I’ve recently worked a client who wanted to implement a Two Tier PKI Hierarchy Deployment with Microsoft Certificate Authority services to secure services such as RDP, iLO, VMware and Lync to check off an item on their security auditor’s list during the next visit and since I’ve worked with CAs in the past, I was asked to design and implement this for them. The design wasn’t too involving as I’m just abiding by CA best practices and there are step-by-step walkthroughs on how to deploy a Two Tier PKI Hierarchy as found in the following links:
AD CS Step by Step Guide: Two Tier PKI Hierarchy Deployment
http://social.technet.microsoft.com/wiki/contents/articles/15037.ad-cs-step-by-step-guide-two-tier-pki-hierarchy-deployment.aspx
Installing a Two Tier PKI Hierarchy in Windows Server 2012: Part I, Installing a Root Certification Authority with PowerShell
http://blogs.technet.com/b/xdot509/archive/2012/10/21/installing-a-two-tier-pki-hierarchy-in-windows-server-2012-part-i-installing-a-root-certification-authority-with-powershell.aspx
The deployment of the PKI infrastructure wasn’t difficult and the automation of having servers enroll new certificates for securing RDP with GPO was just as easy as described in the following URL:
Configuring Remote Desktop certificates
http://blogs.msdn.com/b/rds/archive/2010/04/09/configuring-remote-desktop-certificates.aspx
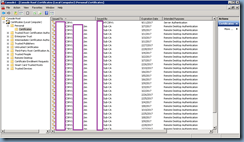
The deployment went without a hitch and because I was also deploying XenDesktop 7 on Windows Server 2012, I went ahead and used those servers for testing. The testing for those Windows Server 2012 servers verified that the auto enrollment via GPO worked so we proceeded to rollout deployment to all of the other servers with the GPO. A few days have passed so I went ahead to log onto a Windows Server 2008 R2 in the environment and to my surprise, I saw that the server’s Local Computer’s Personal Certificate was flooded with duplicate RDP enrollments:
Not exactly a good sight to see and this clearly shows there’s something wrong. Why was this happening to the Windows 2008 servers but not the 2012? A bit of searching turned up this TechNet forum post:
GPO setting "Server Authentication Certificate Template" causes duplicate certificate requests!
http://social.technet.microsoft.com/Forums/en-US/407fc154-d2bb-40f8-a4b6-673c2e36a223/gpo-setting-server-authentication-certificate-template-causes-duplicate-certificate-requests?forum=winserverGP
… which indicated that this would happen if the Template display name was different than the Template name and to no surprise, my Template display name had spaces but my Template name did not since it’s not allowed:
Since you can’t actually change the Template display name, what I ended up doing was simply deleting the template and recreating it as such:
It looks like this has been fixed in Windows Server 2012 but not 2008 or 2003.

![clip_image001[5] clip_image001[5]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjHtsDL2e8ZNskdXsgRNZg_tWhuIQfQezzx5b4CpVDtTedO7dNPdcXGjDiZ9lvhkeBRrsmNRDgXv8AvLxRqHQsJI8AB4aDjgfj2fEEl_gctrwl4wTYhdNddlFwEc1KkL2nisNW5t7_mTcGX/?imgmax=800)
1 comment:
Very helpful article ! I was always curious about all these complex algorithms that are being used in these ssl encryptions.
Post a Comment