While I know installing the VMware vShield Edge Manager isn’t exactly all that exciting, I took the time to document during a deployment in a test lab and what better to way to use some of these screenshots than to write up a blog post. There isn’t a whole lot to during the install but for those who are interested in knowing what the install looks like, please read on.
Proceed with downloading the VMware vShield Edge Manager from the VMware downloads site as shown in the screenshot below:
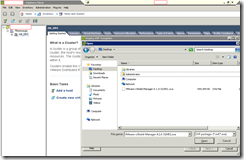
Once you’ve downloaded the OVA file, open up your vSphere Client, log into vCenter, select File –> Deploy OVF Template…:
Browse and select the OVA file you’ve downloaded:
Click Next:
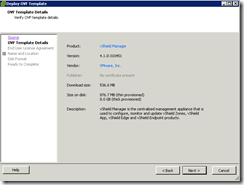
The details of the OVF summarizing what you’re deploying will be displayed:
Agree to the EULA as we always do:
Choose a descriptive name for the vShield Manager:
Select the host you would like to deploy the vShield Manager on:
Choose to either Thick or Thin provision the vShield manager:
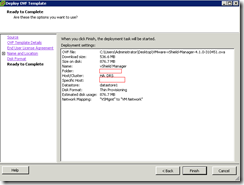
Review the summary and click finish to begin the deployment:
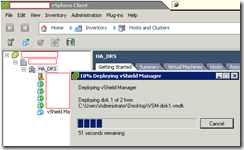
As with any other OVAs, vCenter will begin creating the virtual machine:
Once completed, you’ll see a new virtual machine in your cluster:
Proceed with powering up the virtual machine and open up the console:
The vShield operating system will begin to load:
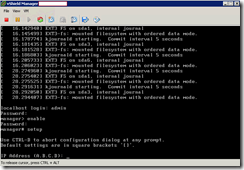
Believe it or not, it took me awhile to figure out what the what the login credentials were because I missed it in the manual so in case anyone is searching for what the default vShield Manager admin credentials are, it’s:
Login: Admin
Password: default
Once you’ve successfully logged in, begin the setup by typing:
enable
setup
The wizard will ask you for the following:
- IP Address
- Subnet Mask
- Default gateway
- Primary DNS IP
- Secondary DNS IP
- DNS domain search list
Once you’ve completed the wizard, exit the vShield Manager console by typing exit and log back in:
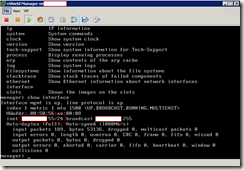
You can check to see whether your IP address setting was applied with the following command:
show interface
Once you’ve confirmed that the settings you’ve configured during setup has been applied, launch a browser and browse to the vShield Manager’s IP address:
Login with the admin/default credentials:
Once you’ve successfully logged in, you will be placed in the configuration page:
You can navigate around the other pages such as the Updates page:
The Users page:
The System Events page:
The Audit Logs page:
To complete the setup, navigate to the configuration page, proceed with entering your vCenter Server information and click on the Save button. Once you’ve saved the vCenter information, you’ll see the following message:
Changing the vCenter address may result in unpredictable behavior. Please update only if you change IP of your current vCenter Server.
Note: Please make sure you complete the vCenter information before proceeding to the next step.
Complete the install by registering vShield Manager as a Plug-in in vCenter by clicking on the Register button. Once you’ve done so, you’ll see the following message:
Plugin is registered successfully
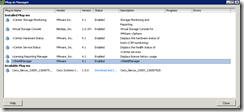
You should also confirm that the plugin shows up in the Plug-in Manager of vCenter:
Nothing too fancy but this should give you an idea of how simple it is to install and register the vShield Manager. Configuring it will require much more thought.