I’ve noticed that I’ve gotten a lot of calls in the past from clients about missing certificate templates while trying to use the MMC Certificates snap-in to request a new certificate so I decided to write this short post so I can point clients or coworkers to it in the future.
Problem
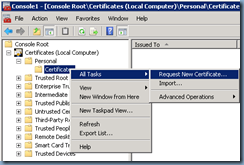
You attempt to use the Certificates snap-in to request a new certificate:
… but notice that the list displayed under the Active Directory Enrollment Policy in the Request Certificates step of the Certificate Enrollment process does not list all of the certificate templates as being available:
Solution
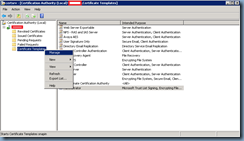
The reason why certain certificates aren’t listed in the list is because the Authenticated Users does not have Enroll permissions log onto your certificate authority, open the Certificate Authority administration console, right click on Certificates Templates and click on Manage:
Within the list of templates that are displayed, select the template you would like to be available and open the properties. For this example, we’ll use the Web Server Exportable template:
Navigate to the Security tab and notice how the Authenticated Users does not have the Enroll permissions:
**Note that it’s also important to note is that my account Terence had enroll permissions but the Certificate MMC Snap-in appears to authenticate with Authenticated Users.
Proceed with adding the Enroll permissions to Authenticated Users:
Now when you use the certificates snap-in to request a certificate, you should see the template listed:
![clip_image001[4] clip_image001[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg7UFZuocG-gZgUUXpeTR5614A6adZxG_zFpXl9-5wvqeo_r-myOTDWZOyeZFRE4Mj14gGHhyphenhyphen4gbiIZfznzkHCPK8Pkr4Kv4NnkNDA-y3mFMRrR2StObNFceN5oC7gAROxzmMbxSQfxynLw/?imgmax=800)
![clip_image001[6] clip_image001[6]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEitSpT7PqiiPufMkl0touxWlpmCyhzbfDd0fc2ypb62xLgSBpQlIeW8p1uiTHDW25neV0nAAicl9Z2ZkVdMjKbyv6EBaJ1_VyjeQWT4wGcg3Vxy8SvjUZrDtOEhiForXEeXMfHesGQnzYkt/?imgmax=800)
![clip_image001[8] clip_image001[8]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgf0Eq2zU1muWTNxjSUu2sjp7NXuc23THxSMLzzadq-o3zOWcnmJfkWoQL6mCTfOrZ3qU2U7FLQDzADO6NwgUGH84RZ66U91ErjSVCiucawlnj0RwrOV6MOrbE9Qk4Nv3r95cagbHYsvnuC/?imgmax=800)



![clip_image001[10] clip_image001[10]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEig8yO0iYV2QYsXicY3GQeAYBfc5G2GKskGO39eTiFvxQAvZ9XCK0MH_ZPaON1Uk-xXprYwvAT_CFTFdFszWWmoUtirawvGcskxaDx_Y2xooVkiGEMy6Ledo8rqMQKKDeWebfN_MMk839S-/?imgmax=800)
9 comments:
Good stuff - thanks
you rock, worked great.
All these post failed to mention is MS Active directory Certification services are based on the AD Domain forest level. So if your forest level is 2003, then you cannot use a 2008 and up custom templates in ADCS Web services. Most people having this issue is because the CA Custom template is 2008 and above. Try Duplicating your Template in certificate template console, the first question when duplicating the template is to choose 2003 or 2008.
Choose 2003, then go into the Certification Authorities MMC (certsrv.msc) and there then right-click the Certificate Templates folder and issue the template that you just created. Now go to your ADCS web site and you should be able to see you custom template now. I know what about the 2008 Templates... Your AD forest level will need to be raised to 2008 R2 for the ADCS web to show the newer 2008 Custom Templates. Good Luck my hard earned .2 cents. I hope this helps someone out there because it took me weeks to figure this out.
Snap-in appears to authenticate with Authenticated Users.
^this is not true. Authenticated users isn't a group an application or snap-in authenticates with. Authenticated Users encompasses all users who have logged in with a username and password.
It is not possible to authenticate with merely the group "authenticated users", apparently the previously used user account to request the certificate with didn't have the required enroll permission.
Granting the "authenticated users" group the enroll permission ensures that all user accounts that authenticated successfully will be able to enroll the certificate. This is a, per Microsoft best practices, less secure solution, unless when you actually want all authenticated users to be able to enroll the specific certificate. A more secure solution is that you give the read and enroll permission to a more specific group of users.
I have done my best to replicate the issue you are describing above, but I was unable to do so. It kept resulting back into that the specific user or group just didn't have the appropriate permissions to enroll the certificate, it had nothing to do with the "authenticated users" group lacking this permission.
As to what Anonymous said above I disagree...
We have a 2003 forest/domain level with Server 2008R2 DC's and we had no CA. I set up a CA and went to request a Domain Controller certificate only to final all templates were unavailable even though I was using a domain account that was part of the Enterprise Admins group.
This blog, about allowing "Authenticated Users" was the only thing to work that allowed my CA to process a Domain Controller certificate request.
many many many thanks to Carlos Rodriguez. After 2 hours of googling, you finally solved my problem. Who would have thought that Microsoft in their infinite wisdom would prevent certificates from being issued if the domain level was not high enough!
THanks again!
Dear all I know this is a old post but please note that the problem is due to the fact that you need to add specific computers account and provide permissions to them. Authenticated users solves the problem only because it includes all domain computers.
Also - after making your changes, don't forget to restart the IIS server hosting certsvr - until you do that any new templates you have created won't be available for web based enrollment.
It's the FOREST level that counts too!!!
Post a Comment