I’ve recently noticed that while I’ve written blog posts about Citrix User Profile Management, I haven’t actually written one for VMware View’s Persona Management that is bundled with VMware View 5.0 and later. As some other VMware View professionals know, there are benefits and drawbacks to using floating and dedicated assignment pools. I personally prefer using floating assignment pools whenever I can due to licensing benefits (I can use less licenses for more users) and avoid having a user unable to work because there’s something wrong with their desktop (good old “agent unreachable” issues). The problem with floating assignment pools is that a user can potentially log onto any desktops available in the pool and this does not work well for users who needs to maintain persistent data or customizations to their desktops. Microsoft’s native Redirected Desktops delivers part of the solution but as we all know, it doesn’t roam certain settings (i.e. signature assignments in Outlook) and this is where Persona Management comes in. I won’t go into too much detail about what Persona Management can or cannot do as this blog post is more of a reference for me to use in the future when I’m setting up an environment for a customer.
Configure summary:
VMware View’s Persona Management will be used to maintain profiles across floating assignment pool desktops for users but folder redirection will be used for common user folders so users directly access files from a fileserver.
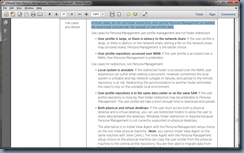
I understand that VMware’s VMware View™ Persona Management guide found in the following URL: http://www.vmware.com/files/pdf/view/VMware-View-Persona-Management-Deployment-Guide.pdf
… specifically states the following on page 23:
In most cases, do not use folder redirection, and use the Persona Management as-needed file downloads and periodic file uploads of user profile data.
An explanation of various use cases for Persona Management and Redirected folders are explained in more detail in the guide but as with every solution, the environment you’re working with usually drives the type of design for the implementation. Most of the environments I work with span multiple countries but the servers are either usually centralized in a single location or if multiple datacenters exist, are connected through a fast WAN link. This is why I choose to use redirected folders so that files are saved instantly on file servers and, more importantly, decrease the amount of storage required on the virtual desktops. As nice as VMware provides the flexibility of managing the where and when profiles are dynamically uploaded to a repository, I prefer redirected profiles because of the following:
- Less storage required for the virtual desktop’s C drive since files and folders are directly saved onto the file server
- Ability to set quotas for redirected folders via Windows Server 2008 Quota Management
With the reasoning behind why I went with this configure, let’s proceed with demonstrating the settings configured.
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
Step 1 – Create Repository Folder Shares
The first step is to create the repository folder shares for:
- Persona Management
- Redirected Folders
For this example, I’ve created a folder named Profiles with 2 sub folders named:
- Persona
- Redirected
Both of the folders above should be set with the same share and security permissions so I’ll just demonstrate setting up the Persona share.
The share settings should be set to Full control:
**Note that whether the share is a hidden share with the $ sign appended to the end is optional.
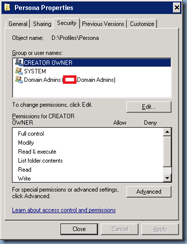
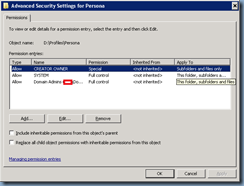
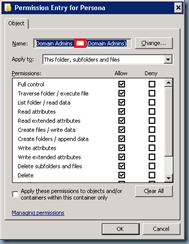
The NTFS security permissions should have the user names and Include inheritable permissions from this object’s parent cleared and set with the following permissions:
CREATOR OWNER:
Apply to: Subfolders and files only
Permissions: Full Control
Apply to: This folder, subfolders and files
Permissions: Full Control
CREATOR OWNER:
Apply to: This folder, subfolders and files
Permissions: Full Control
**Note that I understand that as per the VMware View Administration guide on page 177:
… VMware recommends following the following TechNet article to configure the folder permissions:
Security Recommendations for Roaming User Profiles Shared Folders
http://technet.microsoft.com/en-us/library/cc757013%28WS.10%29.aspx
… and whether you would like to use the settings as shown in the article above is up to you.
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
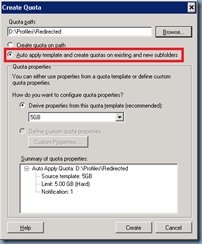
Although not covered by VMware’s Personal Management guide, I prefer to set quotas on the redirected folders because that would prevent users from filling up the file server if they were ever to download large files. I won’t go into how to configure quotas as the following article does a good job demonstrating it:
Create an Auto Apply Quota
http://technet.microsoft.com/en-us/library/cc731577.aspx
The only note I’d like to make is to ensure that you select Auto apply template and create quotas on existing and new subfolders while creating the quota or you’ll inadvertantly set the quota limit to be the aggregate of all the users’ redirected folders:
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
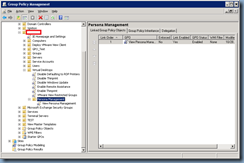
Step 3 – Import ADM and configure Group Policy Object
Once the repository folder shares and quota have been created, the next step is to create a new GPO, edit the settings and import the Persona Management ADM into the policy. The ADM can be found at the following location on the View Connection Server:
C:\Program Files\vmware\VMware View\Server\extras\GroupPolicyFiles
The ADM we’ll be loading is named ViewPM.adm:
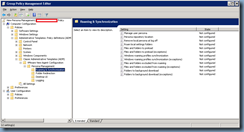
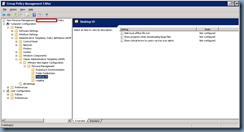
Once the ADM has been imported, proceed by navigating to Computer Configuration –> Administrative Templates –> Classic Administrative Templates (ADM) –> VMware View Agent Configuration –> Persona
Management and you’ll see the following settings available:
Proceed with configuring the Persona Management settings as such:
Computer Configuration –> Administrative Templates –> Classic Administrative Templates (ADM) –> VMware View Agent Configuration –> Persona
Management –> Roaming & Synchronization
Manage user persona – Enabled
Profile upload interval (in minutes): – 10
Files and folders excluded from roaming – Enabled
Value:
- My Music
- My Videos
- Saved Games
The reason why I’ve chosen to exclude these folders is because I do not want files in these folders stored on the server. I’ve also been asked before why I would need to configure this setting if I wasn’t going to configure these folders in the redirected settings (below) to redirect and the answer is because if we don’t configure it here, the folders would still be saved in the persona repository.
**Note that you will need to ensure users are aware that files stored in these folders are not preserved.
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
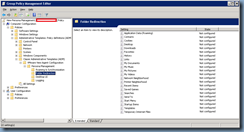
Computer Configuration –> Administrative Templates –> Classic Administrative Templates (ADM) –> VMware View Agent Configuration –> Persona
Management –> Folder Redirection
Application Data (Roaming) – Enabled
Redirect to the following location - \\<fileServer>\Redirected$\%username%\AppData
Contacts – Enabled
Redirect to the following location - \\<fileServer>\Redirected$\%username%\Contacts
Cookies – Enabled
Redirect to the following location - \\<fileServer>\Redirected$\%username%\Cookies
Desktop – Enabled
Redirect to the following location - \\<fileServer>\Redirected$\%username%\Desktop
Downloads – Enabled
Redirect to the following location - \\<fileServer>\Redirected$\%username%\Downloads
Favorites – Enabled
Redirect to the following location - \\<fileServer>\Redirected$\%username%\Favorites
History – Enabled
Redirect to the following location - \\<fileServer>\Redirected$\%username%\History
Links – Enabled
Redirect to the following location - \\<fileServer>\Redirected$\%username%\Links
Redirect to the following location - \\<fileServer>\Redirected$\%username%\My Documents
… and repeat the following for all of the settings except for the following:
- My Music
- My Videos
- Saved Games
Note that these are settings that I prefer and that this may need some tweaking depending on the environment.
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
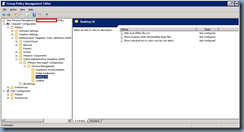
Computer Configuration –> Administrative Templates –> Classic Administrative Templates (ADM) –> VMware View Agent Configuration –> Persona
Management –> Desktop UI
I usually don’t make any changes to these settings because:
- I typically use redirected folders and therefore eliminate the need to notify users when large files are being transferred
- Sometimes it’s better to not confuse users with popup messages
Again, feel free to configure these settings if required.
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
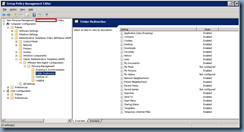
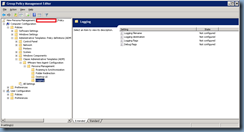
Computer Configuration –> Administrative Templates –> Classic Administrative Templates (ADM) –> VMware View Agent Configuration –> Persona
Management –> Logging
I usually leave these settings as Not configured but whether you customize the logging settings will be up to you.
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
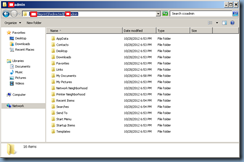
Step 4 – Apply the Group Policy Object to the Virtual Desktop Computer Object
With the GPO configured, proceed with applying the policy to the virtual desktops you would like to have Persona Management turned on. Note that the policy contains settings that are applied to computer objects so do not apply them to user accounts:
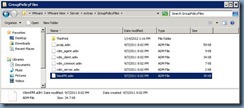
Now when users logs onto the desktops with this GPO applied, their files and folders should be redirected to the configured repositories:
![clip_image002[6] clip_image002[6]](http://lh6.ggpht.com/-8c9ggVCT4dA/UI5pbNVH_GI/AAAAAAAASJc/qkdgIuh3XrU/clip_image0026_thumb.jpg?imgmax=800)
![clip_image002[8] clip_image002[8]](http://lh4.ggpht.com/-6VTZDJmfqUQ/UI5pdFWJDDI/AAAAAAAASJs/cn7MdGq1DYo/clip_image0028_thumb.jpg?imgmax=800)
![clip_image002[10] clip_image002[10]](http://lh3.ggpht.com/-74YgXPXikqQ/UI5pe43JJDI/AAAAAAAASJ8/bHkPAUhS0HQ/clip_image00210_thumb.jpg?imgmax=800)
![clip_image002[12] clip_image002[12]](http://lh3.ggpht.com/-ls6TMro49JQ/UI5pj2NtyfI/AAAAAAAASKs/2kS4ZVXJ0gY/clip_image00212_thumb.jpg?imgmax=800)
![clip_image002[14] clip_image002[14]](http://lh3.ggpht.com/-guhUJ-KfYYE/UI5plSSDS8I/AAAAAAAASK8/t9fuZqH1vq4/clip_image00214_thumb.jpg?imgmax=800)

![clip_image002[4] clip_image002[4]](http://lh5.ggpht.com/-0Av9pcPqrfo/UI5p5MryPcI/AAAAAAAASNM/ryFwXD5miJY/clip_image0024_thumb.jpg?imgmax=800)
![clip_image002[18] clip_image002[18]](http://lh3.ggpht.com/-z45iw3Oyzgs/UI5p7JdYxBI/AAAAAAAASNc/aNw0qSLvN04/clip_image00218_thumb.jpg?imgmax=800)
![clip_image002[20] clip_image002[20]](http://lh6.ggpht.com/-4dmnno2U9JE/UI5p8sl9lDI/AAAAAAAASNs/gwUK5e9t1a4/clip_image00220_thumb.jpg?imgmax=800)
![clip_image002[6] clip_image002[6]](http://lh4.ggpht.com/-a6IvT0oqOJg/UIaUAhOzXSI/AAAAAAAASA4/Cy0eyXhqK0w/clip_image002%25255B6%25255D_thumb.jpg?imgmax=800)
![clip_image002[8] clip_image002[8]](http://lh4.ggpht.com/-upuvB51xOqk/UIaUBxZWHYI/AAAAAAAASBI/SJgnekOlDVA/clip_image002%25255B8%25255D_thumb.jpg?imgmax=800)
![clip_image002[10] clip_image002[10]](http://lh3.ggpht.com/-LxtgHXt5-MU/UIaUP6cBOMI/AAAAAAAASDY/NbQuTAdeh5s/clip_image002%25255B10%25255D_thumb.jpg?imgmax=800)
![clip_image002[12] clip_image002[12]](http://lh3.ggpht.com/-c4Leou22EWI/UIaUSeEHBGI/AAAAAAAASD4/vxZKQAAyf1k/clip_image002%25255B12%25255D_thumb.jpg?imgmax=800)
![clip_image002[14] clip_image002[14]](http://lh5.ggpht.com/-s-57PMoNfUs/UIaUTodYkBI/AAAAAAAASEI/uJ364efMy4E/clip_image002%25255B14%25255D_thumb.jpg?imgmax=800)
![clip_image002[16] clip_image002[16]](http://lh6.ggpht.com/-zCmXV7gDCL4/UIaUUrGpjTI/AAAAAAAASEY/jKAGvHJgDpE/clip_image002%25255B16%25255D_thumb.jpg?imgmax=800)
![clip_image002[18] clip_image002[18]](http://lh5.ggpht.com/-xdKWntyPASI/UIaUVpkIJ8I/AAAAAAAASEo/lzX44vKgKA4/clip_image002%25255B18%25255D_thumb.jpg?imgmax=800)
![clip_image002[20] clip_image002[20]](http://lh4.ggpht.com/-p1o32XFa3P8/UIaUWsfTSCI/AAAAAAAASE4/9aHrx8RU7ZY/clip_image002%25255B20%25255D_thumb.jpg?imgmax=800)
![clip_image002[22] clip_image002[22]](http://lh4.ggpht.com/-8ki-M-JVd6U/UIaUaXt0wUI/AAAAAAAASFY/RW7Mg4KIQTo/clip_image002%25255B22%25255D_thumb.jpg?imgmax=800)