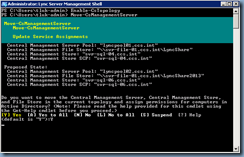
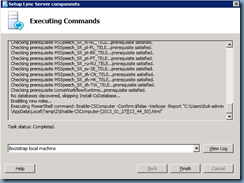
I was recently asked by a colleague to assist with moving a Windows Server 2008 R2 NPS server providing RADIUS services for a Cisco 4400 series Wireless LAN Controller to a newer redundant design. The redundancy was provided by 2 Windows Server 2012 NPS servers configured in 2 different sites that the Wireless LAN Controller would attempt to authenticate one after another in order and finally fall back to local authentication if both NPS servers did not response. The document I was provided was the following:
PEAP Under Unified Wireless Networks with Microsoft Internet Authentication Service (IAS)
http://www.cisco.com/en/US/products/ps6366/products_configuration_example09186a0080921f67.shtml
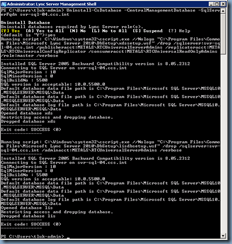
One of the first items I noticed from this document and logging onto the existing Windows Server 2008 R2 server was that it was a Domain Controller with the Active Directory Certificate Services role installed onto it:
I was never a strong supporter of collocating CA services on a domain controller because of the following:
- You need to remove the CA services if you wanted to demote the Domain Controller.
- Not a requirement for Windows Server 2008 but back in the Windows 2003 Server days, the server you migrate the CA services to need to be the same name as the original so if your original CA server was DC01, the new one would also have to be DC01.
With the reasons why I do not support strictly following the Cisco guide and issuing a Domain Controller template certificate to use with PEAP, the following will demonstrate how to use a CA located on a different server for wireless authentication.
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
Most administrators would know that you can continue to configure a NPS policy with Microsoft: Protected EAP (PEAP):
… without a certificate but if you attempt to click on the Edit button, you will be presented with the following:
A certificate could not be found that can be used with this Extensible Authentication Protocol.
If this was a domain controller, one of the solutions is to directly install CA on this NPS server and issue a Domain Controller template certificate for authentication as shown in the Cisco document. An alternative solution to this if you don’t want to install CA services on this server is to log onto an existing CA server, open the Certificate Authority MMC in the Administrator Tools, and navigate to the Certificate Templates:
Right click on the Certificate Templates folder and click on the Manage button:
The template we’re interested in is the RAS and IAS Server template:
Proceed with right clicking on the certificate template and click on Duplicate Template:
Whether you select Windows Server 2003 Enterprise or Windows Server 2008 Enterprise doesn’t matter unless you’re using an older CA (i.e. don’t select 2008 if you’re using this on a 2003 CA server) but for this example, I will select the latter:
The properties of the new duplicated will launch:
Name the template with a name of your choice, modify the Validity period if you prefer it to be longer than the defaults and enable settings such as Publish certificate in Active Directory if you like:
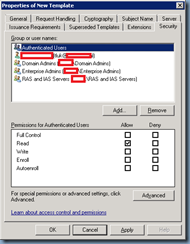
Navigate to the Security tab and select Authenticated Users:
Check the Enroll checkbox and click OK:
With the new certificate template created, open the Certificate Authority MMC window:
Right click on the Certificate Templates folder, select New and click on Certificate Template to Issue:
Select the template that was created earlier:
Notice how the new template is now listed:
Open the Local Computer certificate store of the NPS server and navigate to the Personal folder:
Right click on the Personal folder, select All Tasks, Request New Certificate…:
Click Next:
… then Next:
Select the new certificate template (NPS – RAS and IAS Server):
Clicking on the Enroll button will begin the process:
Note how a new certificate for Server Authentication and Client Authentication has been issued in the Personal store:
Now when you attempt to Edit the Microsoft: Protected EAP (PEAP) Authentication Method:
… the following window will be presented for you to select the certificate:
Hope this helps anyone looking for instructions on how to use a CA that is not directly installed onto the NPS server.


![clip_image001[4] clip_image001[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhZK9g-ubFEdCJIm73FtJBRvIAVdH1ciuWgtqw-EmNIBsuCyNxRCvN7CCRq3jRJ-rUoUPxkGXywScOG5nCWrSfRoXcq8-GVPRzx0Y6rMbQvJJa6R1E1gI7C-LsO2eIKpo7edNt-euGVxTQX/?imgmax=800)



![clip_image001[6] clip_image001[6]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiRSA-8vC0B6IA51SrEYOHtp8_rQSLa4soHNv6FW8n4HhY3WnMyqKEMq9rQltS-5LvJEJOzWrbb4sqTj8492kER_5apQEmLIyMWPtqL8aqQp_AeKXHMjGcFlg8luPd7TZiiIY-QGzMGMCrH/?imgmax=800)
![clip_image001[8] clip_image001[8]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEieIRtEf2kjMaU-Ux77WLuj4-bgHJyI9ecEQMUYoFiJnBB8mjE-d4oZywcMtvv0ksJczTfXPr2ZNWRe3auIs18cCnch2xF0hqoI18g7eIqsx2nAXQcDgZMiQjwlvDNN_frn3mF-K7DRM3Ki/?imgmax=800)
![clip_image001[10] clip_image001[10]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEifp1-okQH6_VjEL7FQqYHHhiaw6GukdsxprNqq9UYXA1dqx9R3EjXvSkBKsa5wU3-coDs7Qva7o5Gmn-pt1DuBgx-DpeEjmU_A35wKNYz-NZGzS1FZ_hEl8T5_J_vPGInw8xHlqomc3-Xp/?imgmax=800)
![clip_image001[12] clip_image001[12]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhNLo8Va9bVjONHYzg-KPa80Ei_h1DAc2blKcYoJX3OmnOu3NbNe7dfk0b4MyPdCdWniREsIVuJ8ZvuW-bfiznPvnR9lY2xiKIILJtA1OSIePxXhaNbBEyUhv4RuuaXUgOBmw9Zzlzwjj2e/?imgmax=800)





![clip_image001[16] clip_image001[16]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjZK1g0WCJQcM7YROW42eLH8WEke9MAAqRfnjco1pJbRm0RNpVL-Qvuz8qSQnStNLzfzIKNFiWmvd19_KxccTs0dTRZGCeSNvvmpMt3K2YbbpXgk6eIWZKABc0DPsg4QX_5wb_2RhlC5ow5/?imgmax=800)

![clip_image001[18] clip_image001[18]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEj_lQIVFPYZrg0VVEM3-53LPuacnngvM3bgm4wCpklhf-D3Xht6ezp0Sll7zZW6qAv2pW2tt_DPIJ4Bu4cSERMFUJ_V_HB-Zt5n0BislgiEyCyJ07L7E5M9MVltfhBLofyK8CrNrEfdZgsb/?imgmax=800)
![clip_image001[20] clip_image001[20]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhlT9KVnksA_C883KPmMufvGh__gU1n0SnmENwaD1rs0RM7WDeTbkaCNqF_wI_z9PXOr5C8CZ2YAXDQEVS3HrwGb6Eg5Dwns9u18mDzSfkBt68wVHR1j_Vot0ky_O6bmjB20Fa8cxjbOcCj/?imgmax=800)
![clip_image001[22] clip_image001[22]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjGonp-x1QDQLc7Nt3xVm3qneLGPpayQzdUD3zjiL39ARcerq-Nu1lRLlQMWUSYlxSULiEDzQXGx0ii47kH92Wr0YM23hbc2aExA7VHvZGeViizsX62M6sgrlayLX6r-wqeTZh-iTLqu2vm/?imgmax=800)
![clip_image001[24] clip_image001[24]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhki7dOZPJe_yATlZRfQDIxn8gD1y0dbvkqxe2FIUZT3ipt0RvtHDrX72rBY9wCx9mrW1-s_aFUnT9Pa8_DJIelnmuTQw4sspg3huuF47YdJKvL-l_N7GWOvY5ouqRIX1kXdLFb2aMnZpap/?imgmax=800)
![clip_image001[26] clip_image001[26]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEihkPxXgeQs3Kte03xtZPaafoxdpTJL-aWVIwQjsZO7aQfqx6o14Eyo6LFIasef7Zzh4TKN82t4mVC3ZDWlyf2uEbetH-Vl1TBMeQ2OqT7oUqD8hekBul1EHi8Lwao8Nef0DDCis2NriZAS/?imgmax=800)
![clip_image001[28] clip_image001[28]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiJ7sJGo4-sLhzbyrFK7HJDsbDN8MT3UEeoZtcARIt74vTWkd0B9y5Z4Ti5Ty1vqBvGZsRrRb_59BCTfQzdusF4jAxrn5UXH6qqr7AHpOQmzCcGhyphenhyphen3ab_VCZ8ObalihOFXjNou2Z0U8tq-q/?imgmax=800)

![clip_image001[30] clip_image001[30]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiifAJP_y8YQlgMYPz83e_JQ1hzAvW3hGDjMpmcyPyYfK7m9BdKWH4o_7RPlZ7Lr-qGbyVNzJMrgV_KGuP6QuQscMAyL3eBYa1QxkfHElRADeUsAiinmPr0Fg8WgxYTxrxh_NoUx98YxE7x/?imgmax=800)