I ran into a seemingly trivial task which ended up being nerve racking and extreme uncertainty.
Situation
We have a client associated with the military who has a lot of wireless devices that use certificate services to authenticate. The client had a bad experience with renewing certificates in the past when the public and private key were inadvertently changed during the renewal process which was why we were brought in for the maintenance work. I basically remember that all I had to do was:
1. Stop the CA service.
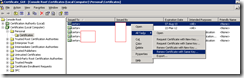
2. Right click on the CA.
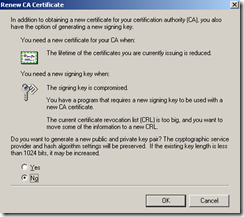
3. Select Renew CA Certificate.
4. Select No so it doesn’t generate a new public and private key, then click OK.
I also went ahead to validate these steps by:
1. Open Help and Support Center.
2. Type in Renew Subordinate and then search.
3.Select Renew a subordinate certification authority : Certificate Services.
4. Then review the instructions.
Being an Active Directory consultant and working with CA services on many projects in the past, I figure this would be a piece of cake but what I didn’t realize is that I don’t actually live and breath in this on a day-by-day basis so when the client looked at me in the eyes and asked me if I was sure when I was about to renew the subordinate’s Root CA issued certificate, I couldn’t say whether I was 100% or not. I felt that I was 99% sure but seeing how you do this every 2 to 3 years (when certificates expires), I couldn’t give him a definitive answer. This was when we reached out to Microsoft.
Solution
Long story short, we had the Microsoft Engineer review the environment and showed him that we can’t do it the following way as we usually do with the other certificates:
The engineer went through the configuration, asked us to change these 2 policies, which I don’t think it did anything:
Note: He wanted us to change the Not Defined to Enabled.
After 2 hours of troubleshooting, he went back to the original steps I had listed above and proceeded with:
Then completed the update. The certificate looked like this before:
…and it looks like this now:
What we ended up doing was compare the Public Key value of the old one and new one to see if it matched.
Seeing how both keys matched, the public and private key should be the same. I hope this helps anyone out there caught in my situation because as I mentioned earlier, if you don’t do this every day, what you did last year or 2 years ago isn’t so sure anymore.












No comments:
Post a Comment