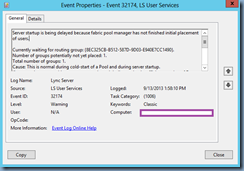
I’ve been working with a client that had two new offices opening in London with HP t610 thin clients as desktops to access the XenDesktop 5.6 environment I built last year at their Bermuda office. This weekend was the actual deployment and we noticed that the Lync clients within their VDIs wasn’t fully functional which then kicked off a 5 hour troubleshooting exercise on Saturday and another 5 hours on Sunday until we got it going. As I’ve been extremely busy lately with multiple projects on the go and haven’t been blogging as much, I felt it was important to set aside a bit of time today to just dump all of the information I have in my head that was required to get this going. Sorry about format as it’s not very organized so I’ll follow up with a proper post demonstrating the process step by step.
Problem
You have the Lync 2013 client installed onto a Windows 7 Citrix XenDesktop virtual desktop and you noticed that the client correctly finds the Video Device as the Citrix HDX Web Camera and it works as expected:
… but when you click on the Audio Device, you see the following:
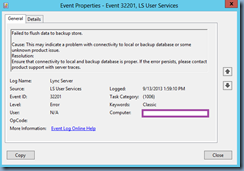
We didn’t find an audio device, which you need for calling
If you have one already, try checking Windows Device Manager to make sure it’s installed and working.
Learn More
The problem appears to be that the Lync 2013 client does not like or see the Citrix HDX Audio device:
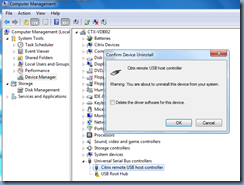
One of the more prominent solutions in Citrix forum posts is to remove the Citrix remote USB bus and Citrix remote USB host controller as such:
Citrix remote USB bus
Warning: You are about to uninstall this device from your system.
Delete the driver software for this device.
Citrix remote USB bus controller
Warning: You are about to uninstall this device from your system.
Delete the driver software for this device.
Once removed, restart the Lync 2013 client and the audio device will now get picked up:
Video and audio calls work as expected but as we all know, if the desktop is shutdown or restarted, these drivers would get reinstalled and if they’re not present, USB redirection of, say, USB flash drives does not appear to work. I suppose it is possible to use the Delete the driver software for this device. checkbox is an option but I prefer not to permanently remove the device or the driver. The Citrix blog post here: http://blogs.citrix.com/2013/04/05/tech-preview-of-xenapp-support-for-the-lync-2013-vdi-plug-in/ has a lot of comments at the bottom with users discussing the issue but appears to not have a resolution.
Another interesting article from TechNet demonstrating how Lync 2013 should work in a VDI desktop can be found here:
Update: Microsoft Lync 2013 in a Virtual Desktop Infrastructure
http://blogs.technet.com/b/nexthop/archive/2012/07/31/microsoft-lync-2013-preview-in-a-virtual-desktop-infrastructure.aspx
Troubleshooting steps out there:
Removing Power Saving Mode for USB Root Hub
One of the suggestions found here: http://forums.citrix.com/thread.jspa?threadID=332025
… and here: http://social.technet.microsoft.com/Forums/lync/en-US/30ec9d70-2cca-40be-b9dc-be7763e3530a/lync-2013-client-no-audio-device-detected suggests to uncheck:
Allow the computer to turn off this device to save power
… in the device manager for each and every USB Root Hub and Generic USB Hub but the problem with this solution is that the option is not available for the Citrix remote USB bus and Citrix remote USB host controller. While this option is usually available for the USB Root Hub, the VDI does not have the proper driver installed for this component:
Device status
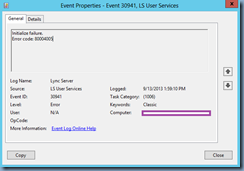
This device is not working properly because Windows cannot load the drivers required for this device. (Code 31)
Furthermore, the post appears to be for an actual physical desktop.
Solution
As per the following Citrix article, there appears to be a few steps outlined by Citrix to get this to work:
XenDesktop 7, XenApp 6.x and Citrix Receiver 4.0 Support for Microsoft Lync 2013 VDI Plug-in
http://support.citrix.com/article/CTX138408
Step #1 – Update Citrix Receiver on the HP t610 thin client
Finally, I went ahead to check the t610 thin client’s receiver and noticed that it was version 13.x.x.xx so upgraded it to 14.
Step #2 – Enable EnableMediaRedirection In Lync 2013 Server
Begin by logging onto the Lync 2013 Server and use the:
Set-CsClientPolicy -EnableMediaRedirection $TRUE
… on the global policy or whatever policy you use for your users.
Step #3 – Install Microsoft Lync VDI Plug-in
Install the Microsoft Lync VDI Plug-in onto the HP t610 Windows embedded thin client from here:
Microsoft Lync VDI 2013 plugin (32 bit)
http://www.microsoft.com/en-us/download/details.aspx?id=35457
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
**Note that if you receive a The installation of this package failed. error while installing the VDI plugin, extract the installer with:
lyncvdi.exe /extract:c:\lync
Then run:
setup.exe /admin
… to bring up the office customisation app, close it then run:
setup.exe
… to get it to install.
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
Step #4 – XenDesktop VDA version 7
Uninstall the Citrix XenDesktop 5.6 VDA agent on the pooled desktop’s master image, installed XenDesktop 7 VDA and pushed it out.
Step #5 – Enable Remote Recording
Another interesting blog post I found which I’m not sure whether is needed but configured it anyway was the following:
Lync deployment: using Virtual Desktops (VDI)
http://itbasedtelco.wordpress.com/2013/06/17/lync-deployment-using-virtual-desktops-vdi/
… that demonstrated how to configure this for RDS which included an additional registry key to add:
REG ADD “HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp” /v fDisableAudioCapture /t REG_DWORD /d 0 /f
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
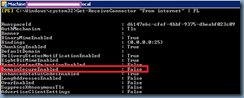
Step #6 – Configure additional registry keys to specify internal and Lync Server 2013’s external server address:
With all of the above done, Lync now will now display the message:
Lync is trying to use your local audio and video
… but then displays:
Lync is not yet connected to Local Audio and Video Devices
What was necessary to get Lync to connect to the local audio was to manually add the following registry keys to the thin client:
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\15.0\Lync]
"ConfigurationMode"=dword:00000001"
"ServerAddressInternal"="yourLyncServer.domain.local"
"ServerAddressExternal"="yourExternalEdge.domain.com"
Step #7 – Install RDP Updates
Ensure that the following RDP updates are installed onto the thin client:
- KB2592687: Description of the Remote Desktop Protocol 8.0 update for Windows 7 SP1 and Windows Server 2008 R2 SP1, released October 24, 2012, and its prerequisite
- KB2574819: An update is available that adds support for DTLS in Windows 7 SP1 and Windows Server 2008 R2 SP1, released October 23, 2012
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
After all the steps have been completed, proceed with restarting the thin client. The Lync 2013 VDI plugin should successfully pair up with the Lync client once the thin client has been restarted as you will notice a Lync 2013 prompt to enter your Sign-in address, User name and Password. Both audio and video should work from the Lync client now. If you’re still having issues, review the applications installed onto the thin client and remove any packages such as ones for the webcam or audio devices that may conflict with the VDI plugin.
I’ll be preparing a more detailed post on how to configure all of this when I get more time. Hope this helps anyone out there who may be looking for more information on getting this to work.