I’ve been asked several times since publishing my previous blog post:
Configuring a NetScaler VPX appliance to publish load balanced XenDesktop 7.x StoreFront servers
http://terenceluk.blogspot.com/2014/07/configuring-netscaler-vpx-appliance-to.html
… how can the HTTP traffic between the NetScaler and StoreFront be secured since the NetScaler effectively authenticates with the StoreFront server(s) and the StoreFront server makes a callback to the NetScaler during the process. The answer is simple and that is to use HTTPS instead. Not all of the customers I work with use HTTPS because their justification is that their server VLANs are secured but I usually recommend to use HTTPS when possible. To do so, a certificate will be required for the URL that the NetScaler will be using to reach the StoreFront servers. Before I begin with demonstrating the configuration, I would like to note the following points:
- Do not use the same URL that you are using for users on the internet or internal VLAN to access the NetScaler for the StoreFront servers(s). This means that if you’re using https://citrix.domain.com for your NetScaler’s VIP, do not use https://citrix.domain.com for your StoreFront servers because Citrix does not support this.
- Make sure that the CallBack URL that you configure on your StoreFront’s NetScaler Gateway configuration matches the name you are using for your NetScaler VIP. Any changes to the URL will not work:
Step #1 – Bind SSL Certificate to StoreFront’s IIS Server
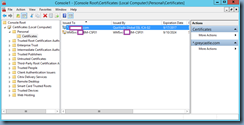
Begin by binding an SSL certificate to the StoreFront’s IIS server. This can be done either by generating a SSL certificate CSR request, sending it to a public CA and completing the certificate request so the server has the private key or simply exporting a certificate from a source as a PFX and importing it onto the StoreFront server’s Local Computer store. The certificate used in this example will be exported from the NetScaler appliance because it is a wildcard certificate.
Note that the Web Interface Address URL currently configured on the NetScaler points to http://storefront.ad.domain.com because the communication between the NetScaler and StoreFront currently uses HTTP:
Testing the URL http://storefrontServerName.FQDN will display the default IIS page:
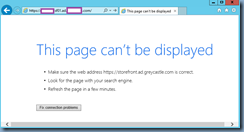
Notice that without a certificate binded to the IIS server, navigating to https://storeFrontServerName.FQDN will display the:
This page can’t be displayed
With the certificate imported into the Local Computer store, launch the Internet Information (IIS) Manage, navigate to ServerName –> Sites –> Default Web Site, then click on Bindings… under Edit Site:
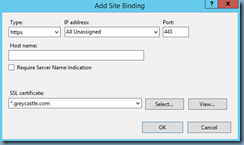
Click on the Add… button in the Site Bindings:
Change the Type from http to https:
Click on the Close button after the new https binding has been added:
There isn’t a need to perform a iisreset but you are free to do so if you like:
With the new https binding created, you should now be able to browse the StoreFront website via https:
Step #2 – Update Session Profile on NetScaler to use https URL
Now that the StoreFront server can respond to https requests, proceed with modifying the Session Profile on the NetScaler
Update the http URL to https:
Step #3 – Recreate Virtual Server with https
You cannot actually change a Virtual Servers configured Protocol from HTTP to HTTPS as shown here:
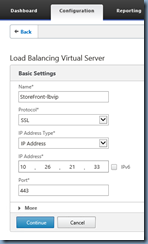
Which basically means that you’ll have to delete and recreate the Virtual Server if you already have on created as is the case in this example. Create a new LB Virtual Server with the Add button:
Fill in the required fields and change the Protocol to SSL:
You will immediately notice that the Load Balancing Virtual Server’s State is listed as being down and this is because a new service will need to create a new Service to add it to this Load Balancing Virtual Server. The reason why we performed this step first is because we would not be able to delete the existing HTTP service before deleting the existing HTTP Virtual Server since it is binded to a Virtual Server. Now that we’ve deleted and recreated the Load Balancing Virtual Server, we can now remove the old HTTP service.
Step #4 – Recreate Virtual Server Service
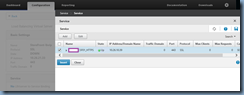
Navigate to Traffic Management –> Load Balancing –> Services:
Since you can’t have two Services binded to the same IP where one is HTTP and another is SSL, we will delete the existing one and then create the SSL service:
The new Load Balancing SSL service should immediately have its State as being Up:
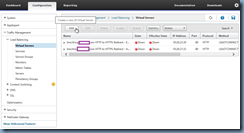
Navigate to the Virtual Servers and open the Load Balancing Virtual Server for the StoreFront:
Open the Service option:
Bind the SSL service that was created earlier:
Note that even with the service added, the service would still be labeled as being down because there is no certificate added:
Step #5 – Bind SSL Certificate to Load Balancing Server
The certificate that needs to be attached to this Load Balancing server is the same certificate that is used on the StoreFront servers and since we’re using the same wildcard certificate as we’re using for the NetScaler VIP and the StoreFront HTTPS binding, the certificate should already be on the NetScaler. Proceed by clicking opening the Load Balancing Virtual Server and clicking on the SSL Certificate configuration:
Click on No Server Certificate:
Click on the Bind button:
Bind the certificate that will be used for the StoreFront servers:
Save the configuration:
Next, click on the Persistence configuration:
Change the Persistence configuration to SOURCEIP:
Click on the Done button to exit the configuration:
Notice that the Virtual Server State is now Up:
Step #6 – StoreFront Monitoring
For better StoreFront monitoring, it is best to create a service specific monitor that the NetScaler provides and the reason why I leave it as the last item to configure on the NetScaler is because a slight misconfiguration can cause the monitor to report the StoreFront as being down so to avoid situations where I might be confused whether I published the site correctly or not, I’d like to complete all of the configuration leading to the Load Balancing Virtual Server with an Up State before I configure the monitoring.
Navigate to Traffic Management –> Load Balancing –> Monitors and click on the Add button:
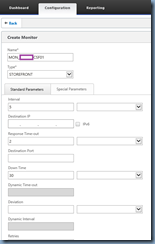
Fill in the following fields:
Name – Type in a name for the monitor
Type – Select STOREFRONT in the drop down menu
Leave the rest of the settings as default and scroll down to the bottom of the configuration page:
Ensure that the following checkboxes are checked:
- Enabled
- Secure
Scroll back to the top and click on the Special Parameters tab:
Fill in the Store Name with the StoreFront name, ensure Storefront Account Service is checked and then click Create:
A new StoreFront monitor should now be created:
Note how the configuration settings we left as default are now filled in:
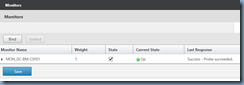
Now navigate to Services and open the properties of the StoreFront service:
Click on the Monitors item:
Bind the monitor we created for the StoreFront server:
Save the settings:
Notice how there is only 1 item listed in the Monitors section and that’s because the tcp-default is removed:
Complete the configuration and click on the Done button for the Load Balancing service:
Step #7 – Update StoreFront Base URL
If you try to access the site now, you will receive the following error after logging in with your credentials:
So before attempting to test, log into your StoreFront server and update the Base URL from http:// to https://:
Once this last configuration has been made, you should now be able to log into the portal and launch applications.




















































3 comments:
Blah Blah Blah, Yawn.
"..Do not use the same URL that you are using for users on the internet or internal VLAN to access the NetScaler for the StoreFront servers(s). This means that if you’re using https://citrix.domain.com for your NetScaler’s VIP, do not use https://citrix.domain.com for your StoreFront servers because Citrix does not support this..."
That is now supported in SF 2.6 http://support.citrix.com/proddocs/topic/dws-storefront-26/dws-configure-single-fqdn.html#dws-configure-single-fqdn
Hi Anonymous,
You are correct and I did use a different URL for the external NetScaler VIP than the StoreFront. It's not easy to see since I had to block out the domain but here's what I used:
NetScaler VIP URL (access from the internet): bmcitrix.contoso.com
StoreFront Base URL: https://storefront.ad.contoso.com
I think I made a note about Citrix not supporting using the same URL in one of my other posts but not this one. Thanks.
Post a Comment