Problem
You’ve configured a new Network Policies policy on your Microsoft NPS server:
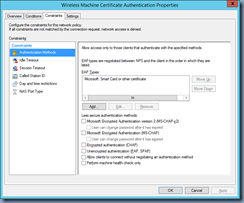
… with the following settings that will authenticate devices with machine certificates:
You configure the SSID on the wireless client with the certificate with the following settings:
… but notice that you receive the following error when attempting to connect:
Reviewing the INXXXX.log file in the directory C:\Windows\System32\LogFiles on the NPS server show that the wireless client authentication makes the connection attempt and the policy is matched:
"DC03","IAS",07/07/2016,20:32:46,3,,"contoso.internal/contoso/Computers/Desktops/Victoria_Place/IT/WKS-MXL2451S3K",,,,,,,,9,"10.80.9.249","contosobm-wlc2500-1",,,,,,,5,"Secure Wireless Connections Machine Authentication",262,"311 1 10.70.1.3 07/07/2016 23:09:55 79",,,,"Microsoft: Smart Card or other certificate",,,,,"577ee697/60:57:18:a7:ea:18/70380",,,,,,,,,,,,,,,,,,,,,,,,,"Use Windows authentication for all users",1,,,,
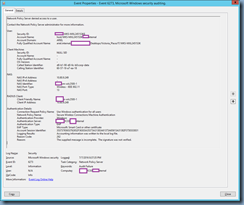
Reviewing the Security event logs on the NPS server show the following event ID 6273 Audit Failure event from the Microsoft Windows security auditing source:
Network Policy Server denied access to a user.
Contact the Network Policy Server administrator for more information.
User:
Security ID: contoso\WKS-MXL2451S3K$
Account Name: host/WKS-MXL2451S3K.contoso.internal
Account Domain: contoso
Fully Qualified Account Name: contoso.internal/contoso/Computers/Desktops/Victoria_Place/IT/WKS-MXL2451S3K
Client Machine:
Security ID: NULL SID
Account Name: -
Fully Qualified Account Name: -
OS-Version: -
Called Station Identifier: d8-b1-90-d0-6c-b0:corp-data
Calling Station Identifier: 60-57-18-a7-ea-18
NAS:
NAS IPv4 Address: 10.80.9.249
NAS IPv6 Address: -
NAS Identifier: contosobm-wlc2500-1
NAS Port-Type: Wireless - IEEE 802.11
NAS Port: 13
RADIUS Client:
Client Friendly Name: contosobm-wlc2500-1
Client IP Address: 10.80.9.249
Authentication Details:
Connection Request Policy Name: Use Windows authentication for all users
Network Policy Name: Secure Wireless Connections Machine Authentication
Authentication Provider: Windows
Authentication Server: SVRARDC03.contoso.internal
Authentication Type: EAP
EAP Type: Microsoft: Smart Card or other certificate
Account Session Identifier: 35373765653762652F36303A35373A31383A61373A65613A31382F3730333831
Logging Results: Accounting information was written to the local log file.
Reason Code: 262
Reason: The supplied message is incomplete. The signature was not verified.
Solution
The key indicator of what would be causing this issue is the following line in the security event entry:
Reason: The supplied message is incomplete. The signature was not verified.
This usually indicates that the certificate presented by the NPS (RADIUS) server is not trusted by the wireless client. The wireless client in this situation was not joined to the domain and since the certificate used by the server to verify its identity:
… is signed by an internal Microsoft CA, the wireless client did not trust it. To correct the issue, simply export the Root and any intermediate CA certificates and import it onto the wireless client’s local computer store.











1 comment:
This article appears close to my issue, however all of the machines were working, now they are no longer able to connect. I renewed one of the certificates that had expired in the personal store of the NPS server but outside of that and I am not able to determine the cause. How should I approach this?
Post a Comment