A colleague of mine recently had to quickly set up a new UCS B series chassis and since we were deploying the new B230 M1 blades, the chassis was actually shipped with UCSM 1.4(1a). The initial setup of the clustered Fabric Interconnects were pretty much the same but one of the behavior my colleague experienced was that a password strength / complexity check was now enforced (turned on). He was in sort of a rush and couldn’t find the option to turn it off so he went ahead and set the password to meet the requirements. Since I’m am now back from vacation and assigned the task to configure the blades to boot from SAN, he asked if I could turn it off.
While the this task is seemingly trivial, it did take me a few minutes to find the checkbox so I figure I’d write a post in case someone needs to find a quick answer through searching it with Google.
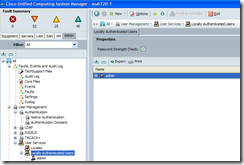
Disabling Password Strength / Complexity Check with the GUI
Log into the UCSM:
Navigate to the Admin tab, drill down the nodes: All –> User Management –> User Services –> Locally Authenticated Users and in the right window, uncheck the Password Strength Check checkbox:
Once you’ve unchecked the checkbox, proceed with clicking the Save Changes button on the bottom right hand corner.
Disabling Password Strength / Complexity Check with the CLI
To disable this via the CLI, SSH to your fabric interconnect’s IP address and login. Proceed and type the following commands:
- scope security
- set enforce-strong-password no
- commit
The output should look something like this:
login as: admin
Cisco UCS 6100 Series Fabric Interconnect
Using keyboard-interactive authentication.
Password:
Using keyboard-interactive authentication.
Cisco Nexus Operating System (NX-OS) Software
TAC support: http://www.cisco.com/tac
Copyright (c) 2002-2010, Cisco Systems, Inc. All rights reserved.
The copyrights to certain works contained in this software are
owned by other third parties and used and distributed under
license. Certain components of this software are licensed under
the GNU General Public License (GPL) version 2.0 or the GNU
Lesser General Public License (LGPL) Version 2.1. A copy of each
such license is available at
http://www.opensource.org/licenses/gpl-2.0.php and
http://www.opensource.org/licenses/lgpl-2.1.php
wu6120-1-B# scope security
wu6120-1-B /security # set enforce-strong-password no
wu6120-1-B /security* # commit
wu6120-1-B /security # show enforce-strong-password
Password Strength Check: No
Pretty simple right?


No comments:
Post a Comment