As we all know, Microsoft Lync Server 2010 carries the same model as OCS 2007 R2 where we’re required to have a folder share accessible for various services. While setting up this share is much easier in Lync than OCS 2007 R2 (the former automatically does most of the heavy lifting for you while the latter requires a bit more work), I’m sure I will find myself having to verify the security permissions of these folders while troubleshooting services which are dependent on them. This post serves to list out the folder tree and permissions of each folder which will probably come in handy if you don’t have another Lync environment to reference to.
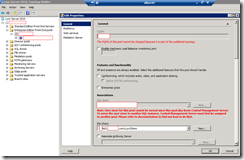
To determine where the folder share is located, simply open up the Lync Server 2010 Topology Builder, download the published topology, right-click on your pool, and choose Edit Properties. From the window that opens up, review the File share field where you’ll see the server and the share in the form of a UNC path:
Opening the share listed in the File share field, you’ll see a tree similar to this:
| 1-ApplicationServer-1 | |||||||
| AppServerFiles | |||||||
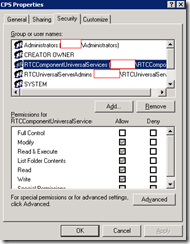
| CPS | |||||||
| PDP | |||||||
| Rgs | |||||||
| 1-CentralMgmt-1 | |||||||
| CMSFileStore | |||||||
| xds-master | |||||||
| replicas | |||||||
| <lyncserver>.domain.com | |||||||
| from-replica | |||||||
| to-replica | |||||||
| working | |||||||
| fta | |||||||
| <lyncserver>.domain.com | |||||||
| to-replica | |||||||
| replication | |||||||
| replicas | |||||||
| from-replica | |||||||
| to-replica | |||||||
| <lyncserver>.domain.com | |||||||
| tmp | |||||||
| 1-WebServices-1 | |||||||
| ABFiles | |||||||
| 000…. | |||||||
| 000…. | |||||||
| CollabContent | |||||||
| CollabMetadata | |||||||
| DeviceUpdateLogs | |||||||
| DeviceUpdateStore | |||||||
| LMStaticData | |||||||
| MeetingComplianceData | |||||||
| MeetingContent | |||||||
| MeetingFiles | |||||||
| MeetingMetaData | |||||||
| WebAuthStore |
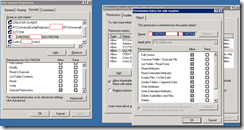
Since I was pretty excited about reviewing all the share permissions for these folders (not that I enjoy right clicking but more because I will be able to clearly document this for future use), I went ahead and did screenshots while taking notes of the permissions which I will list here:
LyncShare
**Note: This name will vary depending on what you choose to name it during your deployment.
All of the above RTC accounts have the same Sharing permissions: Change, Read.
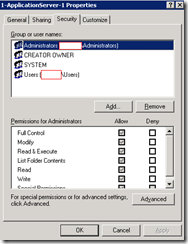
1-ApplicationServer-1 Folder and Subtree
AppServerFiles
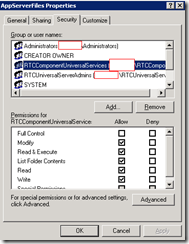
CPS
Both accounts inherit the same permissions.
PDP
RGS
Both accounts inherit the same permissions.
1-CentralMgmt-1 Folder and Subtree
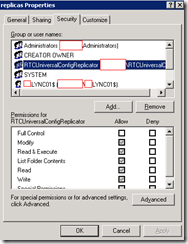
CMSFileStore
xds-master
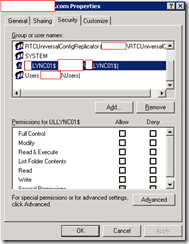
replicas
<lyncServer.domain.com>
Accounts listed above inherit permissions.
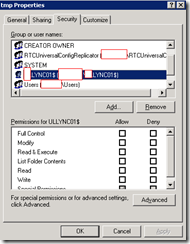
from-replica
Both accounts listed above inherit permissions.
to-replica
Both accounts listed above inherit permissions.
working
Both accounts listed above inherit permissions.
fta
Both accounts listed above inherit permissions.
<lyncServer.domain.com>
Both accounts listed above inherit permissions.
to-replica
Both accounts listed above inherit permissions.
replication
Both accounts listed above inherit permissions.
replicas
Both accounts listed above inherit permissions.
<lyncServer.domain.com>
Both accounts listed above inherit permissions.
from-replica
Both accounts listed above inherit permissions.
to-replica
Both accounts listed above inherit permissions.
tmp
Both accounts listed above inherit permissions.
1-WebServices-1 Folder and Subtree
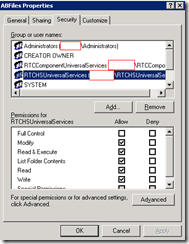
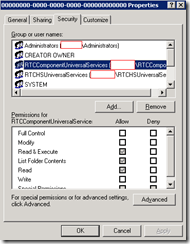
ABFiles
00000000-0000-0000-0000….
00000000-0000-0000-0000….
Account above inherits the special permissions.
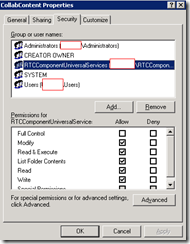
CollabContent
CollabMetadata
DeviceUpdateLogs
DeviceUpdateStore
LMStaticData
MeetingComplianceData
MeetingContent
MeetingFiles
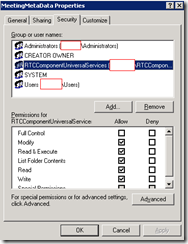
MeetingMetaData
WebAuthStore








































10 comments:
Woaw great work youve done, i have been looking for some documentations on this but not even MS have any...
What a waste of time. You just took the screenshot of the selected users. What about other users and their permission in the list?
i think this is useless because every server eventually gets hardened. the vanilla permission most probably does not stay long.
The purpose of this post as I mentioned in the beginning is to show what the default permissions are in case anyone suspects their Lync environment is operating erratically due to a change in the default permission settings.
@Anonymous: The other users in the list that I did not include are the generic ones such as "users".
@Sarbjit: I've never looked into it but I don't know if Microsoft recommends doing any hardening. I can see some administrators removing the generic accounts such as local users but don't think many would modify the permissions that are specific. I noticed that you're an MVP and I respect helpful professionals like you who give back to the community which is why I'm surprised you would use the word "useless" to describe a fellow IT professional's post that was meant to help others. I'm not taking any offense to your comment as I believe everyone has the right to express themselves.
Thanks for documenting this. It made it easy to verify that permissions were correctly set on the share during some troubleshooting at a client.
Thank you. Exactly what I was looking for - and now external clients download the Address book!
Nice post. It made it easy to verify that permissions were correctly set on the share during some troubleshooting at a client.
excellent stuff.
excellent post! just what i was looking for thanks!!!
A few questions:
1. What permissions are granted to the Everyone identity on the share permissions?
2. What permissions are granted to the local users group?
3. What computer account is granted special permissions on xds-master and 00000000-0000-0000-0000-000000000000?
Post a Comment