Problem
You have a Cisco Wireless Controller setup to use a Microsoft Network Policy (RADIUS) server to authenticate wireless clients via 802.1X and while Android devices and all Windows clients that are joined to the domain have no issues connecting to the network, non-domain joined Windows 10 workstations are unable to.
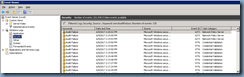
Attempting to join the network with a non-domain joined Windows 10 device shows the following Audit Failure log written in the Security logs of the NPS server:
Log Name: Security
Source: Microsoft Windows security
Event ID: 6273
Level: Information
Network Policy Server denied access to a user.
Contact the Network Policy Server administrator for more information.
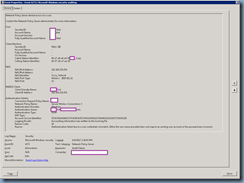
User:
Security ID: CONTOSO\tluk
Account Name: CONTOSO\tluk
Account Domain: CONTOSO
Fully Qualified Account Name: CONTOSO\tluk
Client Machine:
Security ID: NULL SID
Account Name: -
Fully Qualified Account Name: -
OS-Version: -
Called Station Identifier: 00-17-df-a8-e0-50:CONTOSO_Corp
Calling Station Identifier: 60-57-18-a7-ea-18
NAS:
NAS IPv4 Address: 192.168.220.254
NAS IPv6 Address: -
NAS Identifier: Cisco_7d:fe:e4
NAS Port-Type: Wireless - IEEE 802.11
NAS Port: 13
RADIUS Client:
Client Friendly Name: CONTOSO Test
Client IP Address: 192.168.220.254
Authentication Details:
Connection Request Policy Name: CONTOSO
Network Policy Name: Secure Wireless Connections 3
Authentication Provider: Windows
Authentication Server: CONTOSODC01.Contoso.com
Authentication Type: PEAP
EAP Type: -
Account Session Identifier: 35393361643862372F36303A35373A31383A61373A65613A31382F3739383139
Logging Results: Accounting information was written to the local log file.
Reason Code: 16
Reason: Authentication failed due to a user credentials mismatch. Either the user name provided does not map to an existing user account or the password was incorrect.
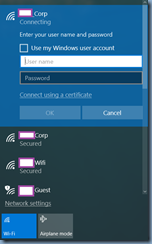
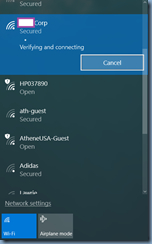
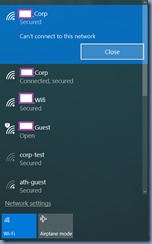
The error presented in Windows 10 during the login is shown in the following screenshots:
Verifying and connecting
Can’t connect to this network
Solution
One of the reasons why this error would be be presented to non domain joined Windows 10 client is if the NPS / RADIUS server is configured with a certificate issued by an internal Microsoft CA that is not trusted by the Windows 10 device since it is not joined to the domain. The way around this is to either install the issuing Root CA certificate on the Windows 10 device or configure the SSID network manually and do validate the certificate. The following outlines these steps:
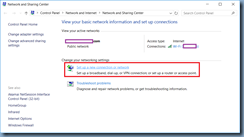
Begin by opening the Network and Sharing Center then click on Set up a new connection or network:
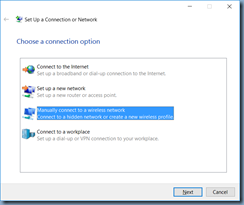
Select Manually connect to a wireless network:
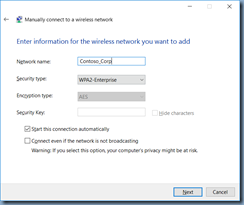
Fill in the appropriate configuration:
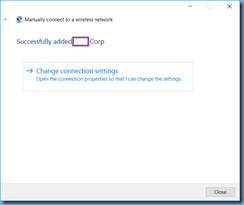
Once the new SSID network has been created, proceed by clicking on Change connection settings:
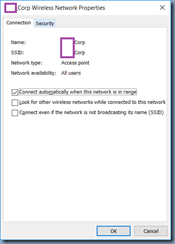
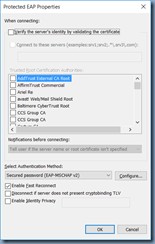
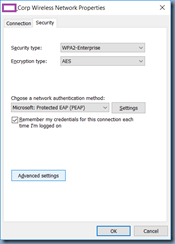
Click on the Security tab:
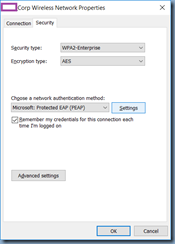
Click on the Settings button:
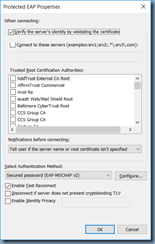
Uncheck the Verify the server’s identity by validating the certificate option:
Configure the above usually does the trick so that the following prompt is displayed the next time an attempt is made to connect:
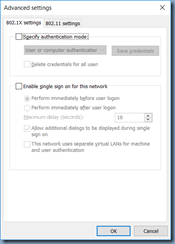
However, if you continue to encounter the same error then proceed by clicking on the Advanced settings button:
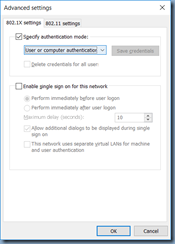
Enable the Specify authentication mode: option:
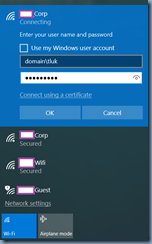
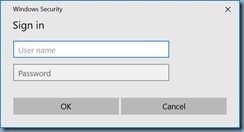
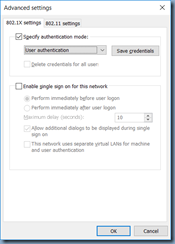
Change the configuration to User authentication then click on Save credentials:
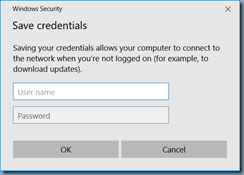
Enter the appropriate credentials:
The SSID should now no longer prompt for credentials and will automatically connect to the SSID network with the saved credentials.
No comments:
Post a Comment