I’ve been keeping a close eye on when Cisco was going to release their UCS B Series infrastructure 2.0 firmware ever since VMware released vSphere 5 as many customers wanted to know whether they could begin testing how stable the new hypervisor would run in their existing infrastructure. Needless to say, I was extremely excited when Cisco released the firmware a little more than a week ago. With that being said, I didn’t have any time to try out the new firmware until mid last week when I was providing UCS training a customer. Since it was my first time upgrading the firmware and I was explaining the process step-by-step, I took the opportunity to screenshot every step so I could write this blog. What I noticed during the upgrade was how much more content Cisco included to show how to validate and test the firmware for administrators who are upgrading their production infrastructure. While the process was very much the same as the 1.x version with some minor differences in ordering, I have to say Cisco did a great job with the extra content they included.
I’m going to by pass the overview, downloading and prerequisites section of the upgrade guide but if you’re performing this upgrade to your production environment, please go through those sections and the release notes so you can be aware of any issues that may pertain to your environment.
Begin by ensuring that you have the correct firmware packages uploaded to your 6100 series fabric interconnects:

Updating the Firmware on the Adapters, CIMCs, and IOMs
From within UCS Manager, navigate to the Equipment tab, click on the Equipment node, Firmware Management tab, Installed Firmware sub-tab and finally the Upgrade Firmware button:

From within the Update Firmware Window, select ALL for the Filter list and 2.0(1m) for the Set Version list:
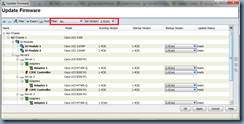
Proceed with clicking on the Apply button and you’ll notice the Update Status field on the right change from ready to updating:

Click on the OK button to close the Update Firmware window and continue monitoring the status from within the Installed Firmware sub-tab window:

Continue waiting until the status for all of the components is listed as ready:

Activating the Firmware on the Adapters
Now that the firmware is updated, we can proceed with activating the firmware on all of the components and the first set of components to activate are the adapters. Proceed with clicking on the Activate Firmware button from the Equipment tab, Equipment node, Firmware Management tab, Installed Firmware sub-tab:

From within the Activate Firmware Window, select Adapters for the Filter list, 2.0(1m) for the Set Version list, check the Ignore Compatibility Check and Startup Version Only check box:

Continue by clicking the Apply button and you’ll see the status of the activation in the Activate Status column:

Click on the OK button to close the Activate Firmware window and continue monitoring the status from within the Installed Firmware sub-tab window until you see the status for all of the adapters being listed as pending-next-boot:

Activating the Firmware on the CIMCs
Now that the firmware for the adapters have been activated, proceed with activating the firmware for the CIMCs by opening up the Activate Firmware window and select CIMC for the Filter list, 2.0(1m) for the Set Version list, check the Ignore Compatibility Check and Startup Version Only check box:

Continue by clicking the Apply button and you’ll see the status of the activation in the Activate Status column:
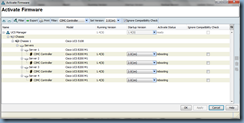
Click on the OK button to close the Activate Firmware window and continue monitoring the status from within the Installed Firmware sub-tab window until you see the status for all of the CIMCs being listed as ready:

Activating the Board Controller Firmware on a Server
Unfortunately, I didn’t have any B440 blades in the environment we had in our demo infrastructure so I won’t be able to provide screenshots for it. Please refer to the manual for more details:

Activating the Cisco UCS Manager Software to Release 2.0
Proceed with activating the firmware for the UCS Manager by opening up the Activate Firmware window and select UCS Manager for the Filter list, 2.0(1m) for the Set Version list, check the Ignore Compatibility Check check box:

You’ll be prompted with a warning message as soon as you click on the Apply button:

Once you’ve answered Yes to the warning message, you’ll be brought back to the Activate Firmware window and the Activate Status will now read scheduled:

Click on the OK button to close the Activate Firmware window and continue waiting till you lose your connection to UCS Manager:



Give the 6100 series fabric interconnects to activate the UCS Manager and within a minute or two, you’ll be able to reconnect again:


Once you’re back into UCS Manager, you should now see that the UCS Manager has 2.0(1m) listed as the Running Version:

Activating the Firmware on the IOMs
Proceed with activating the firmware for the IOMs by opening up the Activate Firmware window and select IOM for the Filter list, 2.0(1m) for the Set Version list, check the Ignore Compatibility Check and Startup Version Only check box:

Continue by clicking the Apply button and you’ll see the status of the activation in the Activate Status column:

Click on the OK button to close the Activate Firmware window and continue monitoring the status from within the Installed Firmware sub-tab window until you see the status for all of the IOMs being listed as Pending Next Boot.
Activating the Fabric Interconnect Firmware for a Cluster Configuration
Activating the firmware on the fabric interconnects requires a specific order so the first step is to identify which fabric interconnect is the primary and subordinate. This can be easily done by expanding the Fabric Interconnects node under the Equipment tab’s Equipment node:

Once you have identified which fabric interconnect is primary and subordinate, we can proceed with activating the subordinate fabric.
Note that in a VMware ESXi environment, depending on which path the virtual machines are binded to, some of them may experience a slight blip in network disruption when you activate the fabric interconnect. The disruption will be minimal as they will fail over to the other fabric. With that being said, if your environment has sensitive applications that are dependent on other servers, disruptions in services can occur so contact the application owners to determine what the best approach for the firmware upgrade because there will be scenarios where it is best to simply shutdown the servers during the upgrade.
Proceed with ensuring that HA is operating correctly for both the primary and subordinate fabric interconnects:


Once you’ve verified that HA is operating correctly, proceed with opening the Activate Firmware window, set the Startup Version for the subordinate fabric interconnect to 5.0(3)N2(2.1m) and check the Ignore Compatibility Check check box:

Proceed by clicking the Apply button and you’ll see the Activate Status column update to Activating status:

Continue by clicking the OK button to close the Activate Firmware window. From here, navigate to the subordinate fabric interconnect node, open the General tab then scroll down to the Update Status section:
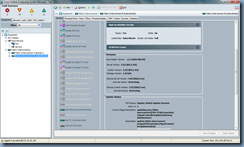
From here, you will be able to monitor the status of the activation:


As with the earlier versions of 1.x, the subordinate fabric interconnect will light up like a christmas tree changing from red, orange, yellow and back to the various available colours with the status’:
Ready: No
State: Down
Failure Reason: Node Down
Leadership: Inapplicable
Cluster Link State: Full
This is all normal so just for the activation to complete:
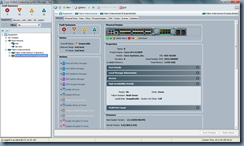
Keep monitoring the High Availability Details section and you will eventually see the status’ revert back to normal:
Ready: Yes
State: Up
Leadership: Subordinate
Cluster Link State: Full
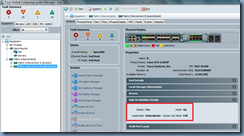
Navigating back to the Installed Firmware tab should now indicate that the firmware version for the Kernel and System is 2.0(1m):

With the subordinate fabric interconnect activated with the new 2.0(1m) firmware, continue with activating the primary fabric interconnect by opening the Activate Firmware window, set the Startup Version for the primary fabric interconnect to 5.0(3)N2(2.1m) and check the Ignore Compatibility Check check box:

Clicking the apply button will prompt you with a warning message indicating that the fabric interconnect will reboot and thus kicking you off of UCS Manager:

Once you have answered Yes to the warning message, you will be returned to the Activate Firmware window where you’ll notice that the Activate Status for the primary firmware is now listed as Activating:

Continue by clicking the OK button to close the Activate Firmware window. From here, navigate to the primary fabric interconnect node, open the General tab then scroll down to the Update Status section:

From here, you will be able to monitor the status of the activation:

The activation process of the primary fabric interconnect will eventually reboot the 6120/6140 so you’ll eventually get kicked out:

You should be able to immediately log back into UCS Manager because the subordinate is supposed to become the primary fabric interconnect:

As with the activation of the subordinate fabric interconnect, the primary will light up like a christmas tree changing from red, orange, yellow and back to the various available colours with the status’:
Ready: No
State: Down
Failure Reason: Node Down
Leadership: Inapplicable
Cluster Link State: Full
This is all normal so just for the activation to complete:

When you see that the High Availability Details listed as:
Ready: No
State: Up
Failure Reason: Chassis Configuration Incomplete
Leadership: Subordinate
Cluster Link State: Full
… you can expect the clustered fabric interconnect to be fully operational soon:
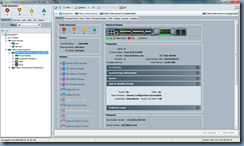
Keep monitoring the High Availability Details section and you will eventually see the status’ revert back to normal:
Ready: Yes
State: Up
Leadership: Subordinate
Cluster Link State: Full

Updating a Management and Host Firmware Package
It’s important that once you have the core components of the UCS B series infrastructure upgraded, you will also need to update the reset of the components on the blade servers. I find that many administrators tend to miss this and what’s nice about the newer firmware versions of 1.4 is that you will actually get warnings about the firmware versions for the blades are old (older firmware never warned you).
Updating a Management Firmware Package
To update the management of the components on the blades, navigate to the Servers tab, Servers node, Policies then right click on the Management Firmware Packages node and select Create Management Firmware Package:

Select the packages for the blades you have in the environment, choose the firmware version and provide a name for this package:

Once you’ve completed your selection, click the OK button and your firmware package will be created:
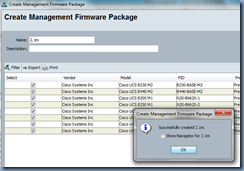
With the new Management Firmware Package created, you have the option of immediately assigning it to your service profile or service profile templates. I prefer to complete the creation of the Host Firmware Packages so I don’t need to go back to the same tab to assign the package again.
Updating a Host Firmware Package
To update the other hardware components on the blades, navigate to the Servers tab, Servers node, Policies then right click on the Host Firmware Packages node and select Create Host Firmware Package:

Select the packages for the blades you have in the environment, choose the firmware version and provide a name for this package:

Make sure you also navigate to the other tabs listed in the window (i.e. Adapter, BIOS, Board Controller, etc):

Once you’ve completed your selection, click the OK button and your firmware package will be created.

With the new packages created, you can now navigate to the Policies tab of the service profile or service profile templates and assign them:

If you were assigning the policies to an actual service profile, you’ll be warned that the operation will cause the blade to reboot:

If you answer yes, your blade will reboot and then go through the updating process:

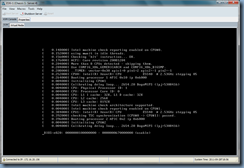
It’s important that you navigate to the Installed Firmware tab to ensure that the components have updated:

… and that’s it. The process is very much the same as 1.x version and while I understand that the manual is extremely straight forward with what needs to be done, I hope this post serves to provide some visual aids through the use of screenshots to demonstrate what the process looks like.