I’ve been asked several times in the past about how to block subdirectories when a website is published with a NetScaler and the most recent request was for blocking Exchange Server 2016 /ecp access. As most Exchange administrators are aware, Exchange 2013 and 2016 allows an administrator to manage Exchange via the OWA URL but with the /ecp subdirectory. This isn’t usually a concern when accessed via the internal corporate network but administrators get nervous when it is available via the internet. With this recent request, I thought it would be a good idea use it as an example to demonstrate what the configuration would look like.
**Note that this post is not endorsing the idea to block the ECP URL because I am unsure as to whether Exchange 2016 fully supports this without breaking any features for regular users as it did in Exchange 2013. There has been several forum posts that appear to suggest it is ok but I’ll leave it up to others to decide to do it or not.
Step #1 – Create Pattern Set
Begin by creating a pattern set to match the ecp string with the following command:
add policy patset deny_ecp_url
Alternatively, you can create this via the GUI as well:
AppExpert > Pattern Sets > Add
Open the properties of the newly created Pattern Set, click on the Insert button and create the ecp pattern:
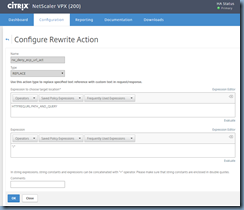
Step #2 – Create Rewrite Action
With the Pattern Set created, proceed with creating a Rewrite Action to replace /ecp with the root with the following command:
add rewrite action rw_deny_ecp_url_act replace HTTP.REQ.URL.PATH_AND_QUERY "\"/\""
Alternatively, you can create this via the GUI as well:
AppExpert > Rewrite > Actions
Type: Replace
Expression to choose target location*: HTTP.REQ.URL.PATH_AND_QUERY
Expression: "/"
Step #3 – Create Rewrite Policy
With the Rewrite Action created, proceed with creating a Rewrite Policy with the previous Rewrite Action assigned via the following command:
add rewrite policy rw_deny_ecp_url_pol "HTTP.REQ.URL.PATH.GET(1).TO_LOWER.EQUALS_ANY(\"deny_ecp_url\")" rw_deny_ecp_url_act
Alternatively, you can create this via the GUI as well:
AppExpert > Rewrite > Policies
Action: rw_deny_ecp_url_act
Undefined-Result Action*: –Global-undefined-result-action
Expression*: HTTP.REQ.URL.PATH.GET(1).TO_LOWER.EQUALS_ANY("deny_ecp_url")
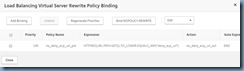
Step #4 – Bind Rewrite Policy to Virtual Server
With the Rewrite Policy created, we can now bind it to the virtual server that publishes the Exchange OWA website via the following command:
bind lb vserver <virtualServerName> -policy rw_deny_ecp_url_pol -priority 100 -gotoPriorityExpression END -type REQUEST
Alternatively, you assign the policy via the GUI as well:
Traffic Management > Load Balancing > Virtual Servers
Bind a new Request Policy to the virtual server:
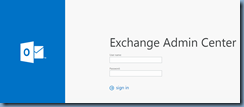
With the new policy binded to the virtual server, any requests to the /ecp directory should redirect the user to the regular OWA login page:
Which means they would never be able to reach this page:











1 comment:
Thank you for this sharing very usefull
Post a Comment