I was asked recently by an ex-colleague about how I would go about in issuing a certificate for a new and only Certificate Authority in Active Directory. I’ve always found this situation amusing whenever I come across it because, and I can’t recall if this is true but I don’t remember Windows 2003 certificate authorities forcing you to have HTTPS (SSL) in order to use the Create and submit a request to this CA option through the http://yourCA/certsrv web enrollment webpage. In Windows 2008, you are forced to secure the web enrollment page for the Create and submit a request to this CA or you won’t be able to request a certificate. This appears to throw a lot of people off when they’ve just deployed their new certificate authority and would like to use that feature to, say, generate a SAN (Subject Alternative Name) certificate which may require that feature.
So how do would you go about generate a certificate without having access to the Create and submit a request to this CA feature? Simply use the Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file or submit a renewal request by using a base-64-encoded PKCS #7 file:
The following shows the problem and solution.
Problem
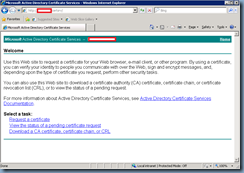
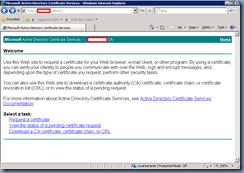
You’ve just deployed a new Certificate Authority in your Active Directory and need to create a new web server certificate with SAN entries for a IIS server so you proceed by navigating to http://yourCA/certsrv webpage to generate a request. You proceed with clicking on Request a certificate:
Then advanced certificate request:
Then Create and submit a request to this CA:
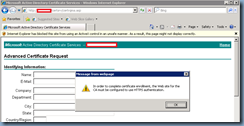
… but then you are prompted with the message:
In order to complete certificate enrollment, the Web site for the CA must be configure to use HTTPS authentication.
This shouldn’t surprise anyone as you wouldn’t want your certificate’s information being passed via HTTP. You then realize that what you’ll need to do is generate a certificate for your root CA’s web enrollment site but may then get confused as to how you can generate a certificate for this website if you don’t have one to secure it.
Note that some may think that they can use the Root certificate that’s already placed in the local computer store:
… but the problem with using this certificate is that it’s not the right certificate template:
IIS actually allows you to assign this but it won’t work.
Solution
The solution is actually quite simple, don’t use the Create and submit a request to this CA feature but rather use the Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file or submit a renewal request by using a base-64-encoded PKCS #7 file:
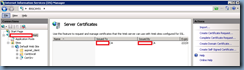
Open up Internet Information Services (IIS) Manager and select the web server:
Double click on the Server Certificates icon:
Click on the Create Certificate Request action on the right:
Fill in the appropriate fields:
Most certificate authorities, especially external public CAs, require at least 2048 bit length for certificates so you should choose that at the very minimum:
Save the certificate request somewhere accessible:
Open your Root CA’s certsrv webpage and select Request a certificate:
Select advanced certificate request:
Select Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file or submit a renewal request by using a base-64-encoded PKCS #7 file:
Once presented with the following page:
… open up the certificate request file you generated earlier:
Copy the content and paste it into the Base-64-encoded certificate request (CMC or PKCS #10 or PKCS #7) then click the Submit button:
You will now see the following Certificate Pending page:
Open up the Active Directory Certificate Services management console either through Server Manager or via the MMC snap-in, then navigate to the Pending Requests node:
Right click on the pending request, click on All Tasks and then Issue:
The certificate listed in Pending Requests should not be listed in Issued Certificates:
Navigate to the http://yourCA/certsrv webpage and you should now see a View the status of a pending certificate request link:
Clicking on the link above should now reveal the page with the link:
Saved-Request certificate (Some date)
Clicking on the link above will bring you to the following page:
From here, you want to make sure you select option Base 64 encoded then Download certificate:
Save the file somewhere accessible:
Opening this .cer file will show something like this:
Navigate back to IIS and select Complete Certificate Request:
Browse to the file and give the certificate a friendly name (I usually just use the FQDN):
The certificate should now show up in the Server Certificates window:
Proceed with assigning it to the Default Web Site and your certsrv site is now secured.





























5 comments:
Thank you, very well prepared instructions.
Thanks Terence, this saved my afternoon! Please can you add how to add the cert into IIS bindings for those who have never done it before :)
can you please clarify where/how we can add additonal SAN names?
Thanks for the great tutorial!!! :D
Thanks for that tutorial! Good job!
Post a Comment