Problem
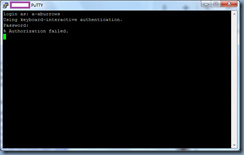
You’ve configured AAA authentication for a Cisco switch with IOS 12.2(55)SE5 to use a Microsoft NPS server as a RADIUS server to allow Active Directory account authentication but noticed that only certain users are able to login while others receive the error message: Authorization failed
You troubleshoot the issue by performing a AAA debug session for an account that you are able to login with and an account that you are unable to. Comparing the outputs show the following differences highlighted in RED:
Successful Login
1y28w: RADIUS: User-Name [1] 8 "a-tluk"
1y28w: RADIUS: User-Password [2] 18 *
1y28w: RADIUS: NAS-Port [5] 6 2
1y28w: RADIUS: NAS-Port-Id [87] 6 "tty2"
1y28w: RADIUS: NAS-Port-Type [61] 6 Virtual [5]
1y28w: RADIUS: Calling-Station-Id [31] 13 "10.10.10.205"
1y28w: RADIUS: NAS-IP-Address [4] 6 192.168.254.253
1y28w: RADIUS(000003EB): Started 5 sec timeout
1y28w: RADIUS: Received from id 1645/8 10.21.1.72:1812, Access-Accept, len 97
1y28w: RADIUS: authenticator D0 8C 90 31 B5 D7 E9 6B - 77 5F 27 B6 5A 2B 66 53
1y28w: RADIUS: Service-Type [6] 6 NAS Prompt [7]
1y28w: RADIUS: Class [25] 46
1y28w: RADIUS: 70 47 06 45 00 00 01 37 00 01 02 00 0A 15 01 48 00 00 00 00 09 C9 33 0D 64 7B EA 12 01 D0 72 08 20 97 22 7B 00 00 00 00 00 00 00 15 [ pGE7H3d{r "{]
1y28w: RADIUS: Vendor, Cisco [26] 25
1y28w: RADIUS: Cisco AVpair [1] 19 "shell:priv-lvl=15"
1y28w: RADIUS(000003EB): Received from id 1645/8
1y28w: AAA/AUTHOR (0x3EB): Pick method list 'user-authorization' - PASS
1y28w: AAA/AUTHOR/EXEC(000003EB): processing AV priv-lvl=15
1y28w: AAA/AUTHOR/EXEC(000003EB): processing AV service-type=7
1y28w: AAA/AUTHOR/EXEC(000003EB): Authorization successful
1y28w: RADIUS/ENCODE(000003EB):Orig. component type = EXEC
1y28w: RADIUS(000003EB): Config NAS IP: 192.168.253.253
1y28w: RADIUS(000003EB): Started 5 sec timeout
1y28w: RADIUS: Received from id 1646/6 10.10.2.72:1813, Accounting-response, len 20
Failed Login
1y28w: RADIUS: User-Name [1] 12 "a-aburrows"
1y28w: RADIUS: User-Password [2] 18 *
1y28w: RADIUS: NAS-Port [5] 6 2
1y28w: RADIUS: NAS-Port-Id [87] 6 "tty2"
1y28w: RADIUS: NAS-Port-Type [61] 6 Virtual [5]
1y28w: RADIUS: Calling-Station-Id [31] 13 "10.10.10.205"
1y28w: RADIUS: NAS-IP-Address [4] 6 192.168.254.253
1y28w: RADIUS(000003E9): Started 5 sec timeout
1y28w: RADIUS: Received from id 1645/6 10.21.1.72:1812, Access-Accept, len 97
1y28w: RADIUS: authenticator D0 95 9A 7C EE 63 A9 AD - BB CA 8B BB 8B DE 1C 05
1y28w: RADIUS: Service-Type [6] 6 Callback Framed [4]
1y28w: RADIUS: Class [25] 46
1y28w: RADIUS: 70 45 06 43 00 00 01 37 00 01 02 00 0A 15 01 48 00 00 00 00 09 C9 33 0D 64 7B EA 12 01 D0 72 08 20 97 22 7B 00 00 00 00 00 00 00 13 [ pEC7H3d{r "{]
1y28w: RADIUS: Vendor, Cisco [26] 25
1y28w: RADIUS: Cisco AVpair [1] 19 "shell:priv-lvl=15"
1y28w: RADIUS(000003E9): Received from id 1645/6
1y28w: AAA/AUTHOR (0x3E9): Pick method list 'user-authorization' - PASS
1y28w: AAA/AUTHOR/EXEC(000003E9): processing AV priv-lvl=15
1y28w: AAA/AUTHOR/EXEC(000003E9): processing AV service-type=4
1y28w: AAA/AUTHOR/EXEC(000003E9): received invalid service type 4
1y28w: AAA/AUTHOR/EXEC(000003E9): Authorization FAILED
*Sep 15 14:40:24: %SYS-5-CONFIG_I: Configured from console by admin on vty0 (10.10.10.205)
TCH-2nd-3750-3#
Solution
After realizing that the Service-Type was being set incorrectly for the user account, I opened up the problematic user’s account properties to check the Dial-in tab and immediately noticed that the Callback Option was set to Set by Caller (Routing and Remote Access Service only):
Meanwhile, for the user who was able to successfully login had the Callback Option set to No Callback:
To correct this issue, either configure the problematic user accounts’ Callback Option to No Callback, or change the NPS policy to Ignore user account dial-in properties as such:

![clip_image002[4] clip_image002[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEij1h-XVHfmsadPaPvB3ZnBpKSx4YjzYNbisS5aHRwxP9-NNUSqVsaGTxfY_SptRFdQ7JPU9znqi0GeiWsv0JjpQ6iJP3zwxtwhyphenhyphenMDRGv6g-kJZpE3ydACoDWSsoyQsXprAVwTjB8JNGqdZ/?imgmax=800)
![clip_image002[6] clip_image002[6]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEj-W5n7OU1Yi5_AvY7u-yLJGRhOl0hAPXIw-lZecHtJRVvi8roEWjmw-HGsmUGV0gz08WJFjX3F0MU3DyM0c4PDQh3OicEiP5BF9YqKrRNvmZJVXRyG9tXlCNLlPmB5RT01l9EYtptifWJh/?imgmax=800)
No comments:
Post a Comment