I’ve recently been asked quite a few times in over the last few months on how to properly request and issue certificates for VMware View servers ever since the later versions of 5.x began throwing warnings when servers are using their default self-signed certificates and not a certificate that is issued by a trusted certificate authority such as an internal Microsoft Enterprise CA or a public CA such as GoDaddy, Verisign, etc. I’ve always suggested using a public CA simply because mobile devices don’t natively trust certificates issued by an internal CA and because it’s not a domain joined device, there is really no automated way to place the internal CA’s certificate into the trusted store. With that being said, if you don’t have any mobile or non-domain joined devices in your environment, you can use an internal Microsoft Enterprise CA for your View connection server certificates. The following demonstrates the process:
Upon successfully deploying your View Connection servers (both internal and external), you will noticed that the dashboard lists all of them with an error:
… and clicking on the server object will display the error:
Name: <serverName>
Version: 5.1.2
Status: Server’s certificate does not match the URL.
SSL Certificate: Invalid
Connections: 0
Before I begin demonstrating using a Microsoft Enterprise Root CA to issue the certificates, note that the official VMware View documentation for obtaining SSL certificates can be found in the following URL:
Obtaining SSL Certificates for VMware Horizon View Servers
http://pubs.vmware.com/view-52/index.jsp?topic=%2Fcom.vmware.view.certificates.doc%2FGUID-358E1A54-DDD7-4A76-B9CB-198E0F7F76D4.html
… another old KB article that is more specific to using a Microsoft CA to obtain a certificate can be found here:
Managing SSL Certificates in VMware View 5.1 using an internal Microsoft Certificate Authority (2020913)
http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=2020913
With the location of the official documentation out of the way, the certificate I intend on issuing will contain the common name:
- vdi.domain.com
… and the following SAN entries:
- vdi.domain.internal
- vdi
- svrvmvc01.domain.internal
- svrvmvc01
- svrvmvc02.domain.internal
- svrvmvc02
- svrvmvce01.domain.internal
- svrvmvce01
- svrvmvce02.domain.internal
- svrvmvce02
By requesting a certificate with all of these names, I can simply use one certificate for all of my servers (2 internal and 2 external View connection servers). I get asked a lot about why I like putting the NetBIOS name in certificates any reason is that I’m quite lazy when it comes to typing in the URL for servers as I tend not to use the FQDN in most cases unless my laptop is not a part of the domain or if the DHCP servers do not issue the suffix for a domain. While I can’t speak for others, my guess is that there are probably others like me out there and since we don’t pay extra for having additional SAN entries when issuing certificates from an internal private CA, why not put them in? What’s also important to note is that Certificate Authorities (CAs) have accepted worldwide guideline changes and will no longer issue SAN SSL Certificates that are not in a legitimate FQDN format as of November 2015. I found out about this a few weeks back when trying to issuing a 3 year GoDaddy certificate with NetBIOS names so keep that in mind when planning your certificate.
Begin by logging onto one of your View Connection server, open the MMC console and add the Local Computer store’s Certificate snap-in:
Right click on the Certificates node under Certificates (Local Computer) –> Personal –> Certificates and select All Tasks –> Request New Certificate:
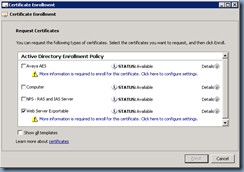
Click on Next:
Select Active Directory Enrollment Policy and click Next:
Note how I have a Web Server Exportable certificate template in the list which is a duplicate of the Web Server template but with the Private Key is Exportable enabled. The reason why this is important is because we will need to export this certificate to other servers so proceed with select the certificate and click on the More information is required to enroll for this certificate. Click here to configure settings. link:
The following Certificate Properties window is where we enter the information required for the certificate:
You don’t necessarily have to fill in all of the attributes but the following are the fields that I usually fill in:
E = tluk@domain.com
CN = vdi.domain.com
OU = IT
O = Company
L = Hamilton
S = Hamilton
C = BM
Adding SAN entries is simply selecting the DNS as the Type under the Alternative name section:
With the Subject tab for the Certificate Properties filled out, proceed with clicking on the General tab and type in vdm as the Friendly name. Note that this field MUST contain vdm or your View connection servers will not use this certificate.
Clicking OK in the window above will complete issuing of the certificate to the server:
With the certificate now in the local computer store, test the certificate by restarting the VMware View Connection Server service:
Log back into the administration console:
Note how the server with the certificate is now labeled with a green square indicating the error is gone:
Note that if you continue to see a red square complaining about the certificate, check the certificate properties and ensure the friendly name has the string vdm:
Now that we’ve confirmed the certificate works, proceed with exporting the certificate with the private key:
Make sure you export the private key:
Export as a PFX file:
Then copy the PFX file to the other VMware View Connection servers and import it:
Restart the services on the server:
Note that it may also be necessary to restart the other servers as well to update the error:
Hope this helps anyone looking for information on using a Microsoft Enterprise CA to issue certificates for VMware View connection servers.










![clip_image001[4] clip_image001[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjOj7-mByfaZgtpiuf1o_-S1_bNx2sAoxiLFRoy7LuaxVpSfX7kTbBG5RUibc9SLatf3Bk6tq-8iV5SVf8hNfURFwVRMPO1a13C0_zSLKMtD_xt8yiq1bM7gtEH5RvC3Xx7h6PFasBM-bFC/?imgmax=800)
![clip_image001[6] clip_image001[6]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhMST78wxmc2tkhmJOR5OdWq9KymmG1C1nobhT30hI475W8gmNQeSF4VDLLiDrb0p7NiZ0KyYGWWx8BlbIHqNlAgRg0kq1ctGDEH-Z9CbHhJazlTvJZVwTCilxtKA3eXpnLgmSd0567WAwe/?imgmax=800)
![clip_image001[8] clip_image001[8]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjs8q4VqNMEBs1vAbr-TzaJYTnfn4qzrGPRiSCMFpBaCjRHJAO2VPvDCqeV4LvqCH6JsTLToOM3Gumjqjf7f1EiBoQtdtMTFxWwQ7TWefTfeAm0HHS3fh_O67mdmlv6KydwJOw-p4xXQlOn/?imgmax=800)




![clip_image001[10] clip_image001[10]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgYk5fg0G1PfLKQ-ESfNJ23u4RPWg8hNIxEzG01ioD-JLihForDDS7cTb4m5y2CPgGATnaEKzas2iXkDlB1VSJAlicLL4unB6Hnn1oTCDsP4iYw2MZOQxQXo1-jju1nS7mXXtNSGtB6TM55/?imgmax=800)
![clip_image001[12] clip_image001[12]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi3UzhRKmsZIMco8sMHSgDALCmMblJYdCchClKs8z2UQdZKNzWQPLn-KznIdlTXxN5jdrUbYBX95DP9lD4EQD5pEOE3FKqlR7N07BRp_BXbKRt07ejFZHZjcMnF3AvdfuVy_HmA8gwCkmjG/?imgmax=800)
![clip_image001[14] clip_image001[14]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhHaTuz9XZ2MKOxlAtNDKQMSv2XZUD7SNmolM54Cpy30unn4bfRRO2rtFqEtraW6ypucJlD6xQxDmpHXg3JeImdCm_A2QoaTwhaULwaNQKl8guWMo9jRHYFAjchtrw4KiGXzPNT2agVABFa/?imgmax=800)
![clip_image001[16] clip_image001[16]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgihweXL9qXaun7ev_SZfgp0G_5is5A8NZlUN24M1CqfvCuAlrwVKVOhHcv4LfsT72C8VgyNtNJJvpTZuaoMswGxyfJ3ESLdK5jbp9J9L51aoMRV-tbPTy6VhjLlGPdUQeBkqDM9v7p7Ob9/?imgmax=800)
![clip_image001[18] clip_image001[18]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEigceg3j1WLjIBFdmgYpGfYgDQ0odw3QYNcjZpAjVThpri08V-i-ktaifpT-lcGNEdbbvY_aUbn1oF6X5tFlFaiMT4dkb0BmsqHAfbZfceYWpFZkHQOmCpdAni1sxR9_39i7AcroqZOxdD9/?imgmax=800)
![clip_image001[20] clip_image001[20]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgeI7jUz2mSIg4WeJCh0tqvx610QR0Gz5brf7dGwYmQggIB2hzV-N4MKJ8uki8LoyAjFUvLuHR8hqNfJI_KBoKGmVQICPkivGWBYh9V00nq170rVtik9rSl91oDMuZtg9qVksS-2x1AbP1Q/?imgmax=800)
![clip_image001[22] clip_image001[22]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjeKgZ89k0zOgZEnGzUiDJfkiOoLGNyKMvpXRyBpl6EmUGf0S5Vj-X40BCO311AGo_RKiacW6O5H1tm1bYH9QUCPq9o0nAlOseIZcLndYuV12ctD53vpoFphSFMAL2KZsS2ADN_7VtOJs50/?imgmax=800)

![clip_image001[24] clip_image001[24]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgXbj2M7G8Hr2D-TAL5sOAbMei-ezdDc4RIRCdaDKFuH7mGaY_bCp2H8IwJY4jdKmIe9mJWY54YPMXUkDvGYN6HnBIhdUpPM6BiF_mi0hqHVXnkWmPhwJPaZH_o2C1P_u_EXrFC1jA-LuMd/?imgmax=800)
![clip_image001[26] clip_image001[26]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjTZTpIozw87LVr8U0tS_afIlZDvWhDZ7JSBHprobwx-1f5o8jnoXcW8QLv4QZSSVhUQCbIdcoiStrFtg5uwvrTgMHCYEnPutAsL6P0acpKvE8DE2cr_1gibnjRVkvvwrvfbRnEs_1sTHgR/?imgmax=800)
![clip_image001[28] clip_image001[28]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiv7rG2BdFORGuSxAstXzD-FuB1tnewXfrpglMdrGqLOhfJ9PWH1gv6rFMwdeJmHDNFMf3phDVL0eUjah9raZiep2S2DnHzIksEVcYkTx8vv_EUQfnjVK_m9SFStBH2xqxlXnTP2LK4kXL4/?imgmax=800)
![clip_image001[30] clip_image001[30]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhCq_JvDA5Jh5BHHOOwcwIba7dsJZnGRlRByum_cuHynQM5xBY19aIxuvcyh2tgnV6gOPpnTbMmpDB6GXAL3xK-nqc3jD5qvsP5nusUhwf0_LOuzlFoBhFQyBcqL9jCObVTdpQS1nJYbCS9/?imgmax=800)
![clip_image001[32] clip_image001[32]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjSMfMxf4P_q6SA69EgVXF7dTDl8UuNqKADXebm4FVKw9Hczi3DijoQ0b899epkY-fQrIVxb5QnJntdfxUmfX1seoPdjZQkA_TgBq_AmAP0rnmi5boJaF0taaTPa3gl1nf1icHjOxnAhxQf/?imgmax=800)
![clip_image001[34] clip_image001[34]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhSoOD15NfQZVES6ipSien26TcZSNTNplnfEvW4x0koo-g_ew3WZJXyBpk5AOCNi9ObTBK2cc-SJNM8ewNQXZTd3poHg5OS0F-9jjq1_xz-iCrzwjJUphakHwVUdEDUQJvMFtBlnBFOu78q/?imgmax=800)
![clip_image001[36] clip_image001[36]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjJmBNEZGhOG8HgShAvy2GNCMTTRYoKOYEhf_eO8CFV73YbH2E0Ol1oeuCiFBfZ9eIlTOx4ytdW_G23PogE31-8mRRXsk4FJRAUeJ83LdJXGPVeTc_Sg_K38P9uZTVad-nG1KhDp6f_bwrZ/?imgmax=800)

![clip_image001[38] clip_image001[38]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEh75BryNlkHVAUJE28RNTxNa7s9pQ7o6jjrab1vbclzJYc-yJv_lzXRot31ZRiDOJQjBNecYmkiAXgBEYqACY3I1hyCSwWp9s1lbVicJWg_U0f13F9OZJwieAg-aoyO9tP5i43-ilWDje8h/?imgmax=800)
![clip_image001[40] clip_image001[40]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhBmng3qfKA6UN4VEDpNc-2MgcfzfT217BdVsMuDomp5ToH30R49UD4FWdsqnuvxZaF4VV1rrKrMGsyc_uBHYSbs84uwiiQQZhAM33aG7WdvdVvbjxexk7oHb-yFyH2AmXXLHVmqp98OSgb/?imgmax=800)
![clip_image001[42] clip_image001[42]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiJJVBmwrB0FLkcpu-dt5PHNdEytpx2EAymB_j3IcnBEHS0Iq7C0ydmGXIL-cTca8831B_X-e6TxGHXKipN14l8j7inGXuhxMJe2-UNJskV95teSStgy9kNHC3-8W_IxFpGD03_nxrByate/?imgmax=800)
7 comments:
thanks a lot
Hi Terence, YOur posts are simply superb. Looks simple but conveys what reader need to know with screenshots.
"I’ve always suggested using a public CA simply because mobile devices don’t natively trust certificates issued by an internal CA and because it’s not a domain joined device, there is really no automated way to place the internal CA’s certificate into the trusted store."
If we use Internal CA certs for view environment and external users try to use View desktop from mobile devices which are not joined to domain, how do they behave. Is it works? DO you see any issues with this approach?
Using an internal CA to generate certificates for external clients that aren't joined to the domain will work if you uncheck the "Do not verify server identity certificates" in the VMware View client "Configure SSL..." options. This is not recommended for obvious reasons so I would recommend using public CA certificates.
Thank you Terence.
I have already installed internal CA certs for Vcenter and it's respective components and I'll request external CA wild card cert for View environment.
Your Post is great, just what i was looking for. The only problem i encounter is the fact i don't have a Web Server Exportable template when the sellection has to be made. Is there a description "how to make Web Server Exportable Template"?
Keep up the good work!!
Thanks for sharing your info. I really appreciate your efforts and I will be waiting for your further write ups thanks once again.
Data Security Information in Bangalore
This is a great post, but doesn't this SAN cert publicly expose your internal server and domain names? I've been trying to find a way to avoid this security risk. Any thoughts?
Post a Comment