I recently wrote a blog post to demonstrate deploying Lync Server 2013’s Edge server:
Deploying Lync Server 2013 Edge Server
http://terenceluk.blogspot.com/2013/01/deploying-lync-server-2013-edge-server.html
… and received a few emails asking whether I could provide more information about upgrading an existing Edge from Lync Server 2010 to 2013. As many may know, there are various ways to perform an upgrade whether it’s a “big bang” or “transition” and the type of the existing deployment such as a single or multiple computer pool also changes the tasks that are required to be done. With that being said, I have done a few single computer pools “big bang” upgrades and will use part of the information from my previous post to demonstrate upgrading a single Edge server topology.
Before I begin, the type of upgrade I will be doing will require downtime for services provided by the Edge server because what I’m essentially doing is building a new Lync Server 2013 Edge server that will take over the identity of existing Lync Server 2010 Edge server.
Backup and Document
The first item to do before you begin with the new Edge server deployment is to backup and document the existing configuration of the existing Edge deployment. Begin by backing up the following certificates:
- Certificate or certificates used for the Edge server’s external interface – Certificate for access, conferencing, etc services.
- Certificate used for Edge server’s internal interface – This is the certificate used for the a/v service on the internal interface.
- Trusted Certificate Authority certificates – Ensure that you have the root and intermediate issuing certificate authorities backed up so you can import them onto the new Edge server.
Also document the following items:
- Edge server’s public facing NIC configuration – IP address, gateway, DNS, etc.
- Edge server’s internal facing NIC configuration – IP address, gateway, DNS, etc.
- Edge server’s static routes – Static routes required for the Edge server to get to the internal networks because there is no default gateway assigned.
- Edge server name and other configuration settings – I personally prefer to just do screenshots such as the following:
Remove the Existing Edge Server From Topology
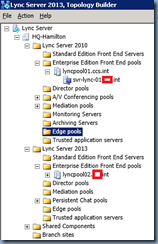
Assuming you have scheduled a window for downtime, proceed with removing the existing Lync Server 2010 Edge server from the topology by opening up the Lync Server 2013 Topology Builder, navigate to your Lync Server 2010 pool, edit the properties and remove the association to the existing Edge server:
… continue by doing the same for your Lync Server 2013 pool if you’ve associated the Edge server to it as well:
Once you’ve disassociated the existing Edge server to the front-end pools, proceed with deleting it from the existing topology:
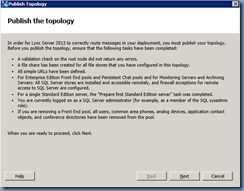
Once the Edge server has been removed, proceed with publishing the topology:
Shutdown Existing Edge Server
With the old Lync Edge server removed the topology, you can proceed with running Lync Server 2010 setup.exe on the server to remove the components but if you don’t intend on repurposing the server, you can simply shut it down.
Preparing the New Edge Server
With the old Lync Server shutdown, begin configuring both of its NICs to be exactly the same as the old server:
Internal NIC Configuration
This is what the internal NIC settings for the Edge server looks like:
Note that there is no default gateway specified but the DNS servers are filled in with the internal DNS servers.
External DMZ NIC Configuration
This is what the DMZ NIC settings for the Edge server looks like:
Note that the default gateway is filled out but the DNS servers isn’t. Two additional IP addresses (total of 3) are assigned to the external interface:
The external interface shouldn’t attempt to register with DNS so the Register this connection’s addresses in DNS is unchecked:
The external interface also does not need Client for Microsoft Networks and File and Printer Sharing for Microsoft Networks enabled:
Static Routes
With the NICs configured, proceed with configuring the persistent static routes needed for your Edge server to get to the internal server VLAN and workstations. Refer to the documentation you completed at the beginning of this post and add the static routes onto the server:
Configure Name and a DNS Suffix for the Edge Server
With the static routes added, proceed by renaming the new Edge server to use the same name as the old Edge server then add a DNS suffix for the server:
Import Backed Up Certificates
The last step required to prepare the Edge server is to restore the certificates backed up so restore the certificate or certificates used for the Edge server’s external, internal interface:
… and the the root and intermediate issuing certificate authorities are imported to the Trusted Root Certification Authorities:
Prerequisites for Windows Server 2008 R2
The following packages will need to be installed if you are using Windows Server 2008 R2 as the operating system for your Edge server:
Install Microsoft .NET Framework 4.5:
Proceed with downloading and installing Microsoft .NET Framework 4.5 from the following URL:
http://www.microsoft.com/en-us/download/details.aspx?id=30653
Install PowerShell 3.0:
Continue and PowerShell 3.0 from the following URL: http://www.microsoft.com/en-us/download/details.aspx?id=34595
There’s a list for 4 items for download and the way to determine which one you’re supposed install is actually noted at the bottom. Since we’re installing PowerShell 3.0 onto a Windows Server 2008 R2 SP1 server, proceed by downloading the following file:
WINDOWS6.1-KB2506143-x64.MSU
Install Windows Identity Foundation:
Continue and Windows Identity Foundation from the following URL: http://www.microsoft.com/en-us/download/details.aspx?id=17331
Windows6.1-KB974405-x64.msu
Prerequisites for Windows Server 2012
The only package you’ll need to install when using Windows Server 2012 as the operating system is the Windows Identity Foundation which can be added via the following cmdlet in PowerShell:
Add-WindowsFeature Windows-Identity-Foundation
Defining the Edge Topology
Once the Edge server has been configured, the next step is to re-define the new Edge server with the same parameters and then publish the topology:
Fire up Topology Builder:
Right click on the Edge pools folder and select New Edge Pool…:
The wizard to define a new edge pool will launch:
Refer to the documentation created earlier:
Select the appropriate settings:
**Note that the Edge server external IPs I’ll be using are NAT-ed IPs which is why the “The external IP address of this Edge pool is translated by NAT.” is selected.
Specify the internal interface’s IP address from the documentation:
Specify the Edge server’s external IP addresses (these will be my NAT-ed internal IP addresses):
Since I selected The external IP address of this Edge pool is translated by NAT checkbox earlier, I will need to provide the true external IP address for my A/V Edge service:
Select the Next hop pool to the new Lync Server 2013 pool:
Select the front end pools you would like to associate the Edge server with. Note that this environment still have users in both pools listed so I’ve selected both of them:
Clicking the Finish button will bring you back to the Topology Builder:
With the new topology defined, proceed with publishing it:
Exporting the Topology for the Edge Install
Since the Edge server is not a part of the domain, there is no easy way for it to download the topology during the install which is why we will need to manually export the topology on your front-end server and copy it over to the Edge server:
Open up the Lync Server Management Shell and execute:
Export-CsConfiguration -FileName <fileNameOfYourChoice.zip>
Copy the zip package to your Edge server:
Installing Edge Server
Launch setup.exe from the Lync installation binaries:
Setup will automatically install Microsoft Visual C++ 2012 x64 Minimum Runtime – 11.0.50727:
Choose Install or Update Lync Server System from the Deployment Wizard:
Install Local Configuration Store:
Select Install Local Configuration Store:
There is no option to retrieve the topology from the CMS because the Edge server is not joined to the domain so choose Import from a file and locate the zip package we copied over from the front-end server:
Setup Lync Server Components:
Once the local configuration store has been installed, proceed with installing the Lync Server Components:
Request, Install or Assign Certificates:
Proceed with assigning the imported certificates for the Edge server’s internal and external interfaces:
Start Services:
With the certificates issued and assigned, proceed with starting the services:
Check Service Status:
Every though the last step Service Status is listed as option, it’s always best to perform it anyways to ensure that all the services are listed as Started:
Once the services have been verified to be started, proceed with testing remote connectivity, federation and other Edge services. The old Edge server can be left shutdown for a week or two before it gets deleted.










![image_thumb[1] image_thumb[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhgvMOG-8GaKAIkhjHjf7d09lJU6wjZ5qYTCxRa_tOBVdtm30-tRFSpbKR29qieL1_0rpLFhyhdwv4zu5-i-nIZ_a4EtLHRXg3rKiocZJ2cuR59ZD9yum7oE4Zi9i48PAp40NYMA6qYsSfF/?imgmax=800)
![image_thumb[2] image_thumb[2]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjrxUKXM5lNEQnn5Lg1YK7dO4ovf01KZaiKnvEIrj81-TcegcxnJEsJEoRwUbZPSn9k9_FBOU4HUMoY99apYQtJ2pJDOTGDaf1QRJUL5OaGWQTUHe1amAnvUbNF7RhukW-imkCVtI4uKUZY/?imgmax=800)
![image_thumb[3] image_thumb[3]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhoRhGpEm7HazxF3MPHjH9iWP_mYFY817LVNbYbX2grGuQFaQFfFVwRsShA8uMwKkRxVzMIbVtw54OHw-prlRem5uefFAFY86BPMxT_ITiUX3tQdmTPaSehBlOwPDE_uvN0LnH5kA6yl2_H/?imgmax=800)
![image_thumb[4] image_thumb[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhuVLcYiQbBofgvEH9-SeJQjhH9f5yhxHvOovPCPa4C6Q5AccqFOSJzDTYObLPd8GCOlBRrd3Y-r1BtOIzempb3DzflW2b1tdctr8BMMUPKNjp1CvbtB0jGmZ65J7nMpMp3VND_nSz2BTLs/?imgmax=800)
![image_thumb[5] image_thumb[5]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiqsmpqnGOQ3hPGXOM_4b84qGWmYVgjBD_hd5JQiNtaGBmZz0vjAX-MH1yFe_eU_i638-f_XUs9T8ZR9rZHYSh_VcJUjIOZVyY3r-3HQ8UpPG8ZNRktvi4SXfioeNb4LTBvl1CO-6D8ekOX/?imgmax=800)
![image_thumb[6] image_thumb[6]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgsmzc9GIdq9LkqiDV5Q9AyUeztojBvJHuJHUrpOQP1xlVvjmIdYkH69vlh3CfC2NvwRi82E1IJson1ixf8vfAxa6BUB75h80gXt5S7D4WBcJLIg9VUZWeWTP5xlQS_y073u-zeXfddhsRA/?imgmax=800)
![image_thumb[7] image_thumb[7]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEj_EWhl56B_Lt_tPnsQmSP9D6iOrLHRZyeEqje4aLf3BO_klkdTXafO42c_ZX2mNmnRX5YSepU8WtR3jYZLQszFtp5lXaPvc-xQuqk3_AitWvSqe-qzbJiWpcf815XMGIeDokX7nTtAx0LL/?imgmax=800)


![image_thumb[8] image_thumb[8]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg9cXsaUi9utCI43zzT0NIb93OmH-8iqeSOaBbuzN8Z5QppDGEL16SYCqUOpuGX-KIYw2iIv5DPmoBzZfcplcuK32xjcfBPCU8ArI6rKaxZwRgx8IiVLueyF51U6m6Ol76ctFw7xttMBbXj/?imgmax=800)
![image_thumb[11] image_thumb[11]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEh6ByA0E1XZJPj95cJLkoTGvHW7qHzgddNeRRXl2lUuS-OpjvBWUoQpxqapdyZkQO4WV9hIMoUD3M7DY7PZbvgrf53YlMZQK4ZVFfaKhiVZQUkQnzm3FOeZlNb9IXBvLTqRznD-tvKMarD8/?imgmax=800)
![image_thumb[9] image_thumb[9]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhFJpnNGxK0-PTmOgaOUZIbvno9Hy3XbDxlmm53l1iyetvnDUHmzTu7K12aO6vdg3oC4sRJACQRTABpEfojm552BB8sakAuyAmRBq5Z61QvWYIaUxZtOjmJX1ZDBSaSlMUzKyUxqIA9t8RH/?imgmax=800)
![image_thumb[12] image_thumb[12]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgPLX87WE5Hpe_VAuWFeBxo9cwqyG4mA2NRVpYPlwpboKTfID35jrKGssn6IxkPaY5hKZ8kBiTvmzs8MxCD-xrEbIUVxi_YhqGk7MbS5jOFcw5AV6iJke6XYQpEhwCIXh9KPHMAmFBphvqJ/?imgmax=800)
![image_thumb[13] image_thumb[13]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjGtS_oc37RTUl0JJODdPZljmwCJriSk3bm-iUCaDNXVfh67XK0laqlTocB1mLw1WSULTJtYyhtkju_bJNIjJHX_vCJH3KwxdSve7Bj95wKZOPa-6Z6toSvC1LALMVIkdgn0wtCwOJLUpsu/?imgmax=800)
![image_thumb[14] image_thumb[14]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiHx1R6K47nbLlry7h0YGFl8Vbkuyt1Loa4GpbdyaKS4UqvVCE76mF3BknSinzuEd-n5h97qhSnavzZS5ePnBoP6vbKNteBbNfnx9scHMqdfBZhS2PXHYylJ5bDeT7VIGKpSAbXX18qGQB7/?imgmax=800)
![image_thumb[15] image_thumb[15]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiKiA4yAKgQ6cXJhE1tYeykV4sHlNLGe-93wO164G_sraRV8IZ8fGZ1eTTXQHhgtJ-tPB9RwcaQgvDKV5Lzk7h8_vLNfTJOozm7UfZSp3PX-rvBjCKUqi7GArtvOY-nOH0Y642ie58ijucs/?imgmax=800)
![image_thumb[16] image_thumb[16]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgDIvJmAjeiZDpyECUA8SLpRw6_BIU7AFNjww_h-0wj5HWUKxqIx7b_qmBUVzIZxKxBzeNDicePcDx89_vLdV2koUyUkCrVf4Gb0BNJjaK7CIxeAFDiOMBXfo-j7w135onq3SoZ8nCe-Ve0/?imgmax=800)
![image_thumb[17] image_thumb[17]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiyGvcsXffvUSHkxk4UgdibCJxHAp0e0fdnPB063h-ohNGLjaIY4VCmQApS5T3SCJArmLJrqnzjVrhV4fH00pVbedVbFQXr6oQwc1VNXCrXYPTVq_0RyoQgD12fvQNbzWPeKT6wF8h1-hUz/?imgmax=800)
![image_thumb[18] image_thumb[18]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhsaYcWMN8XohnK_x88FfKvJoRDxh2pHJg6fHI4X2jQ0GI1VQmzORJIEn1IgX-10pL8IRw-emmam_0yY0Xy5tV-iqkbKiWUHtPmh8d6YC74HdMG8YYXDHMcz82VJRerCxq-CHMn0_wvVkOD/?imgmax=800)

![image_thumb[19] image_thumb[19]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhtO7aOal3vqdLJA9ZrzUqNoY5jGmkVu4fDh_G7p8A26uUnWg36uUjfzNyjF6esZ9rTMrmsTns-Nsh9zUdPso3GJDptJfdgSuSxVk8DLJt4O2X-oWxbssUzvQPNKHQ5xhz96pkHYHAVBynE/?imgmax=800)
![image_thumb[20] image_thumb[20]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiKgkIKZxGcaPPwFmckNB7HL8y3s-mcP2i7qY4E-FJmJLX9L-WHJ5E6gQLE-1kr3YlkSgjSe6tlMS907whEQ23mmHiI1nqnWwql9lUBNLHJM8gfXninFS0Cl2XeqwjpoTdP96TwM7qpzTBp/?imgmax=800)
![image_thumb[21] image_thumb[21]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhCsnAAuiPX8A_3EYIgPIGY_5S8AW2bFAkFsQm9_uBw6DGL_XnFzBuczYkY-lI7rPmh6ENPRTKZQDJ2h4pWxnVQJKx7Kci3ybMbZ-rXq94jG5G1YToNUO4n7VxWzxXpWK1AtepohBiNH203/?imgmax=800)
![image_thumb[22] image_thumb[22]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi6rg2EW_tBrmwAovG11BTns10ZjkOvgE609BkZh-gqNjzNImCKXDzJPtOnfqfqMn7wTzpJz2iuof6jGR-9nT_oXujAV1a3E2QBilX1uzz0ZqF9SbAll-hKHXeZUKbJMUY8XAkaP3jk_ihW/?imgmax=800)
![image_thumb[23] image_thumb[23]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgjzRYesgUcKdG40zUOuBWzlHQaeU-SosD9gJUZbvm3ohL4mRlnpcA4n9abN9nA5765WiY2KT7yjhStKFM7nmxF-VUF-8eV5AjUrHrDiECBTy1LQxf3QyDt-vPHVaB-LNzO7fugF62mD-YH/?imgmax=800)
![image_thumb[24] image_thumb[24]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiKaw33z8K7p_Y3ypC4-frX1Jepaf13IVc4eEwKSBqCWSJOjLHaZ_ZlWhCGG6AKjtE-7PZlsAEPXB5_yQ_FZ6mEV0ix1yCsQqDgm7pLfbIjck8VQHbJntAuonumRZpYvLMFw12-JcsSMh9k/?imgmax=800)
![image_thumb[25] image_thumb[25]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi_yS0g9_Uv4f4Yj58t1Ls25JS36aA8VZ6fENVt3pYrC5Vtmn9_DYhMF9ruf736rLbrDgwarxywURHzKjDuabkvGJbNcnsIhEcdgBjJgYqXl8Ycko7Is_JYjm4gw4wBXjECDcfUryCINORk/?imgmax=800)
![image_thumb[26] image_thumb[26]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiP2-dxYRXHEEBVvhGTX6vZF8zh1hMC78p4gSF2VEXfH8hhEyUyGXYrcoFXOxjK06rr5obpN8iVNTPXDKwT37kvEHrbvcK9jTLq0V24145gIaBJJHGuyP3bdd3JdgWfBzTreoDVDsIlSo-J/?imgmax=800)
![image_thumb[27] image_thumb[27]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgClQPuf5RkO3RLcbNSHz5M_w9jSXz0JER18bkxeFOS-1OJQW0SuTWxkuNaMSl4bedfz955OqsEy6gdHrHkd2WYpbPwnBZDe13eLOsB1Sj7jrMFRadqPV6tDHggODF8oWHGIqRGSphuxt-o/?imgmax=800)
![image_thumb[28] image_thumb[28]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjnPv08G1dVlbqE0ahQbWF5yGBBSWNP03J6YsTyEMqubq6mlKpNRp55Kf1A7EoFt8JC53R13oclF-gf5itiHJCxERzrxw8eYboFjnrJXohtoXjtQmc7T5MmH7YPhwh-N-kizK7b2qqqUh2C/?imgmax=800)
![image_thumb[29] image_thumb[29]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjxa-CDSehyphenhyphen9W38lWcpInDWp6c4WVywsNl_gCxcAr_-dp6n9nw4xpcZTha29SI8-NmqtvLS3x0s7_h3hcokEzDy6ZhUV1mBaqzqvJem4RUM1mqtB69p0nPKojdpX5pVdrkVst9FilH1qwZM/?imgmax=800)
![image_thumb[30] image_thumb[30]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiUbp5SHCUducyo_YiV3M91Z8tazhoBwLkxF-2Az0TlNHUEVTZbFhXS0tGWV9SJpqjrMsm1tTp6ajmDcZcs0EI4mNdYiHQNk0KCfNjGKsLAaLQhUflpNAj1G1ZxXW8vq5__peEY_jr2f-_U/?imgmax=800)
![image_thumb[31] image_thumb[31]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEji7nP7n-6f3Q1vTccFj-6nJp70aTNTV1qzmeSoLvjeXVIY1om79sS30gdL71BdvbEYSlpjUcy1tgJfE57eEHvCs2VZSe0XxX5u0W7-TqmtwDCDE_9FYmYaBuA70CLyZXMEgVfKzC8_pA8h/?imgmax=800)
![image_thumb[32] image_thumb[32]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjEByS_1RhZzTj5SfEkPdqVDULM3MOZvc9GhDOavVqzkyM0ibas3Otjz2InM5uB1PAezMocJxlAWCEed4l1mkuMNvXZFXU9zN9MqKW-UFbfe84fvi2_nTwDC92SJShQEEJJMMEwva07TvMy/?imgmax=800)
![image_thumb[33] image_thumb[33]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgLG3qJWEIPOd7x6a2zEvM3yn_i0moGh-5kPPOMrRejf_Tx59WFZ2Gx_Ee1C2Oecpk3eGjAU3gNMvS48jk7aNOmZXIc-WBzc0CBGSP_cpqrg-vWrW5wMraFAi3urKL-At6v8Tq2L5E0ovxu/?imgmax=800)
![image_thumb[34] image_thumb[34]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhUJeWlvWRPL-Lg13coKOw93I8X7_wsduL2FqoyIy4OK_K-KAa0aQ15YFphzWAeMDqpBVtEKfC4U0dM9sQb6lxX7L_MosSUGgUJb9OAh-UZm6Nsyn3tSHIXuk60LYnh-fQ4U_u5zUvH9kGG/?imgmax=800)
![image_thumb[35] image_thumb[35]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg3nhfaUr9BsCrNcPdpk5BleC2d4-RjInieaKzlCxq81d7ca2VXvehSTyidTiNjzZ-hIvs_N1iYpnITB2-sl6OUbiBbIJp5X4cz7Fke8Kj3Pj23H5jJwBpkcjhRsrkEbbZZ5RIIB1Ab5T6a/?imgmax=800)
![image_thumb[36] image_thumb[36]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjObT0qB4QUrC_N-Fs2AzZAd1FopuMXUvDC9JgdsFvFV48DIF6i2mtPii474DbOcBhkJgDV7L244BeqnETNwTyxnCBXAZFFcckfxTDlrr-VnalRLkyLuU9nKkqLhOh48isS1oeVpXiZfkS_/?imgmax=800)
![image_thumb[37] image_thumb[37]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhekQBBIVOAxBZ7swM4IWEQjWBgX-27HkJCB-97T3wnP4d62jsc-VUSX0DYNrX65abNgXNxFDl9xbtMwOHK8FQZP-ZfFiJK-qeDvGl0w0SKCPKCDDl4c-bxfsuSsmmLu43UNsEwWwQvRwrO/?imgmax=800)
![image_thumb[38] image_thumb[38]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhTtWYArL618pcFB1Lt3BNfDhQWUYTVssAzQjHPZ9t9G06TkdVporaV6y6uLkAVqbtio9S_63WWz2hHHMQo3YAfqxuByh3Z5Y3KO-O5ZD2VIzB-W_6swEMXyTHic9QAr_GY2_TBzfBH1SVc/?imgmax=800)
![image_thumb[39] image_thumb[39]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhAXA302hyotGcSnUS6l-yp8I6KVCpVyGtl0PVkTpCqlOVVn4IlJOsqhsEIdgOnUQjtzNTJ4pFPGFiKpfNmgHvAcfUZhIZLtMHWfyPPobiWYqcpEmsQiWMnLb3E0yavFne2LIB6h-fAaY2u/?imgmax=800)
![image_thumb[40] image_thumb[40]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhpHdud-SHXZ9GCYYM0c53zJkPWoyAGOhVm7-p-YjacSVlNezg_BfUL5QSpGTPfs5_YbQ7WVxeWnrQZ8T_IFQPar0tRkAzjnGZTmuZKksxO3jP2v15xMiAFrPp6oxEKy48SfwklDwxnxs13/?imgmax=800)
![image_thumb[41] image_thumb[41]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjjNcQhpyrK9ZK-P1OQPMxyTQpI2oqdwCVB_7UgL6D6YV2ibjjriK8KjFgSUbX5v4njUHo8xgCiDoh3SX88E0AhyphenhypheniHwmGDO4qPAWVlNbvTE5egriMoKw2wk_p9MO4dXahhM4M3tiL8YSPAq/?imgmax=800)
![image_thumb[42] image_thumb[42]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiYcWTDkWfSAbSuFN5Ti_vGUdhGq_QRWAATN1v-V0hTuDRj73_7n8PDO8tix_5-13m_JM2FkHR4jeWah2P0ByO8LGuvzhTOo8IkJAIxsICUdQ72BlVgaMR9UHE9XfaIDo5EgV-Q4PMSqhHA/?imgmax=800)
![image_thumb[43] image_thumb[43]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiE-85WZf_II3g2vPAIogzLCHAIqFA4Oa1gm4sZrJS-qV-IOjRrUEsNo-d-Rdii1JC2BCjG_nhDVAHlwXF9W5EEn28mygi3h0X4XmX_uoF5NDjxVq6ex8SUOT_dd_J_K3LNd_Q91m84tLxO/?imgmax=800)
![image_thumb[44] image_thumb[44]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEj48K9dKNkIi3y_zEBdveXsP5bMIxDW_0tVQYuzAOrRbDbwLJKA4SIKQUnSRsBb7zujBu2X7kuiCbniQwy6eHW7MCxC5mSUGFyzIf8L1LHufAL58HcuhASPcwy2LyDSDHXJg4E7xBB9qj3F/?imgmax=800)
![image_thumb[45] image_thumb[45]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgbgnKH-e-DapTMdBYAvO-Bg_9t3MbQ6WtsrNDJ3ZyDnvpBiOZGFLOejaLrBlvZgkPGbh66LEbBietasuHEACS1w8h6UfybmVcnJBWP1jT0IUHeBs6BXSSj7mqgB4RHrnentM2QFFvZ2ROx/?imgmax=800)
4 comments:
Love your posts they have been very helpful!
One question though, in a migration scenario, can the Lync 2010 users use the new Lync 2013 Edge server(while they are not migrated yet to the new pool)?
Same question here. Before the transition it seems you had defined the old edger server in the Lync 2013 topology as well, do we need to define the new Lync 2013 Edge into the Lync 2010 topology so the users still in Lync 2010 can use it? Thanks!
I assume in order to reuse the same certificate the 2013 Edge server name and IP will be the same, correct?
Terence - I have the same question as the previous poster, is the server name relevant at this phase? I know the cert will be tied to a FQDN on the FE... but what about the edge?
Post a Comment