This post will serve as more of an update to one of my previous posts for the Citrix NetScaler 9.3:
Configuring Citrix NetScaler VPX (1000) 9.3 for publishing Web Interface server access by authenticating against Active Directory
http://terenceluk.blogspot.com/2012/02/configuring-citrix-netscaler-vpx-1000.html
… to demonstrate a similar configuration on a NetScaler VPX (1000) 10.
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
The environment for this example consists of a NetScaler VPX appliance with 2 network interfaces. 1 interface is sitting in the DMZ (172.16.x.x) network and the other leg is sitting in the internal server network (192.168.x.x). A CheckPoint firewall is configured to allow port 443 traffic to be directed to the NetScaler’s 172.16.x.x IP via a public IP. The XML broker is the XenApp servers and the port they’re using is port 8080. Finally, the NetScaler has a certificate issued by a public Certificate Authority and is a virtual machine on an ESXi 5.0 host with dvSwitches configured.
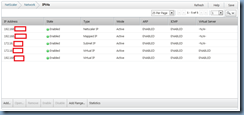
Start by configuring your NetScaler’s MIP, SNIP and VIP IPs:
As important as the NetScaler IP, Mapped IP and Subnet IP are, I would like to note that I’ve configured 2 Virtual IPs. The one sitting out on the DMZ leg will be used to respond to traffic coming in from the internet while the second one sitting on the internal LAN will be used to respond to the call back from the Web Interface server during authentication.
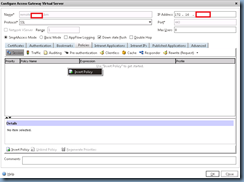
Proceed with navigating to Access Gateway –> Virtual Servers:
Right click on the right hand pane and select Add then in the Create Access Gateway Virtual Server window’s Certificates tab, select the public certificate you’ve installed and click on the Add button:
Next, give this virtual server a name and enter the DMZ IP address:
Proceed with clicking on the Authentication tab:
Click on the Insert Policy button at the bottom to create a new policy then click on the small drop down box under Policy Name and click on New Policy:
The Create Authentication Policy window is where you select the Authentication Type (i.e. LDAP, RADIUS, etc) and set up Expressions (i.e. TrendMicro installed?) which act as rules you have to check against the client that tries to authenticate against the NetScaler:
Enter a name for the policy and select LDAP as the Authentication Type and click on the New button:
The Create Authentication Server window is where you specify the settings for your LDAP server which will be your Active Directory domain controller:
The following is an example of what you might enter into the settings:
Once you’ve completed entering the information for your LDAP server and exit out, you’ll be brought back to the Create Authentication Policy window. Proceed with adding an Expression by clicking on the drop down menu beside the Add Expression button:
For the purpose of this example, we’re not going to add any special expressions in so we’ll be adding the expression True value which just means all or any client:
Once you’ve added in the expression, proceed with clicking the Create button and Close:
Once you’ve exited out of the previous window, you’ll then be brought back out to the Create Authentication Policy window with the policy you’ve just created shown in the Authentication Policies window:
Note that you should be creating a secondary entry or multiple policies with different priorities to build in some redundancy in case your configured LDAP server becomes unavailable.
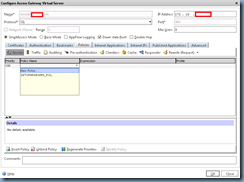
With the authentication policy created, proceed with navigating to the Policies tab to create a new Access Gateway Session Policy:
The configuration options here are pretty much the same as the Authentication Policy settings only in a different context. Here is where we’ll be entering the information for the access gateway to contact the back end web interface servers:
As with the authentication policy, we won’t be putting any special expressions into this policy so we’ll use the True value again:
Once we’ve added the expression, proceed with clicking on the New button to bring up the Access Gateway Session Profile settings which will allow us to enter our web interface server settings:
The first tab we’ll be changing is the Security tab where we’ll be setting the Default Authorization Action to ALLOW:
The next tab we’ll need to configure is the Published Applications tab which is where we’ll be entering our web interface servers’ information:
Note that the Web Interface Address should point to a load balanced VIP or virtual name that spreads across multiple web interface servers to provide redundancy.
Once you’ve completed the configuration of the Publish Applications tab, proceed with clicking on the Create and Close button to exit out returning to the Create Access Gateway Session Policy window:
Continue with clicking on the Create and Close button to exit back to the Access Gateway Virtual Server window:
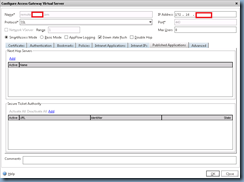
With the access gateway virtual server set up, the next step is to click on the Published Applications tab to list the Secure Ticket Authority (STA) servers. For this example, my STAs are the XenApp servers:
Note that the STA uses port 8080:
Once you’ve completed entering the STA information, proceed with clicking on Create and then Close.
If you’ve configured everything properly, you should see your newly configured virtual server with the State as up:
With the public facing Virtual Server configured, repeat the steps for configuring a virtual server and configure a second one mapped to an IP on the internal network. This web interface will be used for the call back from the Web Interface server during the authentication process. I won’t be including screenshots with instructions as it would look exactly the same as the public facing one. Once the second virtual server is configured, your list of should look something similar to the following:
Now that we have our NetScaler set up, we should proceed with configuring an additional site on the web interface server for the NetScaler to access so log onto your web interface server and open up the Citrix Web Interface Management console. I won’t be including instructions for this but you can see it in my previous NetScaler 9.3 post (URL is at the beginning of this post).







![clip_image002[6] clip_image002[6]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhqfS78Gt2Y1YGChqMmidF_iZzVqNuE1ofGYBBIsTj3ZpGW-8ho8Rw4MvIUQqGeJR4yxkFVNtIw2ovZ8Dyv5gZzF9HJDO4-0kEJiMexs12IKvv0shbtxWI7MFc3-vDTpgYfqXZ_P9ILwiib/?imgmax=800)
![clip_image002[8] clip_image002[8]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgGzlaMCs9R5ASmScWuoCDRV9yUmRAP2hmgffl1xee7JpPlIpHFhuuyU6fjLycZMt48Q_RPqqK0tL54gC0gA4ZaRgMDqCmztUfJ_T0JCGsNWjwBQXgo5zsNzx8TXYFvJ1jXpA9cBlxltUhf/?imgmax=800)






![clip_image002[10] clip_image002[10]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjt4LnMk4nLuIx0NzMyjPQhL0wX2qdR3jT_YSiPcxb7dxEsx7dNW3kzx0QRsw_XUqvYKktYzE5kdlUh9tUtNV52V6uVNn_U-HY-f25VEo7WwURHGzG67OjBYyydlJveAQb1ekwSKGnESAeo/?imgmax=800)

![clip_image002[12] clip_image002[12]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhBHSPVScXN8AX4kwJ5IlLUZUuhoL6d5naKcGjbvlp1FBAevENw6L9pBdnEjD9kbREeKm7b4GTqOWb5f8Rh7pe7psAGLDcPTgVKxfE1-G3r8XwJVmkNUwyEvIHu43-T3gFLbD80sG7W63Oq/?imgmax=800)
![clip_image002[14] clip_image002[14]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjcjG2H2marUo0XioxGPMElGHW-4O8FEoI8xPoxlrC6mu1EGR3TrWBqcuCwH5azSNB21Ewj7Wr9wnNGhqboTRTXc2FBqYA0pun6yR_8oX3WJYRjT3UmYCJtNUzPRgOKa2l5Al__MjYIM5bd/?imgmax=800)
![clip_image002[16] clip_image002[16]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEitvFqjboAi5AH9qZzW8mpvmaceKsGJ2wd75iZt8Sf-0T3wbWxVSVQlEpfKTaSjpf2kf6y6kHCb7HgR5MIw54hSz-FhbZuNkcd27BR7F6bs9cp2X-PqjEn5cfttu1xfWyYeCiMEN0xVI08F/?imgmax=800)
![clip_image002[18] clip_image002[18]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhms2PrX_UFVUKfULskMCjkRnXHAtdn8-DdxPAHkksW1CnAvv-iQmMK4Wi_3qDBI9HCQqv4BqaYHLoBvjhOwyHnVhQh6fIfm4_BgGG-VlYtDl5GICyg4MEwisHba0mSgVrXzGvD65KAWhnh/?imgmax=800)
![clip_image002[20] clip_image002[20]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiJ_yFHei1YS5wswziij96nXqc1DyLJM_7vV1EndAV6qLUvS0RzUCH8fY_pWBFP5oypU9LGTxNQAXNdCbvtez87zs_9gq3dIIyjIepkb074uu8FA0d_G8FUSC1AF6gfxJ0hzaVGLVLCFh0K/?imgmax=800)

![clip_image002[22] clip_image002[22]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEih5-G2mxQajuD5XimcJfe8Wszcs0H3O4RoXFF2kzGNerpFosU4H6eQw241KlXJz3jS1zkaYOiDHlLHqv2Rp1lGRaK63fBXM8mFEdzEOKKLwYty7jNtswOrZRvhaMnx8k1FQ4BTV3Xk7NdQ/?imgmax=800)




5 comments:
Excellent piece - very useful.
you give information with interesting facts thru this article. free antivirus download
If you wanna access blocked site then check this short method to access without any long methods.
access Torrent Downloads in UK
Great article. I was struggling to get AG and storefront up in 2arm Netscaler. thanks for taking the time.
Sadly I completed my setup prior to finding this excellent tutorial. But I was thinking...wouldn't it be wise to Load Balance DNS and LDAP/AD both with load balanced vips and setup monitors on those vservers.
Post a Comment