One of the most frequent issues I’ve had with Microsoft terminal and Citrix XenApp servers is preventing Active Directory user and computer policies from being applied to these servers. The computer policies are easy enough to block with the Block Inheritance feature within the Group Policy Management Console but blocking user policies isn’t as straight forward and since I’ve been asked enough times on how to do it and how it works, this post will serve as something I can point other colleagues to reference.
**Note that I don’t have any screenshots with servers as examples so I’m going to use workstation computer objects instead.
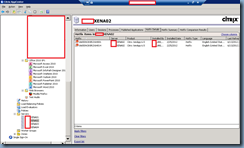
The following screenshot shows the OU named Bunch of User Policies followed with a sub OU named Prevent User Policies. There is also an account named CCS Admin in the Bunch of User Policies OU:
The idea here is that the OU named Bunch of User Policies has various user and computer policies applied to it as shown in the following:
- Office 2010 <— User policy
- Office 2010 Customizations <— User policy
- View Client Customizations <— User and Computer policy
Executing gpresult on the Windows 7 desktop in the OU named Prevent User Policies will show that following user policies are applied to the CCS Admin account:
- Office 2010 <— User policy
- Office 2010 Customizations <— User policy
- View Client Customizations <— User and Computer policy
- Default Domain Policy
- Local Group Policy
Blocking Computer Policies
The computer policy View Client Customizations is easy enough to block by using the Block Inheritance feature on the OU named Prevent User Policies (sorry about the name, this should have been named Prevent User and Computer Policies) and moving the computer object CCSAdmin into the OU:
Note how a gpresult now shows that only the:
- Local Group Policy
… is applied:
Blocking User Policies
With the computer policies blocked, the next step is to block out the user specific policies as shown from the gpresult:
- Office 2010 <— User policy
- Office 2010 Customizations <— User policy
- View Client Customizations <— User and Computer policy
- Default Domain Policy
- Local Group Policy
What we need to do is to create a new GPO loopback policy and configure it in replace mode then apply it to the OU containing the computer object that you do not want user policies applied to:
Navigate to Computer Configuration –> Administrative Templates –> System –> Group Policy –> User Group Policy loopback processing mode:
Enable the policy and set the Mode to Replace:
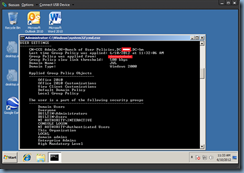
With the loopback policy applied, a gpresult will show the following:
Computer Settings
- Loopback Replace Mode
- Local Group Policy
User Settings
- Local Group Policy
Notice how we have successfully removed both the computer and user policies from this computer object for any user that logs in. One of the other questions that come up quite often is how we can block user logon scripts configured in the Active Directory account’s Profile tab and unfortunately, there is no easy way to do this with policies. The only alternative I know of is to actually modify the logon script to check what computer object the user is logging onto and then filter it.
















![clip_image002[8] clip_image002[8]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjJHJbGYmoMlZg9C3vR5kDFc0bjaeWEbA1parMhZCIBJDJcxHQkwhtHYTnsK2FS6DsgnRw6vZm4rXccjWTHhYmALzkRsdWTwSqwH9FvdfWBLB_6bvIOEYnDJuLhVQSMIyHXI13mUED1my5M/?imgmax=800)



![clip_image002[6] clip_image002[6]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi5aWZmnAdoHnKODK-NzOja1PNxBu4LRFx6DkuNj466Hu-EnBIuK65fTPc4UMlMYLDR_pHKbBb0sBJHZ-w0ewNAmGV8p0zLHIwxkXBN-ydb4ExhxPbaMIlRHL8XbMQm1nntVhyIoPkkIHXE/?imgmax=800)
![clip_image002[4] clip_image002[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEj26U0DIY6Odb0wCEfkP5487WINPjzNA-vr8BGFi7UTmEhJIm8qCRWxigQQt7w8BXJKQr5pDDzlabhBphnFzM7gdS7q-JQyUKxc9c7ecAwOITZAXw1fCKhdOhzliZBrmuhc5Er084zZeZWF/?imgmax=800)




![clip_image002[6] clip_image002[6]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhDT6KYpVQaW9Us8M1txsSi6hc5CHg97MtQZgSpYv9g2lN5gQaU6BapiHtALfZ-ra31s7kuyV5Ck2wPozjSbpXuRAs0ZvqLj8C1PXmeZurebPoRP_7VPiYK-5Htf_QXjRiunGqPJa6tvGAx/?imgmax=800)
![clip_image002[4] clip_image002[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEglkc6FDnr9kkXwZpkjaEYYM9IOIMra0TUsrKRbaIY1rKL-wLD5Hvpvj1jzFKdNcMnJ2nNesWeaIS8xrP1jhQfJTWOsU-lU03HRNwb1_q3S1qI_Mf-s73L7MLaoGOtuCOBtTrwJi0Tv5wpv/?imgmax=800)