Problem
So you’ve completed the installation of the local configuration store, Lync Server Edge components, imported your public certificates and ready to assign them for the public services but when you do, you receive an error similar to the following:
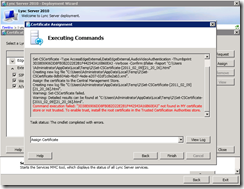
> Assign CertificateSet-CSCertificate -Type AccessEdgeExternal,DataEdgeExternal,AudioVideoAuthentication -Thumbprint 3D38E6906DD8FB0B2D22E2B1F442543A16B60EA3 -Verbose -Confirm:$false -Report "C:\Users\Administrator\AppData\Local\Temp\2\Set-CSCertificate-[2011_02_09][21_20_06].html"Creating new log file "C:\Users\Administrator\AppData\Local\Temp\2\Set-CSCertificate-8db604ab-4bd7-4ede-a207-02df1c8e2ab3.xml".Assign the certificate to the Central Management Store.Creating new log file "C:\Users\Administrator\AppData\Local\Temp\2\Set-CSCertificate-[2011_02_09][21_20_06].html".Warning: Set-CSCertificate failed.Warning: Detailed results can be found at "C:\Users\Administrator\AppData\Local\Temp\2\Set-CSCertificate-[2011_02_09][21_20_06].html".Command execution failed: "3D38E6906DD8FB0B2D22E2B1F442543A16B60EA3" not found in MY certificate store or not trusted. To enable trust, install the root certificate in the Trusted Certification Authorities store.
Solution
I’m not sure if this is new but it looks like Windows Server 2008 R2 servers don’t appear to come with many default Trusted Root Certification Authorities:
What this means is that Lync actually validates the issuer or issuers of the public certificate that you’re using and if it’s not in the Trusted Root Certification Authorities of the Edge server, it will not allow you to use it. You can confirm this by either going into the Certificates snap-in for MMC or simply opening up the certificate’s properties:
Notice how it reads: Windows does not have enough information to verify this certificate
Notice how it reads: The issuer of this certificate could not be found.
What you’ll need to do at this point is to import the root and intermediate CAs in the certificate chain of the certificate you would like to use into your Trusted Root Certification Authorities.
Once you’ve done so, you’ll be able to assign the certificate to your Edge interface.




3 comments:
i dont now what you mean bij
What you’ll need to do at this point is to import the root and intermediate CAs in the certificate chain of the certificate you would like to use into your Trusted Root Certification Authorities.
i have the root and root ca standing under trusted root cert.
what can i do!?
the intermediate cert needs to be imported in the intermediate CA, not the trusted ca
salam kenal bos. lagi jalan jalan pagi nih
Post a Comment