I don’t usually configure NetScaler VPX appliances as this was always left for the networking team when I still lived and worked in Canada. Bermuda, on the other hand, sometimes tend to blur the lines between the networking and systems team where most engineers/consultants would branch off to other realms of technology. I’ve always believed that you can’t really be good at everything and that’s why I tend not to volunteer configuring networking devices such routers and switches even though I know how to because someone else who does it on a regular basis would do a much better job than I would. Also, I think I have yet to meet someone who is extremely fluent with networking to be just as good with server infrastructure. I’m not saying these people don’t exist but I would say they’re very rare. Recently, I had a client tell me that I should stop saying “I don’t configure network devices” and start doing the work as well so clients don’t turn to other consultants which will also allow me to bill more hours and make more money. I wasn’t offended but I made sure I explained to him why it was in the best interest of the client that I didn’t.
Anyways, I think my rant is boring you (the reader) right now so I’ll proceed with demonstrating how to set up a NetScaler VPX to authenticate through proxying between the user on the internet and the backend web servers.
The environment for this example consists of a NetScaler VPX appliance with 2 network interfaces. 1 interface is sitting in the DMZ (172.x.x.x) network and the other leg is sitting in the internal server network (10.x.x.x). A CheckPoint firewall is configured to allow port 443 traffic to be directed to the NetScaler’s 172.x.x.x IP via a public IP. The XML broker is the XenApp servers and the port they’re using is port 80. Finally, the NetScaler has a certificate issued by a public Certificate Authority and is a virtual machine on an ESXi 5.0 host with dvSwitches configured.
Start by configuring your NetScaler’s MIP, SNIP and VIP IPs:
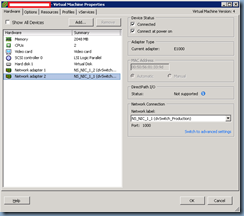
As per the deployment guide for the NetScaler, you’ll need to set up 2 port groups for the NetScaler:
… where 1 interface will be mapped to the port group named:
NS_NIC_1_1
… and the second one named:
NS_NIC_1_2
Note that these port groups must be named exactly as the shown above. I’m not sure why Citrix would hard code this naming convention into their NetScaler VPX’s code but there’s probably a reason I’m not aware about.
I’m not sure if this is consistent with all NetScalers but my mappings are as follows:
NS_NIC_1_2 is mapped to 0/1
NS_NIC_1_1 is mapped to 1/1
I would advise that you do a simple test by disabling one of the port groups to test which vNIC is mapped to which NetScaler interface.
I feel that I need to stress that you ensure your routes on the NetScaler VPX are configured properly as they can cause quite a bit of headache if you don’t:
You have the option of using IPs or DNS Names when referencing your web interface and XenApp servers but as best practice, you should use names so make sure you set up Name Servers on the the NetScaler appliance:
Once you have all of the above set up appropriately, proceed with navigating to Access Gateway –> Virtual Servers:
Right click on the right hand pane and select Add:
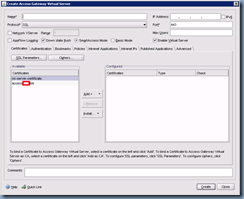
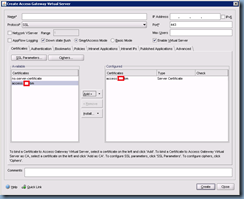
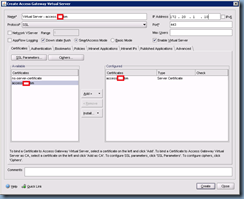
In the Create Access Gateway Virtual Server window’s Certificates tab, select the public certificate you’ve installed and click on the Add button:
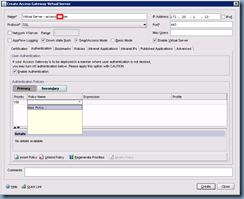
Next, give this virtual server a name and enter the IP address:
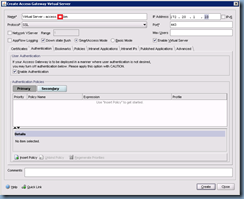
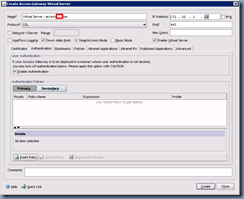
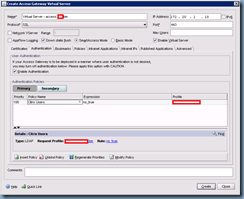
Proceed with clicking on the Authentication tab:
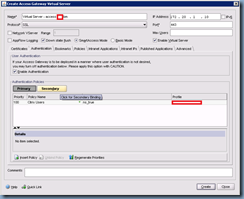
Click on the Insert Policy button at the bottom to create a new policy:
Click on the small drop down box under Policy Name and click on New Policy:
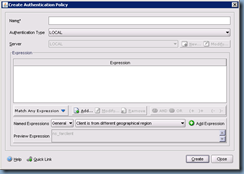
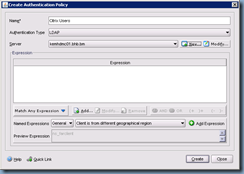
The Create Authentication Policy window is where you select the Authentication Type (i.e. LDAP, RADIUS, etc) and set up Expressions (i.e. TrendMicro installed?) which act as rules you have to check against the client that tries to authenticate against the NetScaler:
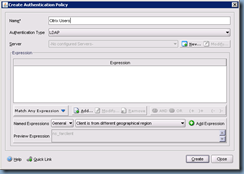
Enter a name for the policy and select LDAP as the Authentication Type and click on the New button:
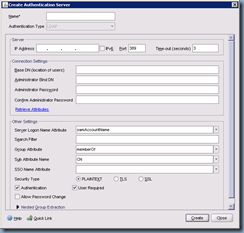
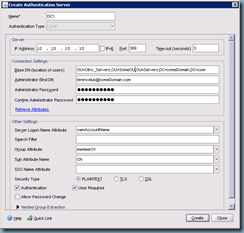
The Create Authentication Server window is where you specify the settings for your LDAP server which will be your Active Directory domain controller:
The following is an example of what you might enter into the settings:
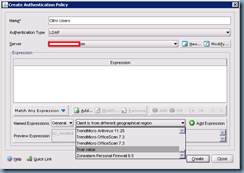
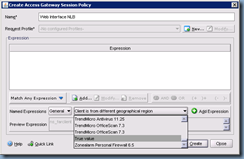
Once you’ve completed entering the information for your LDAP server and exit out, you’ll be brought back to the Create Authentication Policy window. Proceed with adding an Expression by clicking on the drop down menu beside the Add Expression button:
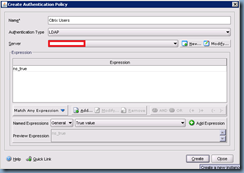
For the purpose of this example, we’re not going to add any special expressions in so we’ll be adding the expression True value which just means all or any client:
Once you’ve added in the expression, proceed with clicking the Create button and Close:
Once you’ve exited out of the previous window, you’ll then be brought back out to the Create Authentication Policy window with the policy you’ve just created shown in the Authentication Policies window:
Note that you should be creating a secondary entry or multiple policies with different priorities to build in some redundancy in case your configured LDAP server becomes unavailable:
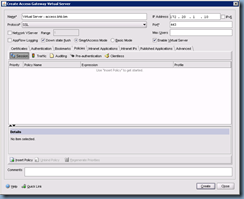
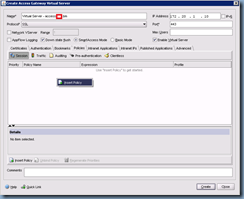
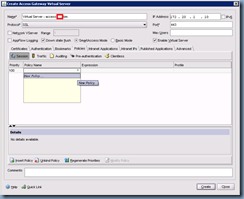
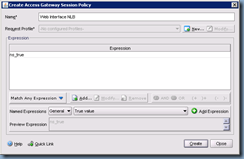
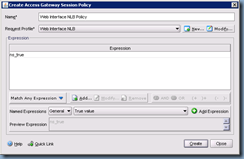
With the authentication policy created, proceed with navigating to the Policies tab to create a new Access Gateway Session Policy:
The configuration options here are pretty much the same as the Authentication Policy settings only in a different context. Here is where we’ll be entering the information for the access gateway to contact the back end web interface servers:
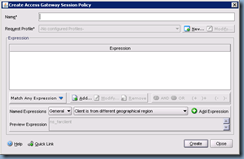
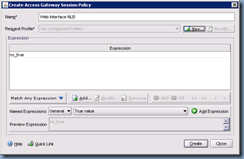
As with the authentication policy, we won’t be putting any special expressions into this policy so we’ll use the True value again:
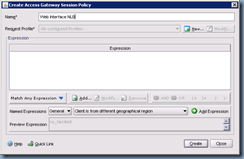
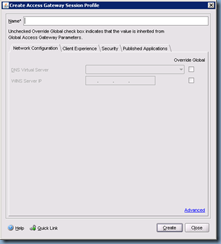
Once we’ve added the expression, proceed with clicking on the New button to bring up the Access Gateway Session Profile settings which will allow us to enter our web interface server settings:
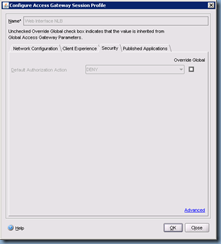
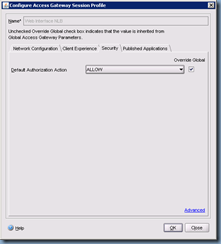
The first tab we’ll be changing is the Security tab where we’ll be setting the Default Authorization Action to ALLOW:
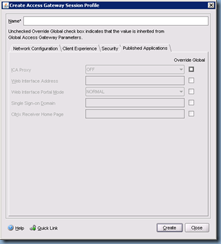
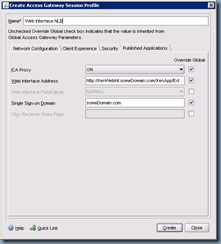
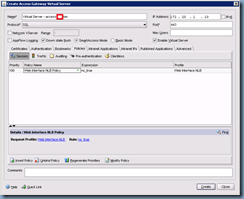
The next tab we’ll need to configure is the Published Applications tab which is where we’ll be entering our web interface servers’ information:
Note that the Web Interface Address should point to a load balanced VIP or virtual name that spreads across multiple web interface servers to provide redundancy.
Once you’ve completed the configuration of the Publish Applications tab, proceed with clicking on the Create and Close button to exit out returning to the Create Access Gateway Session Policy window:
Continue with clicking on the Create and Close button to exit back to the Access Gateway Virtual Server window:
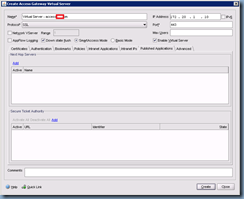
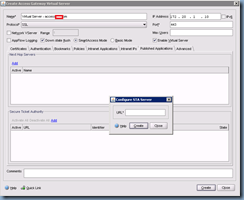
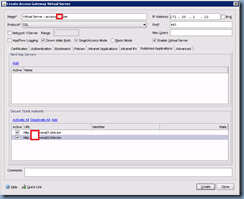
With the access gateway virtual server set up, the next step is to click on the Published Applications tab to list the Secure Ticket Authority (STA) servers. For this example, my STAs are the XenApp servers:
Once you’ve completed entering the STA information, proceed with clicking on Create and then Close.
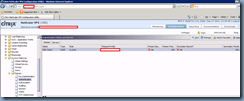
If you’ve configured everything properly, you should see your newly configured virtual server with the State as up:
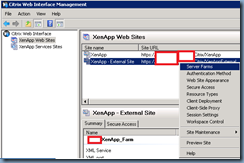
Now that we have our NetScaler set up, we should proceed with configuring an additional site on the web interface server for the NetScaler to access so log onto your web interface server and open up the Citrix Web Interface Management console:
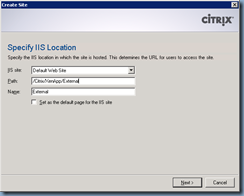
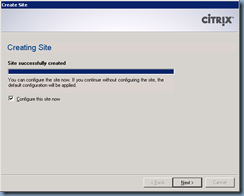
Create a new site:
I never liked the defaults so change them to whatever you see fit:
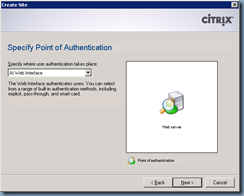
Instead of At Web Interface for the Specify where user authentication takes place:
… change the setting to At Access Gateway:
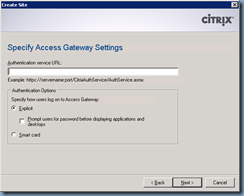
In the Specify Access Gateway Settings window, enter your publicly accessible URL with /CitrixAuthService/AuthService.asmx in the Authentication service URL:
https://access.terenceluk.com/CitrixAuthService/AuthService.asmx
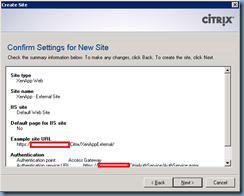
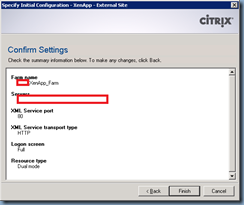
Review the summary tab and proceed with all the information you’ve entered is correct to create the site:
Once the site is created, you will now be able to immediately configure it:
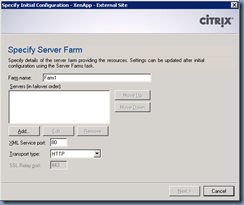
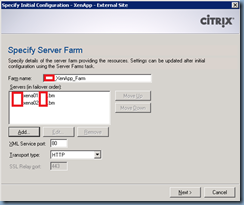
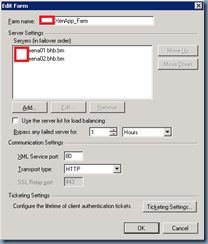
Configure the XenApp or XenDesktop farm that will be servicing the external client:
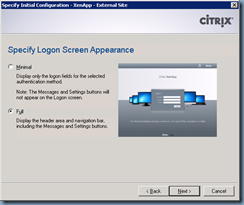
Proceed through the wizard and customize the website as you see fit:
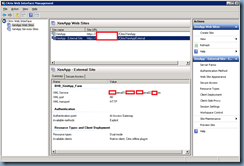
Once the site configuration completes, the Summary tab of the new external site should look something like the following:
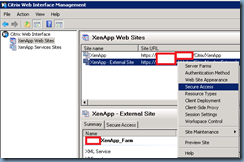
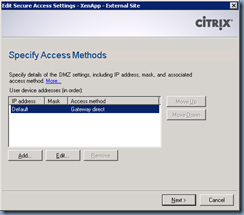
Proceed with right clicking on the external website and select Secure Access:
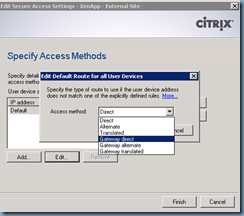
Notice how the Access method is labeled as Direct:
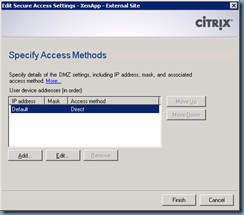
We need to change this setting to Gateway direct:
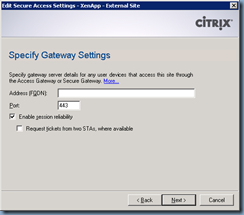
In the Address (FQDN): text field, we need to fill in the public URL our external users will use to access the portal:
access.terenceluk.com
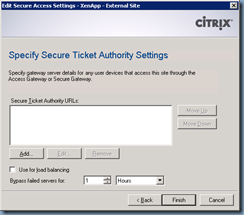
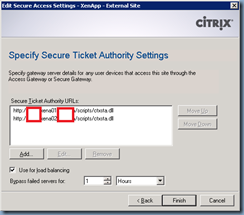
Within the Secure Ticket Authority URLs: window, we need to enter our STAs (the XenApp servers) with the format of:
http://xenapp01.someDomain.com/scripts/ctxsta.dll
Once you’ve completed the Server Access setup, if you have multiple XenApp or XenDesktop servers within the farm, proceed with going into the Server Farms properties to configure the list for load balancing:
… and we’re done. Begin testing the configuration by trying to access the Citrix portal with a computer that’s external to your internal network (on the internet).
Note that all of the configuration we’ve performed on the NetScaler are stored in certain nodes within the administration GUI:
Authentication Policies and Servers
Access Gateway Session Policies and Profiles
There you have it, a quick set up of the NetScaler VPX appliance for publishing your web interface server and applications. Note that I’m in no way a NetScaler expert and what I have demonstrated here is just scratching the surface of what this powerful appliance can do.


10 comments:
Keep up the GREAT work!! Paul C
Can this be set up to not go through a DMZ?
Paul - I had very little Netscaler experience. Eventhough I have a lot of Citrix experience. Your article helped me the most after alot of reading and research I still couldn't get this configured. I never post comments but I had to say THANKS!
Paul - I had very little Netscaler experience. Eventhough I have a lot of Citrix experience. Your article helped me the most after alot of reading and research I still couldn't get this configured. I never post comments but I had to say THANKS!
Your blog has been very helpful in getting things up and going but being new the AG/WI I have a question about the authentication policy with primary and secondary and multiple LDAP servers. Would I add 1 LDAP server as primary and the other LDAP server as secondary or add both to primary and set a weight like 90 for 1 and 100 for the other?
How it be a link to connect to xenapp via netscaler?
I try
https://virtualserver-name.domain.com and it redirect me to https://virtualserver-name.domain.com/vpn/index.html?
I noticed when I create the VIP under Access Gateway -> Server it does not have an area to input the correct subnet.
When I tried to add a route for my VIP. I keep getting the message: "Error: The gateway is not directly reachable"
Excellent work, I found where I was going wrong. Thanks a million for explaingin with screen shots
I haven't work before on Netscaler. But after reading your post i will definitely try this. I like networking concept and doing desktop sharing and other small level networking at my own.
Read more: http://www.portsys.com/index.php/products
Very nice article. A big thank you to you!
I am also new to working with CAG because these are in actual fact networking devices. I have mostly worked with only Secure Gateway which is and used to be a Server application for enabling Citrix SSL VPN access. Inevitably Citrix are moving everything to Netscaler. So recently I forced myself to do some self learning.
I have setup it up on my laptop using VMPlayer and added a 3 legged router/firewall to the mix. But I have come unstuck and don't know if what I am doing is a supported netscaler configuration.
My basic setup is as below:
NSIP 192.168.10.10
SNIP 192.168.10.11
VIP (External WAN) 192.168.10.11
The 192.168.10.0 network is my DMZ
My DC/Xenapp/WI servers live in my private LAN 192.168.199.0 network.
I have opened various ports to enable the flow of traffic for LDAP,Management/STA/XML/ICA but for some reason the SNIP (192.168.10.11) just cannot route packets to the Private LAN 192.168.199.0 network.
Comparing various guides I noted that both the NSIP and SNIP/MIP are always on the same network subnet. Is this the defacto??
Any advice will be greatly appreciated.
Thanks
Mike
M
Post a Comment