I’ve recently been asked by many of my colleagues and clients about what they would need to do to upgrade their internal Microsoft CA from the deprecating SHA1 hash algorithm. The process could be short or long depending on the Cryptographic Settings that the CA is currently configured with. This post will demonstrate the process if your CA is already configured with the Cryptographic Settings Provider as Microsoft Software Key Storage Provider.
Begin by confirming that your CA is indeed configured with the Cryptographic Settings Provider as Microsoft Software Key Storage Provider by logging onto your Certificate Authority server and launching the Certification Authority management console then right clicking on the existing CA and selecting properties:
Under the General tab, review the configuration listed for the Provider and ensure that it is Microsoft Software Key Storage Provider:
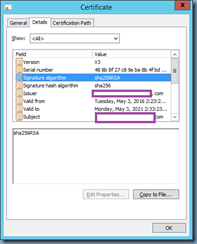
You can also confirm that the current certificate used for signing is SHA1 by clicking on the View Certificate button, then the Details tab and review the Signature algorithm and Signature hash algorithm fields:
With the above items confirmed, proceed to change the Hash Algorithm from SHA1 to SHA256 by executing the following command:
certutil -setreg ca\csp\CNGHashAlgorithm SHA256
Restart the CA service with the commands:
net stop certsvc
net start certsvc
Now when you open the properties of the Certificate Authority, you should see that the Hash algorithm is set to SHA256:
With the Hash algorithm updated, continue by renewing the CA certificate as such:
All Tasks > Renew CA Certificate…
A new certificate should now be created that uses the new SHA256 hash algorithm:
Here’s a screenshot of before:
… and now after with SHA256:










2 comments:
I have a 1 tier Certification Authority on Windows 2012 R2, I need to migrate it from SHA1 to SHA256. It's using Microsoft Software Key Storage Provider.
After upgrade to SHA256 then I will renew the root certificate of the CA.
Now the question is, what will be the impact of renewing the root CA certificate on existing certificates that are in SHA1 ?
Do I need to generate a new pair of key during the root CA renewal or not ?
"demonstrate the process IF(!!!!) your CA is already configured with the Cryptographic Settings Provider as Microsoft Software Key Storage Provider"
Haha, that is a BIG IF! Most of the PKI admins suffer from the fact, that their current setting is NOT the KSP but the CSP! I assume your article is useless in that case. Unfortunately it seems you grabbed only the easier part of this migration problem, and didnt consider the reality most of your readers will face.
soder
Post a Comment