I had to recently troubleshoot an account lockout issue for a client and as it’s been a while since I’ve had to troubleshoot such an issue, I completely forgot the type of logs that were supposed to be logged when, say, a user supplies a bad password, then the correct one. Seeing how I’ll most likely forget all this again, I figure I’d write a short blog post about the logs I saw that were generated in the Security logs of a domain controller.
Note: That you need to turn on failure auditing for your domain controllers as it’s not the default on Windows 2003 and older versions of Windows. The following example uses Windows Server 2008 as examples.
Bad Password Supplied
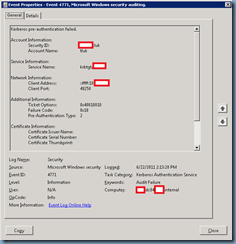
The security event that gets logged in the Security log of a domain controller when a user supplies a bad password is event ID 4771:
Kerberos pre-authentication failed.
Account Information:
Security ID: domain\tluk
Account Name: tluk
Service Information:
Service Name: krbtgt/domain
Network Information:
Client Address: ::ffff:10.45.5.44
Client Port: 49258
Additional Information:
Ticket Options: 0x40810010
Failure Code: 0x18
Pre-Authentication Type: 2
Certificate Information:
Certificate Issuer Name:
Certificate Serial Number:
Certificate Thumbprint:
Certificate information is only provided if a certificate was used for pre-authentication.
Pre-authentication types, ticket options and failure codes are defined in RFC 4120.
If the ticket was malformed or damaged during transit and could not be decrypted, then many fields in this event might not be present.
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
The following explanation of this event ID is provided by Randy Franklin Smith’s Ultimate Windows Security.com site:
http://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=4771
Result Code: 0x18
Kerberos RFC Description: Pre-authentication information was invalid
Note: Usually means bad password
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
Good Password Supplied
The security event ID 4768 is the event that gets logged at the beginning of a successful login:
A Kerberos authentication ticket (TGT) was requested.
Account Information:
Account Name: tluk
Supplied Realm Name: domain
User ID: domain\tluk
Service Information:
Service Name: krbtgt
Service ID: domain\krbtgt
Network Information:
Client Address: ::ffff:10.45.3.35
Client Port: 49260
Additional Information:
Ticket Options: 0x40810010
Result Code: 0x0
Ticket Encryption Type: 0x12
Pre-Authentication Type: 2
Certificate Information:
Certificate Issuer Name:
Certificate Serial Number:
Certificate Thumbprint:
Certificate information is only provided if a certificate was used for pre-authentication.
Pre-authentication types, ticket options, encryption types and result codes are defined in RFC 4120.
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
The following explanation of this event ID is provided by Randy Franklin Smith’s Ultimate Windows Security.com site:
http://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=4768
Result Code: 0x0
Kerberos RFC Description: N/A
Note: N/A
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
Following the event ID 4768, you will an event ID 4769 logged:
A Kerberos service ticket was requested.
Account Information:
Account Name: tluk@domain.INTERNAL
Account Domain: domain.INTERNAL
Logon GUID: {0b43065d-1d2d-973d-9ea4-2f195c65566d}
Service Information:
Service Name: GVQ6RH1$
Service ID: domain\GVQ6RH1$
Network Information:
Client Address: ::ffff:10.45.5.15
Client Port: 49261
Additional Information:
Ticket Options: 0x40810000
Ticket Encryption Type: 0x12
Failure Code: 0x0
Transited Services: -
This event is generated every time access is requested to a resource such as a computer or a Windows service. The service name indicates the resource to which access was requested.
This event can be correlated with Windows logon events by comparing the Logon GUID fields in each event. The logon event occurs on the machine that was accessed, which is often a different machine than the domain controller which issued the service ticket.
Ticket options, encryption types, and failure codes are defined in RFC 4120.
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
The following explanation of this event ID is provided by Randy Franklin Smith’s Ultimate Windows Security.com site:
http://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=4769
Note that you won’t find an error code of 0x0 because that means there is no error.
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
Hope this helps anyone who may be looking for the type of event IDs logged on a domain controller from a failed or successful login.


No comments:
Post a Comment