I recently worked with a colleague of mine to get various network devices to use RADIUS authentication provided by a Windows Server 2008 R2 NPS server and realized how many devices lacked documentation on how to configure the NPS server. One of the devices I ended up guessing was a Cisco Wireless LAN controller and seeing how others may come across this, I decided it may be worth while to blog about this. The server I used to install the NPS role was Windows Server 2008 R2 (the configuration would be the same for Windows Server 2012) and the Wireless LAN Controller was the Cisco 4400 Series (4402).
As with setting up RADIUS for other devices, begin by configuring the RADIUS client in the RADIUS Clients node. Note that I am configuring the 2 wireless controller clients with the name CF-<thenSomeName>. The reason why I’ve named it this way will be shown as we go through the setup:
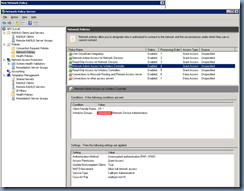
Once the client representing your wireless controllers has been configured, proceed by configuring a new Network Policy:
Policy name – name of your choice
Type of network access server - Unspecified
Click on the Add button in the Conditions window:
Select Windows Groups:
Add the groups you would like to grant administrative access:
Click on OK:
Select Client Friendly Name:
As mentioned earlier, I named all of the devices to start with CF- and this is because you can’t configure the policy to have multiple Client Friendly Names or else in order for the policy to match, the client authenticating would have to match all of the Client Friendly Names. This is of course not possible and that’s why I’ve named the 2 devices to start with CF- so I could use wildcards for the match. For this case, the wildcard to match a name starting with CF- and everything else afterwards is:
CF-.*
**Note that more information about pattern matching syntax can be found here:
Using Pattern-Matching Syntax in NPS
http://technet.microsoft.com/sv-se/library/dd197583(v=ws.10).aspx
Proceed with clicking on Next after you have specified the conditions:
Select Access granted:
Check Unencrypted authentication (PAP, SPAP):
Leave the settings at default and click on the Next button:
Select Standard under RADIUS Attributes and click on the Add button:
Select Service-Type under Attributes and click on the Add button:
Change the Attribute Value from Commonly used for Dial-UP or VPN:
… to Others and depending on what access you would like to give the users authorized by this policy, you can se the value to:
- Administrative <— Full administrator permissions
- NAS Prompt <— View only administrative permissions
- Callback Administrative <— Lobby administrator permissions
Click OK, continue by clicking on the Next button and then click Finish to create the policy:
Notice the new policy created:
Now try logging onto the wireless controller with an Active Directory account:


![clip_image001[4] clip_image001[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEh4lw4D0pEw2Kph2_5-bIPyHOG2QBLXiJPA_10L15T-H7BeWTEDYuTSnZXIuXowzhWO-X8wThRqDx7t-Dlyknx4RPzmaKURgvqX7WMl4ww6z4NkzZP7fVzpX2yDz_sc1C141rOJQ34XcO5K/?imgmax=800)
![clip_image001[6] clip_image001[6]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi0jbtoElrseIGUlfT3zXL5nYbRLWYDw9k6RPtDw3ham9jwPZWD45S4sDWyCe1rwa4Cdo-InueKnebZKjNWHDs1fkMp5j6a0PMaEiYyzpGER0DBMiY-pUajlFQ_LoBITGXYLk5yqky4g7U-/?imgmax=800)
![clip_image001[8] clip_image001[8]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjP4DJcifTY6msLIDbm9FxcKRAc4G2b_xh_EYGYzWYzeXTb4o67SvdW9DunZYd9vLm28kUqXGhdy6KAH9zWl_pYTusqtPCnWvVHB-zaAPe82fWlPj2cV5r-M-yeP_9EtFsBUCHUOmpKVqq9/?imgmax=800)

![clip_image001[12] clip_image001[12]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiwKIbCNRrVOtwH9YGGIG-oazWo0dpI2zs1OzMeTajJ_EYBkL3-2TKb4C69Xrscu1tIuAvELcrTCtNODSUJBT3nwyMHO2Ww8xe7UYGq1efBrP9Oun-cZ7pS5n0cksOLXBO3F2rvWVOsWD1W/?imgmax=800)
![clip_image001[14] clip_image001[14]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjHOouRmUUeIAEoSakPxiok9eL4oUyHjXCoEaW6OOHs4vGLjbkMLwkx5_1RJVw-_SBya4jOgd7npZW2H9m0QBXHoSVCIevrLQOWKgbD8PWRGB50xb8Rwb1pzTbDtIWzu8P1sD9IGeFrFt8X/?imgmax=800)

![clip_image001[16] clip_image001[16]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjZ9YnWulolOi92B8-Mev-7U3txPEF4jQyvAsehohw8TZWiAXQ6ctNdpaZg7m7Kj-EGvuT72Z2BJI1thhI5vljf7DSFUY3etdT3woe8lkoTVHkFABLIsVb0L423Mw5oaHGhN2HZQq1QYf4J/?imgmax=800)
![clip_image001[18] clip_image001[18]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgCT_a0qC4o3JYKRC7EV2jswhongxf182hcOEjkEGsHqfWpGX4Di9sUAf03OWbE5Z4GJaZ3JnMDW54rhSeWAeud6zf2yQkwq2QK98tBuYhyCuH-dD51hyphenhyphen3nZdlsZYzzvKC8SNXX8RXdhmNW/?imgmax=800)
![clip_image001[20] clip_image001[20]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjnSTJfk5XeLZy_Snw8LSOsyAaWAHrUf3erQYWRY1Fi6t0mtdYjudoSzRYjZNB_bVLb2UvrTJvASgKZ_EJ_4NnzXgNAN0i1mHC05zSe6ycbJNyAvKK0eMp2Md5vZ1tTMqGBExMO5yRCwm7X/?imgmax=800)
![clip_image001[24] clip_image001[24]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhIh6idOJNI25HMKphmP06nByZQHQwb5R1zh7CbyS4QS4WQWzsep9iDnFAu3y9G7_6WRsiDG8XP3lWjZevGJNtMo_YDeONtCFDYaY0S4-DaTPv_o4j4ou5mFJJTNcoRJ9H66mk7-bDZ4e7v/?imgmax=800)
![clip_image001[26] clip_image001[26]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg62R2XBCxkXAfHEUCFIRauvuzGupCL5VL3-Y4RZK6nZV3KA-JvrvFtsQhCJp5yxu88vUCt2WjTWI51xJNi_hMhFf1moDCnRU70H9eU_7ecnJb3qtDDymS0K8A-3wEI80XnuQ9xWo9T2ve4/?imgmax=800)
![clip_image001[28] clip_image001[28]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEj_Cd8JzWUUMr7ZfO2yCHzFc3rahJmiLsfzTRpym0fc7XK3OU1fm8XFZBX2LSew0sthIGuoNcZyefrb_DE69Gvv5PqvVQFDS-rfIXkx9Jh0XFZSRo4K7-L7wCN0_v4t2dGsqxU7VC_GrGkW/?imgmax=800)




Very good solution, thanks for sharing your knowledge.
ReplyDeleteHi Terrence, Thanks for the post. Just wanted to see if you have ever or if it's possible to use a wildcard cert for EAP/PEAP authentication in this same scenario you have posted. Thanks.
ReplyDelete