I’ve recently worked with a client who wanted a website load balanced by a Citrix NetScaler to have access filtered based on the source IP address of the incoming client. There are probably quite a few ways to accomplish this but the two that I am aware of is either through ACLs or a Responder Policy. I personally do not like to use ACLs for situations like this because of the “global-ness” that they are configured so the purpose of this post will demonstrate how to accomplish this with a Responder Policy.
Begin by navigating to AppExpert > Responder > Policies:
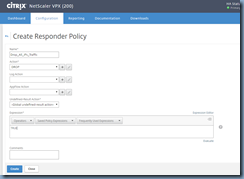
The first policy we’ll be creating is the catch all policy that will drop all connections:
Name: Drop_All_IPs_Traffic
Action: Drop
Express: TRUE
This policy can also created with the following command:
add responder policy "Drop_All_IPs_Traffic" TRUE DROP
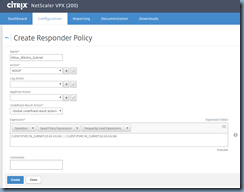
The next step is to create a policy that allows workstation subnets to access the site:
Name: Allow_Wkstns_Subnet
Action: NOOP
Express: CLIENT.IP.SRC.IN_SUBNET(10.43.3.0/24) || CLIENT.IP.SRC.IN_SUBNET(10.43.4.0/24)
This policy can also created with the following command:
add responder policy "Allow_Wkstns_Subnet" q/CLIENT.IP.SRC.IN_SUBNET(10.43.3.0/24) || CLIENT.IP.SRC.IN_SUBNET(10.43.4.0/24)/ NOOP
Note that the above expression allows the subnets: 10.43.3.0 and 10.43.4.0 to access the site. If the requirement is to specify a range, you can use the following expression:
CLIENT.IP.SRC.BETWEEN(10.43.3.1,10.43.3.100)
If the requirement is to specify an individual IP, you can use the following expression:
CLIENT.IP.SRC.EQ(10.43.3.136)
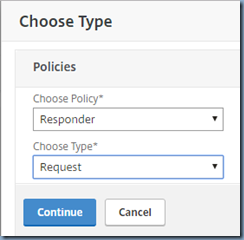
With the Responder Policies created, proceed by opening the properties of the load balancing virtual server of the website and add a new Responder Policy:
Choose Policy: Responder
Choose Type: Request
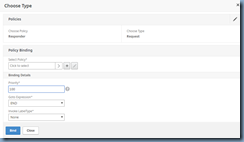
Proceed and select the catch all policy that denies all IPs:
Select Policy: Drop_All_IPs_Traffic
Priority: 100
Goto Expression: End
Invoke LabelType: None
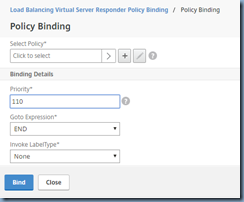
With the policy binded, proceed to click on Add Binding to bind the policy that allows access for specified IP address or subnets:
Select Policy: Allow_Wkstns_Subnet
Priority: 90
Goto Expression: End
Invoke LabelType: None
Notice that the priority is configured to be 90 for this policy because we want the responder policy to evaluate this policy first to determine whether the incoming request is from these source IP addresses, if it is then allow access, otherwise proceed to the next responder policy which denies access to all IP addresses.
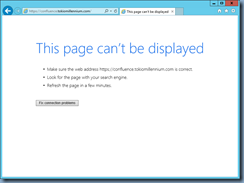
Once the configurations are applied, you should now either be able to access the webpage if the device is on the workstation subnet defined in the responder policy or unable to resulting in a page similar to the following:








4 comments:
Is your lb vserver IP on the same subnet as your transport server? I tried this responder policy but am not able to relay. the LB verser is in a DMZ load balancing the smtp traffic to my internal CAS servers. the CAS servers have the MIP allowed on the receive connector.
I tried and works great
This was very helpful.
Many thanks
Hello Terence,
Can we filter access based on the source IP address only for a backend server that is added to a VS that contains more than 2 backend servers?
If so, can you show us how to do it?
Thanks
Post a Comment