 64-bit ODBC DSN Connection by opening up the Start menu, navigate to Administrative Tools –> Data Sources (ODBC) then select the System DSN tab and click Add:
A common mistake I’ve come across when troubleshooting DSN creation problems is that a SQL Server driver was created instead of the SQL Server Native Client 10.0. So make sure you select the latter and click Finish.
SQL Server = WRONG
SQL Server Native Client 10.0 = RIGHT
Fill in the following fields:
Name: This is just a logical name and can be anything you want.
Description: Logical description.
Server: You can either put the NetBIOS or FQDN of the server name. I personally prefer the FQDN.
Since we’re not using a domain service account, select the radio button for With SQL Server authentication using a login ID and password entered by the user and enter the credentials for the account you configured during the database creation:
Make sure you change the default database to your vCenter database that you created earlier. The name in the installation guide is VCDB:
Leave the following settings as default and click Finish:
A window is now presented that allows you to test the ODBC connection. Proceed with clicking on the Test Data Source button to test connecting over to the vCenter database with the SQL Authentication credentials entered in one of the previous screens:
Confirm that the test completes successfully:
Once you click finish, you will now see your new ODBC DSN:
Set up vSphere Update Manager (VUM) Database and ODBC
Setting up the vCenter 5.1 Update Manager (VUM) database is pretty much the same as setting up the vCenter database and the following are the assumptions made for the VUM environment:
- We are going to use the same VPXUSER account that we are using for the vCenter database to access the VUM database with SQL Authentication
The following is the transact-sql to use to create the database and assign the appropriate permissions:
use [master]
go
CREATE DATABASE [VUMDB] ON PRIMARY
(NAME = N'vumdb', FILENAME = N'K:\Databases\VUM.mdf', SIZE = 2000KB, FILEGROWTH = 10% )
LOG ON
(NAME = N'vumdb_log', FILENAME = N'L:\Logs\VUM.ldf', SIZE = 1000KB, FILEGROWTH = 10%)
COLLATE SQL_Latin1_General_CP1_CI_AS
go
use VUMDB
go
CREATE USER [vpxuser] for LOGIN [vpxuser]
use VUMDB
go
sp_addrolemember @rolename = 'db_owner', @membername = 'vpxuser'
go
As with vCenter 4.1 and 5.0 Update Manager, the vCenter 5.1 Update Manager still uses a 32 bit DSN so make sure you open up the ODBC Data Source Administrator via:
%systemdrive%\Windows\SysWoW64\Odbcad32.exe
Then proceed with creating the DSN as shown in the following screenshots:
Change the default database to the VUM database:
Test the ODBC DSN:
Install vCenter Single Sign On Service (SSO)
Begin by launching the VMware vCenter Installer and selecting vCenter Single Sign On:
Select Create the primary node for a new vCenter Single Sign On installation:
Instead of selecting the Install basic vCenter Single Sign On option, select Create the primary node for a new vCenter Single Sign On installation:
**Note that we have nothing to lose with selecting the 2nd option because the SSO service will operate as normal even if we do not add an additional SSO node to the installation such as when we want to install another vCenter in Linked Mode. If we were to choose the first option, we would not be able to add any additional vCenters to the environment.
Enter the password you would like to use for the admin@System-Domain account for the Single Sign On service:
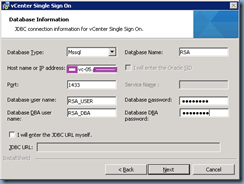
Select Use an existing supported database:
Fill in the fields:
Host name or IP address <— The database server’s FQDN
Database Name <— The name of the database (we used RSA)
Port <— Leave as the standard 1433 unless this has been changed on the SQL server
Database user name <— The name of the database user account (we used RSA_USER)
Database password <— The password for the database user account
Database DBA user name <— The name of the database DBA user account (we used RSA_DBA)
Database DBA password <— The password for the database DBA user account
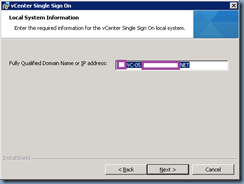
The following field should be automatically filled in with the FQDN of server you’re installing the SSO service on:
Before proceeding to the next prompt, click on the Back button to get back to the SSO database information prompt:
Note that the JDBC URL is now filled out. Assuming that you don’t care to encrypt the traffic between the SQL server and the SSO service, you can proceed with the install. If encrypting the traffic between the SQL server and SSO service is important, there are 2 ways to approach this and the first is to use the self signed certificate on the SQL server that isn’t trusted by the vCenter SSO service by default. This can be done by appending the following to the end of the JDBC URL:
encrypt=true;trustservercertificate=true
… so that the URL would look something like this:
jdbc:sqlserver://;serverName=dbServer.domain.com;port=1433;databaseName=RSA;encrypt=true;trustservercertificate=true
The second option is to configure proper Certificate Authority issued certificates for securing the traffic. I will not be going into this for this blog post so I’m simply going to append the string above to force the trust.
The FQDN should automatically be filled in for you:
While the following prompt is traditionally filled in with the account you are logged in, I noticed that this wasn’t the case for me so uncheck the Use network service account and fill in the vCenter domain service account:
Confirm the directory for the SSO files:
Unless there’s a reason why you need to change the SSO HTTPS port @ 7444, leave it as default:
Proceed with the install:
Install vCenter Inventory Service
Begin by launching the VMware vCenter Installer and selecting VMware vCenter Inventory Service:
Proceed through the wizard:
Accept the EULA:
Confirm the location to install the files:
The following field should automatically be filled in with the FQDN of the server you’re installing the Inventory Service on:
Accept the default ports unless they need to be changed:
Select the appropriate Inventory Size for the JVM Memory:
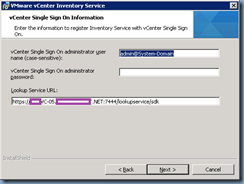
The Lookup Service URL should automatically be filled out for you so enter the vCenter Single Sign On administrator password:
Confirm to over write certificates:
Proceed with the install:
Install vCenter Server
Begin by launching the VMware vCenter Installer and selecting VMware vCenter Server:
Proceed through the wizard:
Note that Microsoft Visual C++ 2005 Redistributable will be automatically installed for you:
Accept the EULA:
Enter a license key if you have it already or you can enter it afterwards:
Select the ODBC DNS that was created earlier for the VCDB vCenter database:
Enter the credentials for the SQL Server Authentication vpxuser account:
-------------------------------------------------------------------------------------------------------------------------------------------------------------------
**Note that if you receive the following error:
The DB user entered does not have the required permissions needed to install and configure vCenter Server with the selected DB…
This is most likely because you forgot to assign the permissions to the VCDB database for the vpxuser account. You can execute the following SQL commands to quickly assign the permissions:
use VCDBgo
sp_addrolemember @rolename = 'db_owner', @membername = 'vpxuser'
go
use MSDB
go
sp_addrolemember @rolename = 'db_owner', @membername = 'vpxuser'
go
-------------------------------------------------------------------------------------------------------------------------------------------------------------------
You may receive the following warning message as you proceed which is just a reminder that the database is set to Full recovery model meaning the transaction logs (ldf) file will continue to grow if they are not backed up and/or truncated. Whether you switch the recovery model to simple would depend on the backup strategy for the database.
-------------------------------------------------------------------------------------------------------------------------------------------------------------------
Uncheck the Use SYSTEM Account checkbox and enter the credentials for the vCenter domain service account:
Select Create a standalone VMware vCenter Server instance:
Confirm the default ports being used for the vCenter service:
Select the appropriate Inventory Size:
The Lookup Service URL should automatically be filled out for you so enter the vCenter Single Sign On administrator password:
Since we installed the SSO service for Multinode high availability and/or multisite, leaving the default Administrators would most likely throw the error:
Wrong input – either a command line argument is wrong, a file cannot be found or the spec file doesn’t contain the required information, or the clocks on the two systems are not synchronized. Check vm_ssoreg.log in system temporary folder for details.
The reason why this error is presented is because SSO installed to support multisites does not support local accounts which makes sense because you can’t possibly assign a local account on one vCenter to another since the directory is local to the server. To proceed, change the field to a domain user or group. In this example, I used domain admins:
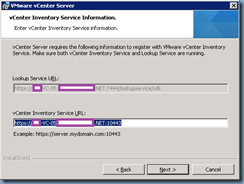
The Lookup Service URL and vCenter Inventory Service URL fields should automatically be populated for you:
Confirm the folder to install the vCenter files:
Proceed with the install:
As noted in the following KB:
Active Directory Web Services fails to read the settings for the specified Active Directory Lightweight Directory Services instance
http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=1023864
One of the items to check before concluding the install is to navigate to the following registry key:
HKLM\System\CurrentControlSet\Services\<ADAM_INSTANCE_NAME>\Parameters\Port SSL
… and check to see if the Port SSL key is of the type REG_DWORD and if it is the type REG_SZ as shown above then you will need to delete it and recreate it as a REG_DWORD with the decimal value of 636 shown below:
Install vSphere Client
Proceed with the install of the vSphere Client so you can test vCenter connectivity.
Install vSphere Web Client
Proceed with the install of the vSphere Client for vCenter connectivity through a browser and/or adding earlier vCenter 5.0 severs for management (vCenter 5.1 servers are automatically added):
The Lookup Service URL field should already be populated so continue by filling in the SSO administrator password:
To add vCenter 5.0 servers, launch the vSphere Administration Application from the Start Menu:
… and add it via the vSphere Web Client Administration Tool. Remember that this is only for older 5.0 vCenters and not 5.1:
To verify that the vSphere Web Client is functioning as expected, launch it via the Start Menu:
Install vSphere Update Manager
The last component to install is the vSphere Update Manager service so being by launching the installer and select vSphere Update Manager:
Proceed through the wizard:
Accept the EULA:
I prefer to use the DNS name even though the default is set to the IP address of the server so make the appropriate changes and enter the vCenter server service credentials or another service account if you want to use a different account:
Select the ODBC DSN that was created earlier and type in the vpxuser account’s password:
Select the name of the server and accept the default ports:
I usually prefer to add separate drive for the location that the patches are downloaded to so make the appropriate changes:
Proceed with the install:
Test vCenter Connectivity
With all the components installed, proceed with launching the vSphere Client and test connectivity to vCenter:
Once logged in, verify that all the services are functioning as expected. As a final check, it may also be worth while to check the services on the server to ensure they are all started:
- vCenter Single Sign On
- VMware vCenter Inventory Service
- VMware vCenter Orchestrator Configuration <— Manual startup
- VMware vCenter Orchestrator Server <— Manual startup
- VMware VirtualCenter Management Webservice
- VMware VirtualCenter Server
- VMware vSphere Profile-Driven Storage Service
- VMware vSphere Update Manager Service
- VMware vSphere Update Manager UFA Service <— Manual startup
- MVware vSphere Web Client
This concludes this blog post. I will be posting the second part of this deployment at a later time where the second vCenter was installed and joined in Linked Mode.


![clip_image002[6] clip_image002[6]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhwvkip6jJo-1W4T3DfVhnlf-_BRww79qK1_G5v2LAchqmmv_i92ZYqJ50Bw_NnDo5g1k5WwciwSgBu1BxPLRzbIqEogK9XD4YOo8LlFPoEzxnlHJHXTf1HbM7LuIgzXI4c6jhUjAcgUDyc/?imgmax=800)
![clip_image002[1] clip_image002[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEguoOoBbmklrWd7cnSsMmaF0TmvrVxT808YatMlWljetB04qy3dGHS0WiTQJ1Q4OZJVwzkXyah6JnCnrTDhmOr66d-KRWX5tF-iegosw30agTdrwi2jGo-hbMnvUV3Jl4OeXJyEg4orxiI8/?imgmax=800)
![clip_image002[3] clip_image002[3]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhPEjyKVk9UEaRSDfn26LqWfzPbWPjt0GKp4M73YI_LW_JIsP1m37PgQ9dtqAd8yhNOdNL6awwhvPhRQcGKVs5lRwU9zGk8suxlCBp7BrCElphKDkDEIpxEi-MbeqZD3p4uoHRQOFvsX1Cx/?imgmax=800)

![clip_image002[5] clip_image002[5]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjPWXgDHKwoIbXNdX7XeaUGEmwfgH57ZkbQpFeGU81_yVYza_gnPlyk4b9cfn0OFf9trtJil6POKGNUcsLr9nrx5Ei1T_uq5BMD18uriSZLfZhBRV1jM-XghxwwC2SFGw8wQr7inViwS0AE/?imgmax=800)






![clip_image002[1] clip_image002[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi3Z3pHrEYWiut_oeDgesDnh99M6je7NZ7SzWOGSu1pg7RHf7kpRxKOaQn5QtRKhwffhwPcz6yHyYASf_fxaPxxAMzhGphfc9ZEpRZ-YZP-ZMERt0V-panNJsD2XDGn1cAW3Ii3tuws1Mvs/?imgmax=800)
![clip_image002[3] clip_image002[3]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgDtHyC2LTDJ0u14LrqbyvORvPFXyJa1KxooRuJUg1RyPMbrLLNyoTPOwHigrla7aNnK_khdHOh860mEZlGXdplJHZdVzqXTILDTWAxdmolej0FOnvzpKwGrj2DXI_uZObsfV_j4DXt1QO9/?imgmax=800)

![clip_image002[5] clip_image002[5]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgilH7gr-T9rSMy-xuwhQaB1E9k7eKe4fBsIAmYCcrzlZgiJDsIMTju7oU7smZOqaC8MDDVz474RXcItbJyAPQ2vfvyhcZ1Hj3sXqjSd6x8ZRKBf8_RSN-pczQm-XbSLqi5SLm0p0n8NvDP/?imgmax=800)
![clip_image002[7] clip_image002[7]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjpfwFDH5T8c4eqe0PZSN4FHkeTVUShAvUeJV2HeaRVoXoidY1Uq1fEyKXx9aK28Nngsxj7wkVYJdaZTkwmwLkFJ2XpJ-mz3GkAEdbZAK7xV3ZIt6AWPKlai3QMtXta_ek6wWQNQlBv9LH9/?imgmax=800)
![clip_image002[9] clip_image002[9]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhofxFi5BLQ3YhTFXAud6TK_WcEFVo4cYmaBXfc0z6z8weARLj95gQp0hBVg_uPMvoLk7PF7L6OdpUwgQ38hN5NwGIym5FJ00bGWcEtlwxjL_xh6-aDSvF7aXEwkOHAeyOEheKlsBbDJYe4/?imgmax=800)

![clip_image002[11] clip_image002[11]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhy2JGV9IjNug7AsSbvmZfMZJc_qVVKaCFxYJrNjH-DG5oqBgE4tq9voLHW-EC9S8_0Mjtw4uO1TqdIp_6f4swCWqD88zOOf0G0nQPbURECfvHKD5twEXnMZmaCvRR125S6GaMNvFZTb5fw/?imgmax=800)
![clip_image002[13] clip_image002[13]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiww4Kunlf-vfVXMMaAA4BzVYCIPSjog9axQjs7KVhHBiZSu_VtLc5sDPa4WlLc4eesyJW6dImbyIS4XMjD8Czho0R1QyGUnA3b2hl5AFSH3feYnQb5cVR9NW1StECxE9T6IhNX6ekBML8y/?imgmax=800)


![clip_image002[15] clip_image002[15]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjrjmJb5vUk0QRfJblQzOg7WwLovQpfLUSG1alJzDU1QPrSJJnYgN7E-KwrRu9ic-2rK6qrOi7EthpeFFq9TxdLIsl1yKv-94dIdIklYlHD4FqU0rlj0O3nHsc461wcVMLTSLfjuoFMLkUD/?imgmax=800)
![clip_image002[17] clip_image002[17]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjtnGthZ3AgbodbcWOp70Rrya6G6-2K2JvtqM60hC3ioVoHvGgrzanSOcMnHG6M12CecHyEphue-BGG6_xAZ409xIgaGXLWRtBvayXWLflckrds-h3VCBOafAXvN4MoR4BPl4ARwe7TSuQZ/?imgmax=800)
![clip_image002[19] clip_image002[19]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi6Mo6TYTwvL1CJ3LMWIx1nLfaIUadu0jVkGBMKbiYB4rdPvGrM4qrns_0X3rf8hqyMbY771KMiiV3W18zsJL2hPXszWSYc7raFgONqh025Sg-w2gGFLE0MZjIPTwnO9LAOsX-SEgOtC66Z/?imgmax=800)
![clip_image002[21] clip_image002[21]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjJHgZviYOV6_7y8KtL4GIAh39Zn7iqUJppQFDgD4w5QuYySjZZWC6qtRZ-p9WYZj223fLqN7T2CCVoLimJ3phOgR7uvgLjJbugKxj8cKiBL4cG0yd0tPtcxRV5fwz7-72w-8xgEwJA_v7f/?imgmax=800)
![clip_image002[23] clip_image002[23]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEin5ZpkHAZhaTL0UBLQthFJ_pCZaShNwSCa6h_r9AmaZd_XvedmJechqI23vTF2YOoCQxOJuYB1WbxQKW3pVssMmge8ZyGsA9d61NYXnYiQjqXEiPjtU9Dv5wmKstzd2TpuiLEnov4Y1iFe/?imgmax=800)

![clip_image002[25] clip_image002[25]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjoERBST2BT_LcG_PmRpqNGZvOM36lA2NFCOHXX9Z7TDFtEAHlq6ZNzxWmqVwgvcA6gEt4xeIRnhDpEqq8knEUVCABSCJTtGAXc2mFD9_2CTXTzJXRNSyV6Z9CI4wyKwKk6Kcb-f9fg0PtU/?imgmax=800)
![clip_image002[27] clip_image002[27]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg6WaDKLPBCzQjMRcWpIKN2lDr6MzaqGEQi1PfO6I2c27I7-U3e7jLCW2ZJ8Z1U4zBRZnXkKV0MgrwU3pwlTvU0q43NSAXBMXpXQTTNe8hX0uniBITnrfRKrPCqO-VhwbSPYMz6p4QJkUOS/?imgmax=800)
![clip_image002[29] clip_image002[29]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjbJLQr489qwja_1TWPzbmJ54YQzvcy7ASdcimkGoHuULanl9vTrzDdEBObPSmxiXGjO1he0A4PdJa0O2aErpYYyLPd_cY8BA3X2JLkQYsPEiqXYZdCYH60sB4rRIiNQ4y6URh_jTG1fPwr/?imgmax=800)
![clip_image002[31] clip_image002[31]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjgFbNJgidZte2fUf8CmBAqFVyUYkw8z3wzeq8s3DHJHgmGKogPWindijEPSfvjVTMHIecicHMHUk-X4qMpaKJ_SaniIBtmcork0dHCblgBdIqVstuK_Kvsfj-13i6SQzgkrRQRgnEZXiqH/?imgmax=800)
![clip_image002[33] clip_image002[33]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiGxhBfHr9iueBhup8pgo6O8TO5NQAZzW08nXpPJ_eg7Yfv90sBWwcYwRoGLeW1wXw8Sn8c9Ak7yNNY37-k4pldSVoLL_5wTfpgecgwx3BzEkK8vTisGW-lfQyfpESGY70hMpBSom-ziNMl/?imgmax=800)
![clip_image002[35] clip_image002[35]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjJMOKMTn_nJUhTfs7t_EpvUxd2_zKubzOaCvWrqhzynjaVr_vjY1EjCIxbZlzP6VWRlwAfYt1dfl6QN7QvjGxK4stuLyc8721r-47fYUo-lxrluNVxNHU3rW5EdPDQzld1H4eV05YdJjlt/?imgmax=800)
![clip_image002[37] clip_image002[37]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjPx5OZ6ecOPjY93RPEE91uCxdS-vFQhwqOGoNzncXwXdGniR0R86TRTzof7CbWAtia-wo9BX2gtXkZgPCKbl4lvOuWMcxoOMKfoCW-V3-uzJcXFTxX8Ss8BG3hN2hvBrUnocnR91k_jTiu/?imgmax=800)
![clip_image002[39] clip_image002[39]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhLTXBjmXa81Ppqlij7uQYSPmdKbElW1q69vc_1xtFg0jmM2Md_ue6zcfKZoZ6_qN0cESPjwz2iaxuuHTK7Gd8y1IjZM0t-YX8-YQzHSDQpKZrV_tRaK8sijvkQCeJEX917U3ohh6X0IWL3/?imgmax=800)


![clip_image002[43] clip_image002[43]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhDveomQghlM_0UQdmzIK_AHrHdtSDu08LRGqwG7HJtjgwswrQpc7jWPkcRn0PkO1i0h7AMb3XVu2Knq8wb-HLOOnvFkYwt1va4w5vHSE3gOLf-BOLV1nw8RvolLCb_Z82Jw-7PGH_dhbVJ/?imgmax=800)
![clip_image002[45] clip_image002[45]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiNnXTvpbybfxRvuhq5exTbgOyxxuZc90QvM4bEcI_BDRWqv3XyLiar68EQgqpEuFFn1TTIq4rcD09j7exScHYfoKe7K5G7TneY-68Zkrv-yZR__COYCCkyHaQ5rXfH6aW9u4o6JqAOVmks/?imgmax=800)
![clip_image002[47] clip_image002[47]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiRNcw5MDZTTsosB7hZ_y5NOISNP-5WUPa__8dRx-HgQJlL1OvE7Ofw3PKDftoP-akMZ4q27v12tNGidfeMi2FGnyTp1brsmemduRabWF9n1uooe_X3FV-OwEI6eYqpfXz74Hpz6Gu83BPP/?imgmax=800)





![clip_image002[53] clip_image002[53]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhqFCjquQdORc53m6qs9U1QpIXEUYRhCLXfC856HvkVLb4hS-gGsjhTJr-jD7sJ2o-ZYKB8UX2Kdvn2vIlWhHRQsF22V9d3w0XhaaqySMBljleL19OQXHqTMyGUgoAOvdOG6QBBY9_WS54m/?imgmax=800)
![clip_image002[55] clip_image002[55]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEisK-SIDv8R2kSZP_NAEe1m2PzxMubX4DqGO9ssm5Pg25XHczI4kzGpoqMeGMK3Vt-aoS07M4YpDJObR6r839t8L2f86IVaA7YIqjucSBwP3trxt9OWWPxe9fgyQP2dW3IlMF4HMDmd8V5k/?imgmax=800)
![clip_image002[57] clip_image002[57]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiTXF6rOUf2o5sEgodihRs60CXe9kFuZpMTZu4joW6-R5fr5wnNqM02qNVpVEcMYpMQ3EGjq5vGVP3hqkChiy8ml1EnnFf00jMVX-eX1mIK0ZNjkR8IHgnxVC0ScKOIfl9mF4d6vBr7fF7z/?imgmax=800)
![clip_image002[59] clip_image002[59]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiuYV_SodDszmakhFxUW4GP8qZGTuaFtIt0mkv0JjJ0TXS3EVki7UY_0ihYi6_W7YOt0UL-k6gf_THpHsWHDNkAxYo6TE-tR_r54p1b3Gz8-4ku3HjftQucBNG1Gr3OhqYmmhLc7k-WHncY/?imgmax=800)
![clip_image002[61] clip_image002[61]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEh2xbYpXcuDIuq9JMNlx_NpTZoN_Ynn21Le80Jr_ZeQOfjajKYVXBeX7i08mOlNzxAF_dGyDZM9mK7sum8QV6BVrCNINsBsM7lAMRAPjPs4R6ZnOpd8Qa7xpUOvGEEwXoYkCS3k76dNoLsn/?imgmax=800)
![clip_image002[63] clip_image002[63]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi_mXfq6-5uFgcTZzqOVzC2oZDY6QaB6_k9KEi9UgVh-Q1Zh1cv0_Rc-BwrcZGnE_4nuSQUkUaZ9sg-3Q31iCs7nNrfsNFJMmwwU6FKJGD3-OnnK_p6RATkpBEB27sgpD3DfAWUrsZcobPc/?imgmax=800)
![clip_image002[65] clip_image002[65]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgsMKm5ZGAYG3V_q3uQM4rVV_b7UKGlfjZ3KK_vImLEBFJiqeyq9e3gEcsyQKEF_h4-oTvq-AzPygilWgE7GUuXVPie9CMhirvIf_Oe_di1wgcwIPD5WoHLGI0QLCmUdIvygycLmekHJV5m/?imgmax=800)
![clip_image002[67] clip_image002[67]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjQxDfQA4jEQwKZseoSUlkxRAS70NmOjh0oM9YE25luMynK4yhNVZlPJKzI7ikZPzasYiQ5IcsMTMad97vJ8X5IVoIMLWq6Y5bZ6IDlTHXJZie6jBAzi1l6sTjzRtL-og9XFa7Ov4MWjGZ2/?imgmax=800)
![clip_image002[69] clip_image002[69]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiQjvu572I8Hy1eD-m9I2oA6iRYF7zo8W9Sd7THliDTLZxJjx_j3j0Ej3K8LYWrG1OHyZ5tr_ybbw5PBNoSO-yWP565rQIS-LHyKZM4Eh-6iCvFYrl5fIog2TR9MfwEDRP3pzvDts4marTU/?imgmax=800)
![clip_image002[71] clip_image002[71]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiMfm_t0Ipva_TNSisK42HBkGb66qId25pqKMmUZ08OzwheL8fd8p0Ft3Vsrf9b3yKGotcFIz6vkjnw_-erTQ28VhlE5vguORbIrnHM_3hAF4bGMdLTH9GGfNyf1WC_TBI1YWRLTde0tlTt/?imgmax=800)
![clip_image002[73] clip_image002[73]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhvuS8h4h1ORjZlT6gyPgLWOSeeqp7YnFEf8YRm7Wzd6B9wYayrP0VHBYE0UP6CnGlqZgkf1BvKZGBdBEv5r1BdLBjt1BDGRdZHpVPmDTUImGAFBvg7YMTcXxnEcYNlrnGbnZskHE0RgWIy/?imgmax=800)
![clip_image002[75] clip_image002[75]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiDKOlNubashTHWt1RMrb4Amwrb3UNJs2NVpQ36lRzqZ64nWMbZD6FOMNtv1p2qz3bA2I6p_2nOjD_JpnfOC4-1LpW1kHwn_wk3NEHPKBRGlZf_9yDkRiDNIv1y1TzEMREh8xXWNaKJGMh-/?imgmax=800)
![clip_image002[77] clip_image002[77]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhDmQpe8v1a5TxZMuqY8vuFmKgVwRaSxnpJk52Hn2WO3d43RUt8xFO6_9TzN4_CaTe20PD8ph0mnlFdfTPbHZPWu39MwU11yW_PMk50HqQBb7HWa9veVvMPouoxA5D4oFuofZZA-qs_bmJw/?imgmax=800)
![clip_image002[79] clip_image002[79]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi5is4j99T2VWIL0YC28r1CUxKi1c2WsnX-zsB4gF1VkUrKBTqut-Fwj6ZVuovcHIANm7jQagjWPRrPCxkp8yYYIPu_j2LcslTrXS-TxgNCbHnxaTNOlYPrFgSdcCOoci1bF14QqRPGB1cf/?imgmax=800)

![clip_image002[81] clip_image002[81]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg5xeLzu-gxOoRMuTchAaMz-ZpNuGOEh341xceCphFYB7QnpLW7Q7sRFcgiOTl3EHrZw_S6oWDYPe84oHEu3jQvSv-yAlRf0lOI5EZfT3Yf_VP2mAj97aINp8Jih_n7Q6BPZ_2BCZtWu1iK/?imgmax=800)
![clip_image002[83] clip_image002[83]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjxpD5dxPs2l3Kg8cvemAphzp4w6bRm-4l2T-nH1nuWLcFEX7iuPkDbkb1owtHHGc7Oe3Wzxan0ASotkO_Y2c1VB4qX1i8XFMTfQKEsfe-2r38CuGWS8hi0Akab_1gU9MRcMJRNPhQZ9-Vm/?imgmax=800)
![clip_image002[85] clip_image002[85]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjuKE0Ia0_DsoW1hGcwFUqvU1AcvqfwlgahsrC5IHCvW2PTfLe0HFP5SwSsUk1_imBO2kT5-pn14eFpjCoLAQYgWYDZ_SX8bxPsEpJUy46UDDaLpbM5CgBEyg5jFNkeeOCR_DLQBFUZcm3A/?imgmax=800)
![clip_image002[87] clip_image002[87]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiXMKl0wW0o1TUwDADfqQ83AFSlt8cPZYQb57igFoCNhTfYVmQCaYfY4nfqWHy1tDrJ9C7JgiY1eSkXGQSpGqypzLJr4ieR42TbKvEZqNUt_4qpLLj2P7kWOkLp77fPs36j8-yflmnBtCrC/?imgmax=800)
![clip_image002[89] clip_image002[89]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiGe4phP34tQVh4pi2bR4ngOCFo_bAnp8rEaPJ1wglzFYRWDisQwBqYpJjgRtnKYiAP82Hgtr-XDZY_oAe4kqB54kg5kzLBtnf_rWUeAt3YxG3T-uj29b45NznbR0vScmnJyPp1c7nZJEri/?imgmax=800)
![clip_image002[91] clip_image002[91]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhJbODSofeElBc9BRF5OkJZrd-jfNJ2t9SshYTV3eskRH4J2Tn1VbpprndW23ghujM_OK7nG8Z9S5O_wpTxZzp3EyA1nhzm6pefoiZo9jv09cjOZo6flEQYG71k2yzBwpNOneZXzSb5z3JO/?imgmax=800)
![clip_image002[93] clip_image002[93]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjlq3SVGsn8kRBxuql6a1GkZ3UTTYnj7HvLEg5e1tZWk-3qzvnXZDZ7mkSDULZv0auhdXIlQIYT3Yesf7qEoiLYYN6txxzmi52oyqpchw1PaXm5abKy7LfedBkkdzid2EnwV2kDr4C8HFWX/?imgmax=800)
![clip_image002[95] clip_image002[95]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhD89fMxa-yOkAUaRzvViEvF20OxaJUiixczDhO5S68FV5vFl4CfSQWf7mLr4MoJh0L0CAaI4JXGYVW92-0t0X-MX-5PF47CAxtnm6XLkgWXO6ntlRKOr1zY0r-XZQCjs60qCMFUfUzklg5/?imgmax=800)
![clip_image002[97] clip_image002[97]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgLxtx9uFK_jYCkxaMpqikNzBK4V1A5_iGvIjhMD_gsxh517hoybd846H1EUmKmFw7etXAfTCiGMhMVuRmtalxuIm0yXleQ7VqoPUhcgg2cr0NWvSzWpwD8d3UfxpDjBOJ3IDUhjapkWxHo/?imgmax=800)

![clip_image002[99] clip_image002[99]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjaiFz6sNZzcg2Y8UmnNy5e87hkT4LPyMEnTyyEot0rR8EgcWN6H7fOvNGghilpKbxcKqDZJl6A-jb-Y93Z5DdRmb4HCpQYyIuSpWDNUeuM8b0AcrjJ-MDhoON4tifm8uyh1kRJTHC7MZZ3/?imgmax=800)
![clip_image002[101] clip_image002[101]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgUaIaUeCCCPFXYs-G9Pj6nk1uMr_lAiLErkbWPygMN-l8mFFi2XQULeFFV2TkwTjKl3I48EJf6hvRpvteoJ21U8KjywLGbJOlnn2H4blf_-tH4Xbj36WElORqYTxCa6iHEKjghoCFR1dZK/?imgmax=800)
![clip_image002[103] clip_image002[103]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiS5GnopLz_roz09_Xp0QbQELdMNh58ELSPGX4b_X3IavRtU3Zo5_XtTEMCS8TFHGUCcYR3nhoZF70TOOmFGZqNKZdRpgMFfq7xHgiaeQzjf4O6k6O8WlAfuuXo_r9nu62DbN7m_QpUVr0R/?imgmax=800)
![clip_image002[105] clip_image002[105]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhOGRRvzBUuq7mswORN7K5mX1wKQADObhM-Hetgqs9iZsqFJCnmltUm4ePceTyAyvjGTZRVEEyzMJMoaLDkW78-SW5iC-DMIJ1aE4lXgUtjUh-qvEdquRIiogRTE_iNC5kTHkPU6LUwt0ma/?imgmax=800)
![clip_image002[107] clip_image002[107]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiVm1-dFarGI8B63cqaHSKCsaZnNBV7pQBtRzk60boD21hSxlODrf0VIyw0ZGxl6KfjS-RWo7RaJgkSS1ZHP4cW0LNZnEjuEcIknEw6koh0XhOvEJ32qrZlBImvr_Um9TsDxaV7KupN3vEm/?imgmax=800)
![clip_image002[109] clip_image002[109]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjnnmZ_HF0HWNPyYC7ZK50pCSqVDBQpPSCWP7XHLSdYmYVzHhxUqA0jXHar3sx4Nh6ygMBr9dwyqVHtyJeDEl2BmfrAWDJ3cgT4FZEL0BJB_KAp1g8CkyudeImp64BT_p7WzuQ4QrXuHuxS/?imgmax=800)

![clip_image002[111] clip_image002[111]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEif3-pJAhZ7DWYCACd3klnig8XNkGPDKuFUpma7pQm6to4vB-Gc2qaRG0T5us6_d4cmbRmMcaPo2ir_gDqKLytgyU8A3nSmea57ZfAKww58L64VSKeSTzElrl1mM7YpvvgFnj9SBk2Hb7oW/?imgmax=800)


![clip_image002[113] clip_image002[113]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiFyC65NI0tX84wuDhuMkLFR8HgyDS70iPdfCNjPEjqCiuDIM1DDvwKtTfRa2Z5WdKAOXh3T2ZW48mp3_5_RHkMRkTi8wfYQJTBxfFq2ssbNnL31A0CnLo8GT5xIpylMmQyFppLqgZU0GFN/?imgmax=800)
![clip_image002[115] clip_image002[115]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgUd35yEceNvq8R9CaiUzwsZYsM2RTWjV1TlN0C-aL4-huTLZX0r_W0g5PMi_AbTUjg_Jkrtf-zCbVgzV513LiFbgQGI_ASjCCg4WVPPh14Z-KgXaQytp7dbw81yMQwIHCl8OqaNrhOBxVv/?imgmax=800)
![clip_image002[117] clip_image002[117]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi1BMAFkDFzZdvKFkRjRsmbEf9O6r5ip-Z6qs68h61WcqiXj7AkTYOdNclwSqK3uWuC5CWwCLAYtyWErHLVOEpKNNvDmwWfr2VqXOk1OrlVU3VSKKHdpcJrcc62Bokowy2Cw6Dlcti2eQNH/?imgmax=800)

![clip_image002[119] clip_image002[119]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg2xBmbBu4HpjCqEqpJNQyAkylKjNu3ezx6z6JZaVFOzH3aBu-iyjJPYGCacuaJjq9R-ZJxvGPzr_FLQnIV5cXTeCLfVpSc3wQ-_dbXtYPUKYEO_oBThoQB6KeiL4tb-jmLX9l721PPxmmh/?imgmax=800)


![clip_image002[123] clip_image002[123]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgfB5GvpGIghM1_L_GhyphenhyphenAd3Rw_Rjgqh8xdtGF0R-WrSqoioULBk7jTme3xHzEd8om-PXmUtzM2Y5LbB0Zs1bU-fNEtMzvanEddX9wuls7jjSeg5V4oJw66EoLSYy7ZUVnU-5BGHv9iBrxEB/?imgmax=800)
![clip_image002[125] clip_image002[125]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg_hijW0oHJxD7Tfvc1MPgNb7QHvnOac94re1TQQgvhgN229aOxWviNlnqQViHrefIcKXxdXhsP1GbYvRIr2vHEBTSABoapjFTNgfD8ZwGgRZzNouBSa6AOsoNq40RXNEzFizQaoCBcMlwb/?imgmax=800)
![clip_image002[127] clip_image002[127]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgD1hVrM5mNvbk22zz_Lw-eBXdl4FvPV75b1AlKO6xRtqGV_-sCQ7QZaPEffpKRAyM7wLIvggBgamm6E8UrtcAfLMpFS8rsBUusCmc6HY50TCOhqsdeRQnVo5MK0I6dxDjdmyE1_JZ1TZBn/?imgmax=800)
![clip_image002[129] clip_image002[129]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhKVeNCqgQ3x_ckC_Ka5XTvWk64tvMHV6IPAJDGKW1O6rZCKseCu5pNvfntFPXuTdC_3i8RGZ3J01bjvBLXUwyMgvIkkRZhzQX0ohhI8zehSvHRrPuZDcAyumf8ZmvTqAMf6Fgj9T5QDHkx/?imgmax=800)
![clip_image002[131] clip_image002[131]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjCuhZ0KJP0WSB5SfxXVvlZf1fw4fn8NU-OXqKA2VIkZm3PHqF85CGIZQjDI-TPTO2n800C46Xn8L7s_QdWfez5hO1PMaRhQ-zg0PtwsNzAXAyaEx6ovdYENEk3kQ5PgGzQUpTHriiVlVyp/?imgmax=800)
![clip_image002[133] clip_image002[133]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgoFt_EDgNMWHSbv2gk6DUz5q5NLlhjbOqXdEYBQDiiZ6N_qHcE3P1Kst433L7gYOnZeXnSH2surPNiFAzPVS_dYf27D7fsnlVhG-h7cCxfCLAPAvs98rNdX_yCFOKRVXuCM7pYVT6VeuxR/?imgmax=800)
![clip_image002[135] clip_image002[135]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiPQXhm49Pn8e1LbH4Y4_b99Qig_jTAKCrnGvBWMfLmUOTz50u6LieLyqhNfb2e26UE_M3DyrrKP8xmT6DYcmORtNPP15rHtYIp3S-MelVsF159Z1CvCl2lilDGBi3chtXJu_34XUDSPMDj/?imgmax=800)
![clip_image002[137] clip_image002[137]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhnda9TY-N9LvxXzWZQ3tow3I7hoXuS4aBMSxb1u8pLJRcDk1OtqVWl2IBGbtpWf6f-524wVWSs61b7L_I2pf5how7XMYL8E38adt8-C5djyKe66cfcH4tLYMFSXUQgH9r_T5a094yBdoRk/?imgmax=800)
![clip_image002[139] clip_image002[139]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhsb4nIzh7gn-Mb7vIH2vNfTyja2urSuD1Y574OtJJccjfAslKYLbFKQwqJxDWfFubezS6gF20QWEBkgYuekzJfc-FlK1JpEW2g4jxxGMxrrAScIL1MLP9KcntH6MbSxVCk_51uGNTErwLq/?imgmax=800)
![clip_image002[141] clip_image002[141]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgYGFh6lq97wwHuSHJ-H7UCjXwCTW04DhbI5W5K9wBaTl3_Y-bNUwKYpk9KCoYI-0jyr1VHNzQSx5J_ZO73_llm8PVKF02E5suQz8z7A5RzaatBI1E4jhuDmDvoKC0eyb3yU3gTllh8wZPl/?imgmax=800)
![clip_image002[143] clip_image002[143]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjjE-jeyb_ybepEpJ5aQoKJfX5VQw_D6mNNDMgpyb8PpbjIAvSNn5U9cuKjW3t8vKNfKXzIKn5FjhTZP0ScAdJ5H7vD3nI4HO4HqV2W8DlAfNYhVYFVZEplUnSmWZFyjpFSA8BLioUGiqla/?imgmax=800)

![clip_image002[1] clip_image002[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg6bGKVNxWHkigQi6alqoNJKDma14wOBRvQjjXzrvD3h1qeErFyto9zTq9EiClTCb2rlfqADBmf5XuzDNs8-NR_z_cRw9Fqn3gRpoWFY48ZISPkk3D2G85r9RoGzipQ9Ri85aWHRZrPYM_C/?imgmax=800)
![clip_image002[3] clip_image002[3]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiNu3ZUU5gEJTq0wNPDs3QIuh8eG7RZWHZkvD8TjVTh8aBeC1i0iYpHjlqJhYXM8wip9tGCcemZDTPGiZOfigMMhPU7R1YVaCk2zw93X64O_1m7a2MAOMEQ4_2HyNjjErFuUM05LbQTDty1/?imgmax=800)
![clip_image002[5] clip_image002[5]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEho9F4m1CNIU0eoBJhp2q4a1Ijr1e5Kfk5GmToEQ32Gxm7etSLTW8qOhsgxlO6fwpCEJUAz69wcBilvxsXozl0uUXgUxhe4Uo7E28afooxdPJ2oshbObKbpbLA8EONfAwwmb0wFMPH1I5d2/?imgmax=800)
![clip_image002[7] clip_image002[7]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhBtPY5i99b8X-2UnGYwSWD529ofoxfi_GLxiwdJiQQGCi_OHkDGyorZbf62KR_4IWwIkTtxF6uURlgjkvxoHgKu0P7SlpJgLgqcGw3dsDg1wqMhDMpUp8D_ygQmcVa7YZBBm2M-Gyp45oP/?imgmax=800)
![clip_image002[9] clip_image002[9]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhReDbohI3sbr2y6osTjz0DzowK03OK0LHFBVKqb0wZ-hUTKcfyoivrYxEgeIjYA3V2xrm_wQAwWjBk9_pg2zLaR_be-0kZpxH0A_SwuKrBcv262LGgSpCD_Ydl8lv8p7RojfNc0t0fEJiD/?imgmax=800)
![clip_image002[11] clip_image002[11]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhfQE8YwZvl9IKuj4fHsM6Jn2ZQXSEpeNjRneFbyOVvsdBQrRPi4ikIwQ6iA9ZilWblTHBznyMk8owwmh9NhbA7Xavb1eQOvsqZzAOvMWA-3UF7WgxUHpTUBQkoTsIKiF8Q7OZkpeo-Y6Xd/?imgmax=800)
![clip_image002[13] clip_image002[13]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgKwSDLAcybJftRx4Tw1ZirxfuIX0HaJZRwmPuekVKIzmXgUj1uJzfVhjdVGV8Gvl88M14AJkDf90Zx7UGQsNlSC9Je3AdYME88ukdnYbsDT2oYGqd2pNZYPezv577D4YZ6Bu67AFA_jGBR/?imgmax=800)
![clip_image002[15] clip_image002[15]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjzfhIYWiqB9sh1ChtgbFCDeUwNkTUni5kXTNvVQNNBIxx93wsfoHh4xn_XkJBqOn_0vY_aChTtsF44RlYT2K9AyHoDlhBXCAP3WLcshGlo0Gpd8VM7O5OYmO7_V8u-cBLNLeF-BghuycTG/?imgmax=800)

![clip_image002[17] clip_image002[17]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgfBl-K5EKgSwPEzQOz1QXvY05x1ti48hIdEyMfgQwA6u6yT4NXO2FxInZ3lTz8LOTjw6jojwc_x43zUpvq9cYDe_iXXhuzIMWH5pU1HxKmOl4wfHsmoqXmSoTUJbleolI7dkaGkBMpvX7Y/?imgmax=800)
![clip_image002[19] clip_image002[19]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhBAsHCZIYN4c-s5zObH9pRYXbpBBDZVRmZt9RUz0rlDK6fOqmFhUcptUFtwm3wHKTrv44nOLm8gYHsJAntqnAf-_YU4ODCkpo_PrZeuYtx81fhWNw8Asia_3keLLfDi8tQo2I1ZKTBhIaC/?imgmax=800)
![clip_image002[21] clip_image002[21]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjqObDbXsJTBpluLM2qf9pL-GoFLYR0_szRqDP9vcu18-e1XO3Z2JjEIl4EXStaOSgJa2YdYWNscdBoqMlVbz_s2kYsJx7DYp-Lxb-IQY9y3d0WVrEAB3ElHJD5STEMsdSbLHQmXc5dhuPh/?imgmax=800)
![clip_image002[23] clip_image002[23]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgVGbH-kpStUUPVOo6IOnkWSJxt90Jbpwye3WIfIK7NCoBj90cCvJlKYt8oBwfmZxCshqs9sg-K8P89F_UFyG7ggcs81lztJF2L9GvHELa6cVXWQoTEcRMME1hz0IQ2tyzDBNth1oTc9JgJ/?imgmax=800)

![clip_image002[25] clip_image002[25]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhxLPpdt9pKdKGWyfdGVvipX4ljnG5teQs3Im92mJbDYYiZC99cC5bapuwKEf4fwWdKdqroKgr_Gh_bvElKY6AHKuROdU8E_YFCJYB4PdWh7HFKv_ONJgJReWOFvIcx7YM8OpsR8Gdlux8Z/?imgmax=800)
![clip_image002[27] clip_image002[27]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgQUZIG2Zk7rbv82rzR1S_DY3TUqykgkC9clycwGNSRqsDBC_LaLmf-E3XrUqDpnf4z7KeANOW5m0w3PIjjDkBcyMj_LAP55jdPuQO82rbJBt7Mx5_vSX92RlBEmdglQb59B49CXk77wivU/?imgmax=800)
![clip_image002[31] clip_image002[31]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhuEknJTNtjXnJqHI3yQas_5cC2Oh-jbDKY8wyk8orJw3cUXkh22q4PVgs3oh2NVp_IH3-jKcOcLDmPH42KprlsUadYARbbSeP1r6GzcsKk8Y0ALwUB7fsEvQE3imei5AINCDGXxhFqxm7M/?imgmax=800)

![clip_image002[33] clip_image002[33]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEj7K8QGDAE8FTx0cC_MqgfCLpAtK4BjTWQ-K-EotkaZao73T3z-WA8fculaiePBR0Z6IfB-F8HAgY4SYDcaju1mGNj-pd3sPXjAs5UBt3eyrQISHQ-rgWVPuhF8UxeEKlDdGL5PqM6GTEiH/?imgmax=800)
![clip_image002[35] clip_image002[35]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhJeJIziVApVw31hNagnaWQGPxvvumG7R5IiIDtXaTKg4zYqKi3vGbXXSX7eyFrPchDH__NkcAEG4IGOA4woMedXXIdQVWlvZPr15S1ccDJXgb3Yq90pAav-QEKZyyjnZ2y5hUBRA0WTC8h/?imgmax=800)

![clip_image002[39] clip_image002[39]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhlv6Xcy-UtUaTNdGTfoQy39v1B4TH_MYA1A1Tfq7Zjqx1BnrPgcRiAvUPVi1QWw1MdKt4y5pNOQox7wh5vIt0xDNJazhrzvk-Kxb8IRAPF686mhiEGWgIvU5c3E1B_8guxGnb7n3_SUwRB/?imgmax=800)
![clip_image002[41] clip_image002[41]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg8W5_WJZyotUhyL0Xup8vYuyHgPLhBWy50GRcd2XzngZaFI4FPabMMFUUxRJhn9xmdXXgEa1Y2SViqkRu7wCAP5WdjuwmHqNJHUEfAIsISg6RAxF0kAG0h_awwox2keShXRYcLwjSptpF-/?imgmax=800)
![clip_image002[43] clip_image002[43]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi_HizAHhmHiN5sMWtmUYM86OtLy4toNjCpw4-Hm8waGNn2En8jzi_XDLqj5Gj90lCd8-AUNPk9jkLVeuBo7Dp7_jVSqBY3gMj0lv4YBMRBC5_7WTS8kCyf83zpwOxSAPe8Gr7n6B9zj1RD/?imgmax=800)
![clip_image002[45] clip_image002[45]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiYGEOLjqcfOoVcQPfee_kBlKJJyixU1HIye3ofO_mpAHMMM9571xOF64at7zSwjucyanNEWRXwrObdjYKmBL4nEJMWLgJKAENTUEUaXpDBvVUo1tM-1u1eo5LSBcZQWB9vlu4XEEhbSFHF/?imgmax=800)
![clip_image002[47] clip_image002[47]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhGUf4SCbvZaIoTKZaCfvfMy9BWLupb5L08-pnfOLJZtr0wRTV_VZB3Nw2t9NmZCUPpcj_oxi2nEPqVPbo26Arr06Wr9FM5iHRSmDm4s_0nUdG0qgKRbK-vdhTxCIhRGFeDcyiI1i89tyPa/?imgmax=800)
![clip_image002[49] clip_image002[49]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiO845DnAyJkMyQlHxr-K_u07PX0wdG8sBZGWO9OtisODgySExtwNi8M4wifzZrPmlgfz5HyNDl-4lKVh0xMMqMi4anQdMFmhjdrbnL5r4rfVn-bRWFPmtFWyDZhtgdpD68Yl10k9M_Zu4p/?imgmax=800)
![clip_image002[51] clip_image002[51]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEixtMALejVhR16kNJ_SPp25aec2pigzN8OOGyWyAxaGO0AErotFNmFtOGvOT3A1B4B3SpWle3f0cmTEmwc5Yps3l3xU-aGKOcF6FtJH7zal9YVuy6g3nPJUpk7nUwONOQAYDNWV0IouYrJg/?imgmax=800)

![clip_image002[53] clip_image002[53]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjPou-hAsCLpiUIVlQyfnDUZZZpfs-eBBLb280f5qAqUWs7yHAxtS6I1j1i1QLACmr8saPySQIkFNmEXCuenrSl5zdDIbinMpzlwBWi1wdpmy1RtI9zdZ3J8fyi_sBr4s2FVsw_VxG9OtkH/?imgmax=800)
![clip_image002[55] clip_image002[55]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjd5bEUAxZk8acd6al7DrxQFJGmtc9N93hqb-3oi5m7Qh4jIsp6HsgmAPDuaDPeixZJ1xZMZnOleNoBHbxUbWy01EHiTuPC1JXkesj5tj5Pxi9LiM3fcU8Az80IjlsVy6H4JFo4EWzs9xRX/?imgmax=800)
![clip_image002[57] clip_image002[57]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhV8lXkL8BoQPzCAEgnoIrJOIg5PfZFar65c7rRcsEj_4KyAqU2CU9i9fg2jXNWzCfqrSjG9WeY2pRciwasXd4LahQMw21HT1USR0xnkEAleILBS2T2Q6Wca-ddCPB4mCGpP1JWtgNw4UbN/?imgmax=800)

![clip_image002[59] clip_image002[59]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEha_nlyInE8tCN2R93HEGtaEUDMqJybbMH-Ywgmudf02PbBoNgpht6eErlMTUhKbkTgZXjrzor-qYU3SuypTS6S_ZIOiRos0aEXIMPF3-TEKPa0_wulsg_hr6C-u8yiLdk_QAXbMswLptTZ/?imgmax=800)
![clip_image002[61] clip_image002[61]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgQe6nG9DhAnxAprJMY_havylUPNRwtOzxB3Y8pdraY_J4MNGX7lWoYIR3MA6N60zKY6bL7leDVnadPATzX0vUk9sUj1ima-Y26JI6GIf0CJGZCJZLoVLIMII79nMcSCvc305G6QKe1lTR1/?imgmax=800)
![clip_image002[63] clip_image002[63]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiCfvEyPDSKTIyvOlU5hkQHpMRGLN9cvQRCIYNGTM5cFOKJvYEJmB9ugTUeXxdSf0Ya2RJjJv6o89GMjk5Tat2Zfkf4emSqgoePztOh3yaYsgusmEpsKt546FCuuOjQfI8zB3fQYthTfdfE/?imgmax=800)
![clip_image002[65] clip_image002[65]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhPsfPynkKRxKBK2eNwfyBWk6UI1zphfCwU5q3x91ByLov9YdNOvQWUToTyZds_GdGQs869HiK7QVeqfRyr3hylvi5pY-IxsPsM4EemM6jwTj4wqGIAMfRk6Wyh5eFUM0I6_w1F5kUZv7vD/?imgmax=800)
![clip_image002[67] clip_image002[67]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhLK2VeTGurVWhmhry0EPUcjakHCk4i6a2Cl6E1p4nDOlyqVQlLowAFBYMy8CqoXTfKi_HqjI8xgUGEql3GhgpWi7-ux3HTNL6ntppacfMCjfEclo_b1Yhg3olU9ZRv9lVmX8BLTg_ilpQi/?imgmax=800)
![clip_image002[69] clip_image002[69]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiDsvDV_PqWw-exMYqywBMJK-lXsdJzaUhQMWzJujFVTKsnNaz1jkHGLeXTMxlg-lD7-kL0KS9rtxCN_bT048gr_CkfXKBOP6tGzgeePzfsrGcMpmo1psEL36ZiC6pHsyA7RdQEqLOPIHEe/?imgmax=800)



7 comments:
Great post! But unfortunately I have come to a stopping point while installing SSO. During the "Configuring Lookup Service" I repeatedly receive the error (Error: 20010 failure to configure lookup service). I have searched high and low and I cannot seem to come up with a fix. The strange thing is that I installed it perfectly yesterday, removed it today, and when reinstalling it I am getting this error.
Any help would be appreciated.
Re: lookup errorm - delete the rsa database and recreate it and then go again with the installation steps
You can perform in-place upgrades on 64-bit systems from vCenter Server 4.x , vCenter Server 5.0, vCenter Server 5.1 and vCenter Server 5.1.0a to vCenter Server 5.1.0b. You cannot upgrade an instance of vCenter Server 4.x that is running on Windows XP Professional x64 Edition.
Federation saml
Publication is great. I followed each and every process according to your blog and succeeded in deploying. Many thanks!
VMware vsphere
Hi Terence,
I have a customer who is experiencing a strange issue. Please help me with the below issue:
- When customer logs in with his username and password on the view client on his computer he gets an incorrect username/ password error. Other users can log onto his computer with their credentials without any issue. This customer can log into the view client with his credentials on another computer without any issue except his own computer. We have tried multiple steps but not getting anywhere. Please help.
Best of all tutorials!
Congratulations for this great work!
Complement with some notes that were useful at times. I hope to help.
Solution for error SQLExpress Port Listen:
VMware KB 2040068
Solution for port configuration error 80 for vCenter:
VMware KB 1030445
Thanks!
Post a Comment