As noted in my previous install post (http://terenceluk.blogspot.com/2010/09/what-installing-forefront-unified.html), the following is the configuration process I went through during the deployment of UAG for DirectAccess:
Once I rebooted the server after the install, I went ahead and ran Forefront UAG Management from the start menu:
Had to wait a few seconds before the management console actually launched:
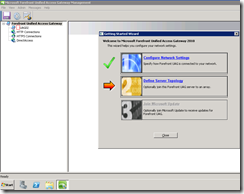
The console launches and I was greeted by a friendly wizard:
Prior to installing UAG, it was important to assign the proper NICs with the external and internal IPs. The following screen is where we identify which was which:
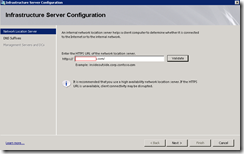
Here we define what our internal network IP address range is:
Easy enough!
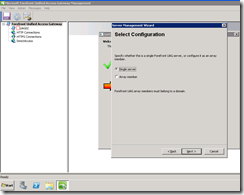
Next we define the topology:
I’m actually going to add this server to an array but because I needed to use this install to test an issue we had, I went ahead to configure it as a stand alone topology for now.
Again, easy enough.
Self explanatory.
I chose No for the last option.
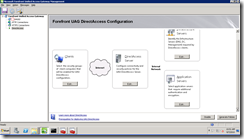
Once done with the initial network and topology configuration, I was presented with an easy to follow steps:
- Clients
- DirectAccess Server
- Infrastructure Servers
- Application Servers
Select the security groups of clients computers for UAG direct access:
Notice how the configured nodes have “edit” instead of “configure”.
Continue defining the networks:
Define the type of UAG DirectAccess required:
Define the certificate you’re using where the top is either the root or intermediate certificate you want to verify certificates sent to DirectAccess clients and the bottom being the actual certificate you purchased for authenticating the DirectAccess server to a client connecting:
Make sure you install the certificate or it won’t show up in the above screen:
Here’s a screenshot of what window you’re presented with when you choose the root or intermediate certificate as noted above:
Once completed, click finish:
Notice the change in the nodes again:
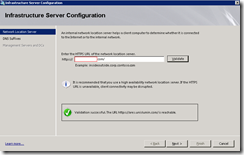
Once you click on infrastructure servers, you’ll be ask to enter a location server which you will need to setup prior to the configuration:
To validate whether you installed the location server properly, click the validate button:
I wont’ go into the settings in the following window as the details can be found on the deployment guide:
The wizard picks up the domain controllers but you’ll need to specify the other servers in the environment:
Notice another change in the nodes:
We don’t have any Applications Servers ready to be configured yet so I left this as the default:
Finally completed all the configuration nodes:
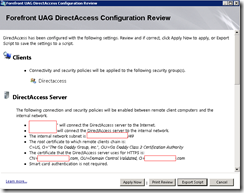
Once completed, clicking on the Generate Policies button will present you with the following window where you can click on Apply Now to complete the configuration and this is where it gets interesting for the deployment.
Once you click on the Apply Now button, you’ll see this window pop up:
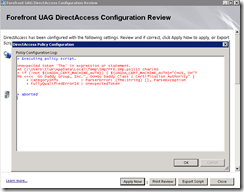
Yikes!
> Executing policy script.
Unexpected token 'The' in expression or statement.
At C:\Users\tluk\AppData\Local\Temp\tmpFE62.tmp.ps1:13 char:80
+ if (-not ${UAGDA_CERT_MACHINE_AUTH}) { ${UAGDA_CERT_MACHINE_AUTH}="C=US, O="T
he <<<< Go Daddy Group, Inc.", OU=Go Daddy Class 2 Certification Authority" }
+ CategoryInfo : ParserError: (The:String) [], ParseException
+ FullyQualifiedErrorId : UnexpectedToken
The install and configuration was easy enough but this error got me stumped for 3 hours of troubleshooting before I was able to resolve it.
The next post will show the troubleshooting steps I went through leading to the resolution.